Windows Defence Master
Posted: March 15, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 16 |
| First Seen: | March 15, 2014 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
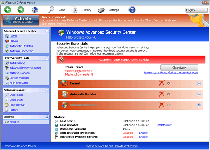
 Windows Defence Master is a fake anti-malware program designed to create false impressions of the presence of a variety of high-level threats, while also including direct attacks against your PC that Windows Defence Master then blames on these threats. Without any real security features to buy, there should be no question that Windows Defence Master isn't worth your money, but malware researchers have connected Windows Defence Master to previous scamware families that are able to threaten your PC's overall state of security. Accordingly, you should rush to disable and then uninstall Windows Defence Master with suitable anti-malware utilities and strategies, just as you'd do with any Trojan, rootkit or another form of threat.
Windows Defence Master is a fake anti-malware program designed to create false impressions of the presence of a variety of high-level threats, while also including direct attacks against your PC that Windows Defence Master then blames on these threats. Without any real security features to buy, there should be no question that Windows Defence Master isn't worth your money, but malware researchers have connected Windows Defence Master to previous scamware families that are able to threaten your PC's overall state of security. Accordingly, you should rush to disable and then uninstall Windows Defence Master with suitable anti-malware utilities and strategies, just as you'd do with any Trojan, rootkit or another form of threat.
The Master Who Takes Away Your PC's Defenses
Windows Defence Master, possibly targeted at the United Kingdom (due to its British spelling preference) is a fraudulent security product that malware researchers have linked to such an infamous family of scamware as FakeVimes, although Windows Defence Master also bears some resemblance to at least one branch of FakePAV and NameChanger. As with the members of any of these families, Windows Defence Master's specialty is faking system pop-up announcements, which will announce that your PC has been compromised by various forms of threats from multiple directions. Common complaints faked through Windows Defence Master include a compromised Registry, the presence of information-stealing spyware and/or a compromised firewall.
Besides faking its security features through pop-ups and system scans, Windows Defence Master also is a danger to your PC in other ways that don't require you to be misled about its real intentions. Windows Defence Master has shown the ability to block other applications, which may lead to other PC security problems while you find yourself unable to access everything from your preferred Web browser to the Windows Task Manager. In some cases, Windows Defence Master even may modify the Registry to allow itself to launch instead of the intended program.
Ditching the Windows 'Defence' that isn't Helping Your Computer
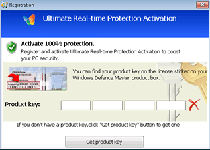
The centerpiece of Windows Defence Master's tactic is its request that you spend real money on purchasing Windows Defence Master, which Windows Defence Master says will allow Windows Defence Master to remove the (fake) threats that it's detected. Instead of spending good money after nothing in return, you should consider restarting your PC through a USB-loaded backup OS. Windows Defence Master's automatic startup routine has been found to have no defense to this security procedure, which will allow you to remove Windows Defence Master freely with the real anti-malware tools of your choice.
Windows Defence Master and clones of Windows Defence Master use compromised advertisement networks and corrupted websites to load the scripts that install them automatically. Be suspicious of any website or pop-up that tells you that it's scanned your PC for threats without requesting your permission beforehand. Malware experts also point to the frequent name changes in scamware, which may make it difficult to identify them by name alone. Fortunately, Windows Defence Master has a close visual resemblance to other FakeVimes entities, such as Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.


Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\svc-rpjx.exe
File name: svc-rpjx.exeSize: 1.07 MB (1072640 bytes)
MD5: 18f5ab40c8d56cb4b0551c26a6c17ae9
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
%AppData%\data.sec
File name: %AppData%\data.secMime Type: unknown/sec
Group: Malware file
%AppData%\svc-[RANDOM].exe
File name: %AppData%\svc-[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%UserProfile%\Desktop\Windows Defence Master.lnk
File name: %UserProfile%\Desktop\Windows Defence Master.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%AllUsersProfile%\Start Menu\Programs\Windows Defence Master.lnk
File name: %AllUsersProfile%\Start Menu\Programs\Windows Defence Master.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\bckd "ImagePath" = "22.sys"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = ".zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = "1"HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = "%AppData%\svc-[RANDOM].exe"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = "0"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = "0"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = "0"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableVirtualization" = "0"HKEY..\..\..\..{RegistryKeys}HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "S_SC" = %AppData%\svc-[RANDOM].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "MS-SEC" = %AppData%\svc-[RANDOM].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "ZSFT" = %AppData%\svc-[RANDOM].exe
Additional Information
| # | Message |
|---|---|
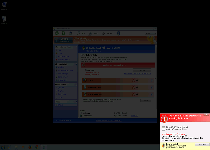
| 1 | Error
Potential malware detected. It is recommended to activate the protection and perform a thorough system scan to remove the malware. |
| 2 | Error
Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
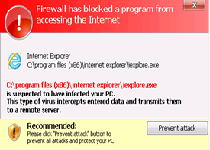
| 3 | Firewall has blocked a program from accessing the Internet
Microsoft DirectPlay8 Modem Provider C:\Windows\system32\dpnmodem.dll C:\Windows\system32\dpnmodem.dll is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.