Windows Recovery Series
Posted: April 29, 2012
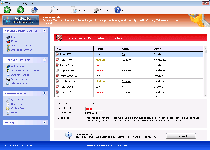
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 9 |
| First Seen: | April 29, 2012 |
|---|---|
| OS(es) Affected: | Windows |
 Contrary to its efforts to appear like a unique and competent anti-spyware product, Windows Recovery Series is just a straight copy of other rogue anti-virus programs that fall under the Win32/FakeVimes classification of scamware. Other than its new name, Windows Recovery Series can be considered a clone of its fake anti-virus scanner brethren, and SpywaRemove.com malware researchers suggest that you ignore any popup alerts, system scans or other forms of security information from Windows Recovery Series, regardless of how legitimate they may look. Besides its fake security feeds that cajole you into spilling money for Windows Recovery Series's registration key, Windows Recovery Series may also be involved in other attacks, with highlights of its hostility including browser redirects and attempts to block completely unrelated security programs and system tools. As a genuine danger to your PC, Windows Recovery Series should always be deleted on sight if you have anti-malware software available for doing so safely.
Contrary to its efforts to appear like a unique and competent anti-spyware product, Windows Recovery Series is just a straight copy of other rogue anti-virus programs that fall under the Win32/FakeVimes classification of scamware. Other than its new name, Windows Recovery Series can be considered a clone of its fake anti-virus scanner brethren, and SpywaRemove.com malware researchers suggest that you ignore any popup alerts, system scans or other forms of security information from Windows Recovery Series, regardless of how legitimate they may look. Besides its fake security feeds that cajole you into spilling money for Windows Recovery Series's registration key, Windows Recovery Series may also be involved in other attacks, with highlights of its hostility including browser redirects and attempts to block completely unrelated security programs and system tools. As a genuine danger to your PC, Windows Recovery Series should always be deleted on sight if you have anti-malware software available for doing so safely.
Why the Only Thing Windows Recovery Series Has for Your PC is a Series of Poor Recommendations and Even Worse Attacks
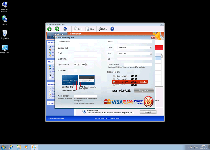
Windows Recovery Series is a copy of such confirmed fake anti-virus applications as System Defragmenter, Ultra Defragger, HDD Control, Win HDD, Win Defrag, Win Defragmenter, Disk Doctor, Hard Drive Diagnostic, HDD Diagnostic, HDD Plus, HDD Repair, HDD Rescue, Smart HDD, Defragmenter, HDD Tools, Disk Repair, Windows Optimization Center, Scanner, HDD Low and Hdd Fix. Each of these clones of Windows Recovery Series, as well as Windows Recovery Series, can be recognized by their Windows Security Center-copycat interface, their inclusion of overstated features like an 'all-in-one suite,' and their attempts to replace Task Manager with an 'Advanced Process Control' window. SpywaRemove.com malware analysts discourage attempts to interact with Windows Recovery Series or use its features, since Windows Recovery Series is incapable of providing accurate security information and will use many of its features merely to redirect your browser to a purchase page.
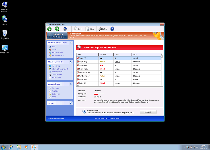
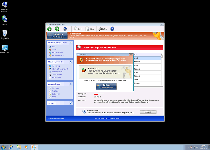
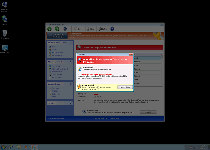
Windows Recovery Series's foremost symptom is the variety of fake security pop-ups, including Windows taskbar notifications, that it displays in an attempt to make you think that your PC is heavily-infected by unrelated PC threats. These fraudulent pop-ups, along with Windows Recovery Series's faux system scans, should be disregarded for the sake of your PC's safety, and under no circumstances do SpywaRemove.com malware researchers recommend that you purchase Windows Recovery Series.
Other symptoms of a Windows Recovery Series infection can include disabled UAC features, malfunctioning or nonoperational security programs (especially Windows Task Manager) and search engine redirects to potentially malicious websites.
The Shortcut to Recuperating from Windows Recovery Series
While SpywaRemove.com malware researchers see nothing to gain from spending money on Windows Recovery Series, in some cases, registering Windows Recovery Series for free can be helpful for smoothing out Windows Recovery Series's removal process. The key '0W000-000B0-00T00-E0020' has been confirmed to work on many members of FakeSysDef, including clones of Windows Recovery Series, and can reduce attacks by Windows Recovery Series until you can remove Windows Recovery Series appropriately.
Windows Recovery Series's deletion should, whenever possible, be handled with anti-malware scanners that can also detect any related PC threats that may have assisted with Windows Recovery Series's installation (such as the prolific Zlob trojan). SpywaRemove.com malware analysts suggest scanning your PC as soon as possible after a Windows Recovery Series infection, since lengthy cohabitation with Windows Recovery Series can result in your computer being damaged by other attacks due to its vulnerable state.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-dogk.exe
File name: Protector-dogk.exeSize: 1.46 MB (1462784 bytes)
MD5: 7d36f6d8800613a0d1a854903e34e459
Detection count: 35
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: April 30, 2012
%APPDATA%\Protector-sett.exe
File name: Protector-sett.exeSize: 2.06 MB (2069504 bytes)
MD5: 18510cef2424d343a6b9905529f9c5fc
Detection count: 7
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: April 30, 2012
%AppData%\Protector-[RANDOM].exe
File name: %AppData%\Protector-[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Inspector-[RANDOM].exe
File name: %AppData%\Inspector-[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "ID" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-2-17_2"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "rudbxijemb"HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashDisp.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\divx.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mostat.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\platin.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapsetup3001.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avp32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avpcc.exe
Additional Information
| # | Message |
|---|---|
| 1 | Error
Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Error Software without a digital signature detected. |
| 3 | Warning
Firewall has blocked a program from accessing the Internet. Windows Media Player Resources C:\Windows\system32\dllcache\wmploc.dll C:\Windows\system32\dllcache\wmploc.dll is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
| 4 | Warning! Identity theft attempt Detected |
| 5 | Warning! Identity theft attempt Detected
Hidden connection IP: 58.82.12.124 Target: Your passwords for sites |
| 6 | Your system files are at risk. We strongly advise you to activate your protection. |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.