Crypto Ransomware Seeks Dominance as New Threats Emerge to Encrypt and Destroy Files
 Ransomware threats have been a major nuisance for a couple years now. At one time, the prevailing ransomware threats were limited to ones that exploited law enforcement agencies across the globe threatening computer users with a misrepresentation of an authority that supposedly detected illegal activities. In the latest discoveries and detections of ransomware threats, the authors are seeking dominance in the malware world as the threats have a newfound commonality that involves an aggressive approach of encrypting files on an infected computer.
Ransomware threats have been a major nuisance for a couple years now. At one time, the prevailing ransomware threats were limited to ones that exploited law enforcement agencies across the globe threatening computer users with a misrepresentation of an authority that supposedly detected illegal activities. In the latest discoveries and detections of ransomware threats, the authors are seeking dominance in the malware world as the threats have a newfound commonality that involves an aggressive approach of encrypting files on an infected computer.
Crypto Ransomware threats first emerged on the scene about two years ago where the specific threat CryptoLocker was an initiator for this new type of malware. We were one of the first to blog about CryptoLocker providing exclusive removal processes and technical information about this new type of threat. At the time, not much was known about Crypto Ransomware threats. Though, the sight of a ransomware message on the screen of a Windows PC was nothing new and most shrugged it off as another FBI or Police Ransomware threat that was virtually harmless to files and applications stored on the infected computer.
Unfortunately, threats like CryptoLocker and other Crypto Ransomware types took their infection to a whole new level by manipulating files through encryption, which would cause irreversible damage in some instances.
Among recent Crypto Ransomware types, there is a short list of threats that stand out among others as they have been the most destructive and proven to be the most difficult to remove from an infected computer. Starting with CrytoLocker, it was one of the first at ground zero for Crypto Ransomware threats.
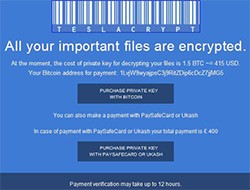
Following CryptoLocker there was a rash of threats that were virtually identical to CryptoLocker, such as CryptoWall, CTB-Locker (Critoni), BitCryptor, CrypVault, KRIPTOVOR, VaultCrypt, TeslaCrypt, and the recent 'Los Pollos Hermanos' threat that thrives on its crafty name the draw attention, but is actually the name of an older TV show "Los Pollos Hermanos" (The Chicken Brues).
Hackers are undoubtedly clever in their actions, and sometimes we find humor in some of the names they conjure up for their malware threats. What isn't funny is the utter destruction caused by these recent Crypto Ransomware threats. Many of them end up in a game of chance or a flip of a coin where heads means you are able to obtain an antispyware program to remove the threat before it damages your files, or tails would be a dire situation where the threat encrypts so many files on your computer that you must format the hard drive and start over by reinstalling Windows and your applications.
Looking at the ultimate objective of hackers and cybercrooks who create and distribute Crypto Ransomware, the details are plastered directly on the threat messages that the malware displays. It is all about money, always has been and probably always will be.
Most of the Crypto Ransomware threats will display a deceptive message claiming that your files have been encrypted, which is true in most cases that we have examined with such threats. From there, the message gives you an option to decrypt those files through obtaining a decryption key that will cost anywhere between $100 to over $1000. Dependent on the location of the infected system, the Crypto Ransomware may convert the money into the proper currency. The threat will give victimized computer users a choice of making the payment through a type of e-payment system, mostly Bitcoin payments or via PayPal or similar avenues. For those who do pay up the fee, they may or may not receive the encryption key. For those that do receive a decryption key, they are able to restore their files in most cases. In some rare instances, computer users must take other steps to utilize their purchased decryption key, which may be followed by other offers to extort additional funds.
As we continue to stay abreast of the newest Crypto Ransomware threats, computer users must know that prompt action taken to detect and remove such threats will be the key to resolving the issue without losing important files or data. The encryption process conducted by Crypto Ransomware threats may be limited upon quick removal of those threats. This is why it is essential always to keep an updated and running copy of a trusted antispyware application on your computer at all times.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.