Windows Attacks Preventor
Posted: March 2, 2012
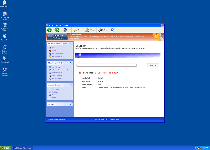
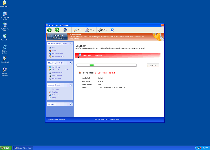
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 6 |
| First Seen: | March 2, 2012 |
|---|---|
| OS(es) Affected: | Windows |
 Windows Attacks Preventor may have mastered the outer looks of an anti-malware scanner, but with regards to its actual features, Windows Attacks Preventor is no better than a Trojan or virus, and alerts and scan results from Windows Attacks Preventor are always inaccurate. Since Windows Attacks Preventor doesn't have any real security features, Windows Attacks Preventor creates fake threat information to persuade you to spend money in a fraudulent registration process – a process that SpywareRemove.com malware researchers discourage in favor of deleting Windows Attacks Preventor with a system scan from legitimate anti-malware software. As a rogue anti-virus scanner with plenty of tricks up its sleeve, Windows Attacks Preventor may also be a source of web-browsing redirect attacks or malfunctions in your security software until Windows Attacks Preventor is completely removed.
Windows Attacks Preventor may have mastered the outer looks of an anti-malware scanner, but with regards to its actual features, Windows Attacks Preventor is no better than a Trojan or virus, and alerts and scan results from Windows Attacks Preventor are always inaccurate. Since Windows Attacks Preventor doesn't have any real security features, Windows Attacks Preventor creates fake threat information to persuade you to spend money in a fraudulent registration process – a process that SpywareRemove.com malware researchers discourage in favor of deleting Windows Attacks Preventor with a system scan from legitimate anti-malware software. As a rogue anti-virus scanner with plenty of tricks up its sleeve, Windows Attacks Preventor may also be a source of web-browsing redirect attacks or malfunctions in your security software until Windows Attacks Preventor is completely removed.
Windows Attacks Preventor: A Fraud That's Newly Stamped Out from an Oft-Used Mold
Windows Attacks Preventor markets itself as an independent and reputable product that can guard your PC against phishing attacks and other PC threats, but SpywareRemove.com malware analysts have lined Windows Attacks Preventor up as just another clone from the WinWeb Security family of fake anti-virus scanners. As if its misspelled name weren't enough, Windows Attacks Preventor is visually identical to well-known PC threats like Antivirus Security, System Security, AntiSpyware Pro 2009, Total Security, Total Security 2009, Security Tool, Trojan.RogueAV.a.gen, System Adware Scanner 2010, FakeAlert-KW.e, Advanced Security Tool 2010, System Tool 2011, MS Removal Tool, Antivirus Center, Security Shield, Personal Shield Pro, Advanced PC Shield 2012, Security Sphere 2012 and Futurro Antivirus. Infection vectors such as Trojan droppers that are capable of installing Windows Attacks Preventor may also install related PC threats from the same family, and you should scan your entire computer while removing Windows Attacks Preventor to make sure that fresh attacks from the same sources will not reoccur.
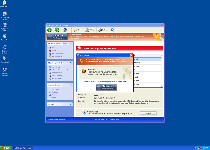
Many of Windows Attacks Preventor's fake alerts and other pop-ups are also borrowed from previous members of its family, and, as such, are completely ignorable as sources of information on PC threats or other issues that may be troubling your computer. Since Windows Attacks Preventor is unable to detect legitimate problems with your PC, viruses and other threats that Windows Attacks Preventor digs up are all illusionary issues that Windows Attacks Preventor creates to deceive you with messages like the following:
Error
Software without a digital signature detected.
Your system files are at risk. We strongly advise you to activate your protection.
Security Center Alert
To help protect your computer, Security Center has blocked some features of this program.
Name: Win64.BIT.Looker.exe
Risk: High
System warning
No real-time malware, spyware and virus protection was found. Click here to activate.
Error
Software without a digital signature detected.
Your system files are at risk. We strongly advise you to activate your protection.
Error
Attempt to run a potentially dangerous script detected.
Full system is highly recommended.
Warning! Virus Detected
Threat detected: FTP Server
Infected file: C:\Windows\System32\dllcache\wmpshell.dll
Overcoming Windows Attacks Preventor's Passive-Aggressive 'Security'
Because Windows Attacks Preventor will launch itself automatically and avoid being closed or removed by normal methods, you'll also be under attack by other Windows Attacks Preventor-related functions besides its pop-ups and system scans – without any obvious way to turn them off. SpywareRemove.com malware research team recommends that you combat the symptoms noted below by booting from a USB device or switching to Safe Mode (to suggest two common methods of disabling Windows Attacks Preventor) before you remove Windows Attacks Preventor with an appropriate anti-malware program.
Other symptoms that can be a result of a Windows Attacks Preventor infection include:
- Browser redirect attacks. Redirects may display fake warning screens, block your ability to access certain websites, change your search results or redirect you to Windows Attacks Preventor's own site.
- Problems accessing Windows utilities such as the Registry Editor or Task Manager that are replaced by fake Windows Attacks Preventor features.
- Problems accessing other programs, which Windows Attacks Preventor may block under the pretense that they're infected.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-grd.exe
File name: Protector-grd.exeSize: 1.89 MB (1894912 bytes)
MD5: d8bd1894b3f5ad2daf8499a6136f2c98
Detection count: 18
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: March 2, 2012
%CommonStartMenu%\Programs\Windows Attacks Preventor.lnk
File name: %CommonStartMenu%\Programs\Windows Attacks Preventor.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Desktop%\Windows Attacks Preventor.lnk
File name: %Desktop%\Windows Attacks Preventor.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\Protector-<RANDOM 3 CHARACTERS>.exe
File name: %AppData%\Protector-<RANDOM 3 CHARACTERS>.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = 2012-3-1_2HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "fneqtdmtpi"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\symtray.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windows Police Pro.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mmod.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\oasrv.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashCnsnt.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avxmonitor9x.exe
Additional Information
| # | Message |
|---|---|
| 1 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
| 3 | Warning! Virus Detected Threat detected: FTP Server Infected file: C:\Windows\System32\dllcache\wmpshell.dll |



1) dunno2) get antivirus sorfwate. Good one. Like avira, kaspersky, ect.3) get good AV sorfwate4) All you needed was cheap antivirus sorfwate that will protect you from other crap aswellAVS doesnt always do the trick but 95% of the time it will.