Windows Health Keeper
Posted: March 17, 2012
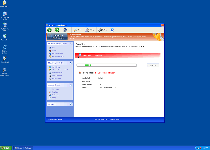
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 39 |
| First Seen: | March 18, 2012 |
|---|---|
| OS(es) Affected: | Windows |
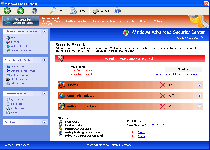 Windows Health Keeper hails from the same Win32/FakeVimes group of fake anti-virus products. A typical Windows Health Keeper infection will also include additional attacks besides those that fake Windows Health Keeper's security features. SpywareRemove.com malware analysts rate the following functions of Windows Health Keeper as being more dangerous than its above characteristics, and mandate Windows Health Keeper's immediate removal as soon as you notice Windows Health Keeper:
Windows Health Keeper hails from the same Win32/FakeVimes group of fake anti-virus products. A typical Windows Health Keeper infection will also include additional attacks besides those that fake Windows Health Keeper's security features. SpywareRemove.com malware analysts rate the following functions of Windows Health Keeper as being more dangerous than its above characteristics, and mandate Windows Health Keeper's immediate removal as soon as you notice Windows Health Keeper:
- Your system settings may be changed to allow Windows Health Keeper to hijack your browser. Hijacks can include changing your homepage, changing your search engine, restricting access to security sites or promoting dangerous sites.
- Your anti-malware and security programs may be blocked, along with fake error messages that indicate that this is supposedly for your own good because of application damage or infection. By using a Safe Mode boot or similar methods to disable Windows Health Keeper, you regain usage of your anti-malware programs, which SpywareRemove.com malware researchers recommend for deleting Windows Health Keeper.
Identifying the Cracks in Windows Health Keeper's Red-Alert Diagnosis
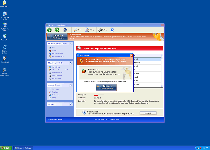
After its installation (typically by a Trojan, a fake online scanner or a drive-by-download attack), Windows Health Keeper launches itself without your permission whenever Windows starts. This allows Windows Health Keeper to display a constant flow of inaccurate warning messages alongside its self-contained 'system scans' that actually don't scan your PC in the first place. Even though warning messages from Windows Health Keeper may appear to be technical and contain drastic warnings, SpywareRemove.com malware researchers have solidly confirmed Windows Health Keeper's inability to provide legitimate threat alerts or system analyses. Instead, you'll find that you're looking at fake warnings like the following examples:
Security Center Alert
To help protect your computer, Security Center has blocked some features of this program.
Name: Win64.BIT.Looker.exe
Risk: High
ERROR MESSAGE:
Warning
Warning! Virus detected
Threat Detected: Trojan-Spy.HTML.Sunfraud.a
Error
Software without a digital signature detected.
Your system files are at risk. We strongly advise you to activate your protection.
Error
Attempt to run a potentially dangerous script detected.
Full system is highly recommended.
System warning
No real-time malware, spyware and virus protection was found. Click here to activate.
WARNING! 371 threats detected
Detected malicious programs can damage your computer and compromise your privacy. It’s strongly recommended to remove them immediately [sic]!
Potential risks: Infecting other computers on your network
Continue unprotected Remove all threats now
Warning! Virus Detected
Threat detected: FTP Server
Infected file: C:\Windows\System32\dllcache\wmpshell.dll
Warning! Identity theft attempt detected
Hidden connection IP: 128.154.26.11
Target: Microsoft Corporation keys
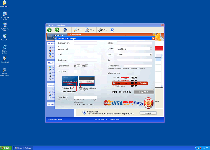
Ignoring these warnings will not cause any harm to come to your PC, since Windows Health Keeper's real goal is to bludgeon you with hoax alerts until give up and spend money on the (equally worthless) 'complete' version of its software. The infamous FakeVimes also gave the world Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security. Instead of spending your money on a product that can't do anything that Windows Health Keeper advertises, it is recommended by SpywareRemove.com malware research that you treat Windows Health Keeper like any other PC threat and remove Windows Health Keeper with real security software. However, you may also need to use added security measures to stop Windows Health Keeper from starting before you can delete Windows Health Keeper completely.



Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\Protector-[RANDOM 3 CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM 3 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%Desktop%\Windows Health Keeper.lnk
File name: %Desktop%\Windows Health Keeper.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%CommonStartMenu%\Programs\Windows Health Keeper.lnk
File name: %CommonStartMenu%\Programs\Windows Health Keeper.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "rnkkhbcsqe"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-3-17_2"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net"HKEY..\..\..\..{Subkeys}HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nwservice.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rapapp.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avwinnt.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashAvast.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fih32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mgavrtcl.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sweep95.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winav.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
need to find out how to remove this windows health