Windows Cleaning Toolkit
Posted: November 26, 2013
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 16 |
| First Seen: | November 26, 2013 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
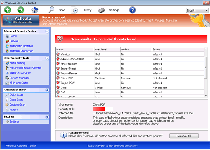 Windows Cleaning Toolkit is a rogue anti-malware program that pretends to detect PC threats, but actually generates intentionally inaccurate scan results to make you purchase its fake software. Windows Cleaning Toolkit steadfastly provides fraudulent system information and may engage in attacks including browser hijacking and blocking other products, and, as a consequence, is classified as malware. As far as malware experts are concerned, disabling and deleting Windows Cleaning Toolkit with any anti-malware strategies and software required is essentially necessary for keeping your PC safe from further harm, regardless of whether it comes from Windows Cleaning Toolkit or related threatening software.
Windows Cleaning Toolkit is a rogue anti-malware program that pretends to detect PC threats, but actually generates intentionally inaccurate scan results to make you purchase its fake software. Windows Cleaning Toolkit steadfastly provides fraudulent system information and may engage in attacks including browser hijacking and blocking other products, and, as a consequence, is classified as malware. As far as malware experts are concerned, disabling and deleting Windows Cleaning Toolkit with any anti-malware strategies and software required is essentially necessary for keeping your PC safe from further harm, regardless of whether it comes from Windows Cleaning Toolkit or related threatening software.
Why this Toolkit Has Bad Advice in Its Bag
Like other fake system optimizers and rogue anti-malware products, Windows Cleaning Toolkit is carefully-designed to look just like an actual system-scanning utility, but doesn't have any of the real features of one. Current evidence gathered by malware analysts has led to the indication of Windows Cleaning Toolkit most likely being a part of the FakeVimes family, which includes many other brand name variants of similar scamware. Some examples of all of Windows Cleaning Toolkit's relatives engaging in similarly fraudulent misbehavior can include Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.
Although misleading system scans and a range of different fake alerts are the foremost functions of Windows Cleaning Toolkit's attempt at fraud, malware experts also have seen many other attacks originate with this family – all for the purpose of making you spend money on non-functional anti-malware software. Examples of the most significant of these are as follows:
- Modifications to the Windows Security Center for the purpose of promoting Windows Cleaning Toolkit.
- Hijacking your browser to redirect you to fake warning pages.
- Hijacking your Web searches.
- Reducing Internet Explorer's security settings to allow Web-based PC threats to attack more easily than usual (through risky downloads, script exploits, etc).
- Blocking other programs by forcing svchost.exe (a normal Windows component) to launch instead of an unrelated program.
Cleaning Up After a Windows Cleaning Toolkit's Infection
Clearly, Windows Cleaning Toolkit is an abject danger to your PC and certainly doesn't warrant any money being spent for keeping Windows Cleaning Toolkit on your computer. However, Windows Cleaning Toolkit's ability to block other applications naturally leads to obstacles in removing Windows Cleaning Toolkit from your PC – even before taking into account the fact that malware experts often see FakeVimes-based scamware distributed by related threats, such as Trojan downloaders. Try to disable Windows Cleaning Toolkit through the use of Safe Mode or other basic security techniques before you begin removing Windows Cleaning Toolkit, which will require unrestricted access to appropriate security software.
Since Windows Cleaning Toolkit is a threatening program that will do its best to prevent itself from being removed, manual deletion of Windows Cleaning Toolkit isn't recommended. For an easier and more all-encompassing solution than removing Windows Cleaning Toolkit unassisted, malware researchers would encourage using anti-malware tools to scan your entire PC. Doing so, hopefully, will detect both Windows Cleaning Toolkit and any other threats that may be responsible for its being installed.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:result1.db
File name: result1.dbSize: 2.37 KB (2372 bytes)
MD5: 4ea5af257d1ceb7daea8725d0db6996f
Detection count: 86
Mime Type: unknown/db
Group: Malware file
Last Updated: November 27, 2013
%APPDATA%\guard-khxd.exe
File name: guard-khxd.exeSize: 1.18 MB (1184448 bytes)
MD5: 991fa9637ce83f45a0e2c01088d1d469
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
%AppData%\results1.db
File name: %AppData%\results1.dbMime Type: unknown/db
Group: Malware file
%AppData%\guard-fvtb.exe
File name: %AppData%\guard-fvtb.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "GuardSoftware" = "%AppData%\guard-toiy.exe"HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell"="C:\\Users\\User\\AppData\\Roaming\\guard-fvtb.exe""LowRiskFileTypes"=".zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.mHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger"="svchost.exe"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger"="svchost.exe"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation"=1HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings
Additional Information
| # | Message |
|---|---|
| 1 | Error Attempt to run a potentially dangerous script detected. Full system scan is highly recommended. |
| 2 | Error System data security is at risk! To prevent potential PC errors, run a full system scan. |
| 3 | Error Trojan activity detected. System data security is at risk. It is recommended to activate protection and run a full system scan. |
| 4 | Firewall has blocked a program from accessing the Internet c:\program files\internet explorer\iexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
| 5 | Torrent Alert Recommended: Please use secure encrypted protocol for torrent links. Torrent link detected! Receiving this notification means that you have violated: - the copyright laws. Using Torrent for downloading movies and licensed software shall be prosecuted and you may be sued for cybercrime and break of law under the SOPA legislation. |
| 6 | Warning! Identity theft attempt detected Hidden connection IP: xx.xxx.xxx.xxx Target: Microsoft Corporation keys Your IP: 127.0.0.1 |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.