CNN Alerts: My Custom Alert
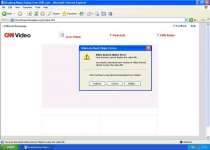 "CNN Alerts: My Custom Alert" is the new spam email that follows CNN.com Daily Top 10 in the malicious tactic to deceive users into downloading trojans like Zlob, Vundo or Trojan-Downloader.Agent.EL. "CNN Alerts: My Custom Alert" and "CNN.com Daily Top 10" are malspam emails created by hackers that appear to look like CNN alert emails when, in fact, all it contains are links that point to rogue websites, where a screen will pop up to inform the user that the Flash player needs to be updated. Once you download the fake Flash player, it will download a trojan onto your computer.
"CNN Alerts: My Custom Alert" is the new spam email that follows CNN.com Daily Top 10 in the malicious tactic to deceive users into downloading trojans like Zlob, Vundo or Trojan-Downloader.Agent.EL. "CNN Alerts: My Custom Alert" and "CNN.com Daily Top 10" are malspam emails created by hackers that appear to look like CNN alert emails when, in fact, all it contains are links that point to rogue websites, where a screen will pop up to inform the user that the Flash player needs to be updated. Once you download the fake Flash player, it will download a trojan onto your computer.
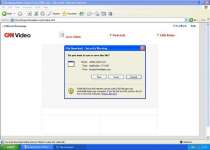
If you receive an email with the subject "CNN Alerts: My Custom Alert", do not be tricked into opening it and clicking on the links provided. "CNN Alerts: My Custom Alert" is supposed to contain relevant CNN story links such as "Chinese Islamic group threatens Olympics", which should redirect to a legitimate CNN story. However, you may find a message embedded within the image of the "CNN Alerts: My Custom Alert" email that links to the "FULL STORY" which redirects you to biogazrhonealpes.org/cnnplus.html, a rogue website. Another rogue website you may redirected to is sarlcreapub.fr/cnntop.html that pops up the error message "Video ActiveX Object Error. Your browser cannot play this video file.".
If you download the fake video codec to watch the video, you'll actually install a Trojan on your machine. CNN Alerts: My Custom Alert may modify your Windows Registry. CNN Alerts: My Custom Alert's fraudulent activities may cause a flood of popups and fake system alert messages. Ultimately, the trojan installed on your computer will display fake warning messages to push rogue anti-spyware programs such as Antivirus XP 2008.
File System Modifications
- The following files were created in the system:
# File Name 1 c:\Program Files\rhcnkrj0etfg\MFC71.dll 2 c:\Program Files\rhcnkrj0etfg\mfc71enu.dll 3 c:\Program Files\rhcnkrj0etfg\msvcp71.dll 4 c:\Program Files\rhcnkrj0etfg\msvcr71.dll 5 c:\Program Files\rhcnkrj0etfg\rhcnkrj0etfg.exe 6 c:\Program Files\rhcnkrj0etfg\Uninstall.exe 7 c:\WINDOWS\system32\CbEvtSvc.exe 8 c:\WINDOWS\system32\lphcjkrj0etfg.exe 9 c:\WINDOWS\system32\pphcjkrj0etfg.exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{RegistryKeys}c:\Documents and Settings\All Users\Desktop\Antivirus XP 2008.lnkc:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008c:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008.lnkc:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\Antivirus XP 2008.lnkc:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\How to Register Antivirus XP 2008.lnkc:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\License Agreement.lnkc:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\Register Antivirus XP 2008.lnkc:\Documents and Settings\All Users\Start Menu\Programs\Antivirus XP 2008\Uninstall.lnkc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfgc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantinec:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Autorunc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Autorun\HKCUc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Autorun\HKCU\RunOncec:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Autorun\HKLMc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Autorun\HKLM\RunOncec:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Autorun\StartMenuAllUsersc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Autorun\StartMenuCurrentUserc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\BrowserObjectsc:\Documents and Settings\LocalService\Application Data\rhcnkrj0etfg\Quarantine\Packagesc:\Program Files\rhcnkrj0etfgc:\Program Files\rhcnkrj0etfg\database.datc:\Program Files\rhcnkrj0etfg\license.txtc:\Program Files\rhcnkrj0etfg\rhcnkrj0etfg.exe.localc:\WINDOWS\system32\blphcjkrj0etfg.scrc:\WINDOWS\system32\drivers\54c70b2e.sysc:\WINDOWS\system32\phcjkrj0etfg.bmp
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.