Windows Secure Workstation
Posted: August 13, 2012
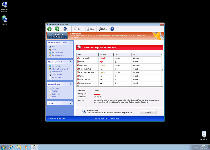
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 7 |
| First Seen: | August 13, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
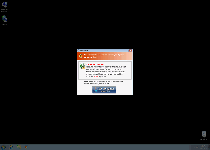
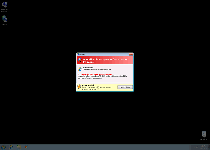
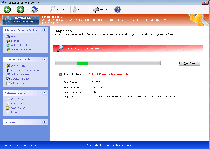 Windows Secure Workstation is a new version of fake anti-malware software that's duplicated from other members of its family with a change in brand name. Windows Secure Workstation uses fake scans and pop-up warnings to convince you that Windows Secure Workstation is capable of searching and deleting malicious software. However, Windows Secure Workstation is incapable of backing up these claims with genuine anti-malware features, and the most prominent symptom of a Windows Secure Workstation infection includes attacks against real security applications. Given that SpywareRemove.com malware experts have confirmed Windows Secure Workstation and its close relatives as scamware without any positive traits, you should be content in finding a way to disable Windows Secure Workstation so that actual anti-malware programs can remove Windows Secure Workstation for good, rather than spending money on its fake services.
Windows Secure Workstation is a new version of fake anti-malware software that's duplicated from other members of its family with a change in brand name. Windows Secure Workstation uses fake scans and pop-up warnings to convince you that Windows Secure Workstation is capable of searching and deleting malicious software. However, Windows Secure Workstation is incapable of backing up these claims with genuine anti-malware features, and the most prominent symptom of a Windows Secure Workstation infection includes attacks against real security applications. Given that SpywareRemove.com malware experts have confirmed Windows Secure Workstation and its close relatives as scamware without any positive traits, you should be content in finding a way to disable Windows Secure Workstation so that actual anti-malware programs can remove Windows Secure Workstation for good, rather than spending money on its fake services.
Other scamware that belong to the FakeVimes include Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.
When You Can't Trust Windows Around Windows Secure Workstation
Windows Secure Workstation, as a rogue anti-malware scanner, isn't able to protect your PC from Trojans, viruses or other types of malware, but its features will strive to imitate legitimate security programs. This can include subverting your Windows startup process to include fake warning messages before you're even allowed to load your desktop, the presentation of fake Fake Microsoft Security Essentials Alert and announcements that prominent Windows tools (such as Task Manager) are infected or damaged. SpywareRemove.com malware analysts encourage you to ignore all unusual security warnings during a Windows Secure Workstation infection until you've disabled Windows Secure Workstation, which can be done with either Safe Mode or a system boot from a clean USB drive.
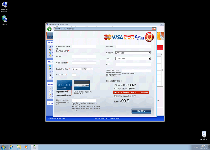
Like its identical kin (such as the equally-recent Windows Anti-Malware Patch, Windows Ultimate Safeguard or Windows Virtual Angel), Windows Secure Workstation's only goal in displaying this fake security information is to make you spend money on a purchasable registration key. However, even once registered, Windows Secure Workstation can't detect actual PC threats or protect your computer from them, and any financial information handed over in this process should be considered effectively compromised.
What Windows Secure Workstation Does to Make You PC Insecure
Although Windows Secure Workstation may be distributed by various means, its central method of infecting new PCs is through fraudulent system scans that are hosted on hostile websites. Since these scanner simulations often use JavaScript, disabling JavaScript or keeping it uninstalled can help to block content that installs Windows Secure Workstation without your consent. Although you may experience a prompt about downloading security software, most such attacks will install Windows Secure Workstation or a related type of fake anti-malware software regardless of what you click.
SpywareRemove.com malware researchers also note that Windows Secure Workstation may block many different types of applications while Windows Secure Workstation is active. Competing types of scamware, legitimate Windows security utilities and anti-virus scanners may all be blocked by Windows Secure Workstation, with corresponding fake pop-up warnings. Windows Secure Workstation's startup process exploits the Windows Registry, and methods of booting that sidestep Registry settings (such as booting from a USB drive) can also let you access your PC and its software without launching Windows Secure Workstation.
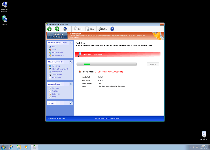
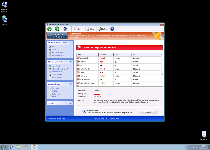
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-ytky.exe
File name: Protector-ytky.exeSize: 2.61 MB (2616320 bytes)
MD5: 89d2b47749a39d5f29d96f38138e2f20
Detection count: 46
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]HKEY_CURRENT_USER\Microsoft\Windows\CurrentVersion\Settings\ID 4HKEY_CURRENT_USER\Microsoft\Windows\CurrentVersion\Settings\UID [RANDOM CHARACTERS]HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXEHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exeDebugger svchost.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.