Windows Protection Unit
Posted: April 16, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 4,072 |
|---|---|
| Threat Level: | 2/10 |
| Infected PCs: | 21,372 |
| First Seen: | April 16, 2012 |
|---|---|
| Last Seen: | October 16, 2023 |
| OS(es) Affected: | Windows |
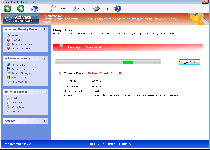 In keeping with its predecessors, Windows Protection Unit will display the same fake alerts, inaccurate scans and other types of fraudulent security information to make it appear as though your PC is under attack by countless threats. Since Windows Protection Unit isn't able to detect or remove any type of genuine PC threat that could endanger your computer, SpywareRemove.com malware researchers discourage any interaction with Windows Protection Unit other than faking its registration (if necessary) and removing Windows Protection Unit with a real anti-malware application. As a rogue anti-virus product, Windows Protection Unit's sole goal is to steal money and related information in its fraudulent registration process, and purchasing Windows Protection Unit or taking its recommendations to heart is never an action that's in your best interests. Windows Protection Unit is a rubber-stamped clone of other scamware programs from FakeVimes, such as Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.
In keeping with its predecessors, Windows Protection Unit will display the same fake alerts, inaccurate scans and other types of fraudulent security information to make it appear as though your PC is under attack by countless threats. Since Windows Protection Unit isn't able to detect or remove any type of genuine PC threat that could endanger your computer, SpywareRemove.com malware researchers discourage any interaction with Windows Protection Unit other than faking its registration (if necessary) and removing Windows Protection Unit with a real anti-malware application. As a rogue anti-virus product, Windows Protection Unit's sole goal is to steal money and related information in its fraudulent registration process, and purchasing Windows Protection Unit or taking its recommendations to heart is never an action that's in your best interests. Windows Protection Unit is a rubber-stamped clone of other scamware programs from FakeVimes, such as Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.
Windows Protection Unit – a Fake AV Program That You'll Want Your Own Protection Against
Windows Protection Unit may look like an anti-virus program with more security features than the popular brands are willing to offer, but this generosity comes easy to Windows Protection Unit, since it doesn't bother to back its features up with the functionality that they'd require. Windows Protection Unit's Advanced Process Control is just a roundabout way of preventing you from using the Windows Task Manager normally, and that's just a prelude to other security-hampering attacks by Windows Protection Unit that SpywareRemove.com malware researchers have found worthy of mention:
- Windows Protection Unit is capable of modifying your Hosts file to redirect your web browser to undesirable sites. Similar attacks may also hijack your search results or prevent you from loading beneficial websites (such as sites for PC security companies).
- Task Manager, competing rogue security programs and various types of legitimate security software can be disabled by Windows Protection Unit. SpywareRemove.com malware researchers suggest that you try to launch Windows without Windows Protection Unit also launching to be able to access all of your anti-malware software and remove Windows Protection Unit in an appropriate manner. Safe Mode and booting from a remote or removable drive can be used to prevent Windows Protection Unit from launching.
- Windows Protection Unit may also change your system settings to permit you to download files with invalid signatures (a telltale sign of a file being malicious) without triggering any warnings from Windows.
- User Account Control (abbreviated as UAC), a Windows security feature that prevents unwanted system changes, may also be disabled.
Detecting and Dealing with a Windows Protection Unit Infestation
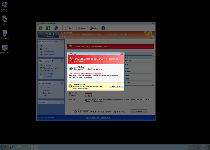
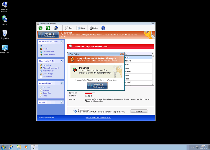
Pop-ups from Windows Protection Unit can be identified by their alarmist and fraudulent contents, which will contain warnings about fake attacks or the presence of nonexistent types of hostile software on your computer. SpywareRemove.com malware experts heartily endorse completely ignoring warning messages, which are common to the Win32/FakeVimes family.
As a security risk, Windows Protection Unit should be removed with anti-malware software that can scan your PC. Because normal methods of deletion won't remove the Hosts file changes and other traits of a Windows Protection Unit infection, SpywareRemove.com malware researchers discourage unassisted attempts to delete Windows Protection Unit if other options are available. Windows Protection Unit can also be registered with the registration code '0W000-000B0-00T00-E0020', which can simplify the process of deleting Windows Protection Unit properly.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%Desktop%\ Windows Protection Unit.lnk
File name: %Desktop%\ Windows Protection Unit.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%CommonStartMenu%\Programs\ Windows Protection Unit.lnk
File name: %CommonStartMenu%\Programs\ Windows Protection Unit.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-4-7_2"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "ahwohainwk"HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aswUpdSv.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atcon.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\advxdwin.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aswRunDll.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\inetlnfo.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bidef.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dvp95.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tds-3.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winupdate.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ozn695m5.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rtvscn95.exe
Additional Information
| # | Message |
|---|---|
| 1 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
| 3 | Warning Firewall has blocked a program from accessing the Internet. Windows Media Player Resources C:\Windows\system32\dllcache\wmploc.dll C:\Windows\system32\dllcache\wmploc.dll is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.