Scammers Continue to Use The Hunger Games to Hunt for Vulnerable PCs and Launch Malware Attacks
 As people continue to be obsessed with The Hunger Games, you can bet that cybercriminals also are obsessed with the phenomenon surrounding The Hunger Games and want to get a piece of the action. Internet users are searching the Web for 'free' Hunger Games movies, ebooks, screensavers, etc. Therefore, anything related to The Hunger Games is a perfect oportunity to hunt for prospective, gullible PC users to scam or infect with malware.
As people continue to be obsessed with The Hunger Games, you can bet that cybercriminals also are obsessed with the phenomenon surrounding The Hunger Games and want to get a piece of the action. Internet users are searching the Web for 'free' Hunger Games movies, ebooks, screensavers, etc. Therefore, anything related to The Hunger Games is a perfect oportunity to hunt for prospective, gullible PC users to scam or infect with malware.
Blockbuster hits like the Hunger Games have their uses for criminal enterprises, and we've taken note of a range of attacks that exploit the popularity of the Hunger Games cinematic experience to launch attacks against the vulnerable PCs of fans. Similar to previous efforts that have also targeted popular media products like Twilight and the 3D re-release of the Titanic, recent Hunger Games-related attacks have created poisoned search results that lead fans of the movie to malicious sites, often under the pretense of offering a 'free' download of the movie. The fake movie player updates and fake media files that these websites host are typically used to install PC threats, especially rogue security programs, although other types of threats (such as browser hijackers or trojan downloaders) are both possible and probable. Even though many of these sites have been blacklisted or taken down, attacks are ongoing, and SpywareRemove.com malware research team warns you to be cautious about downloading files from websites that claim to offer free Hunger Games movie content, which can be tantamount to giving a trojan free reign over your computer.
What Hackers are Really Hungry to Gnaw: the Computers and Wallets of Hunger Games Fans
Over time, malicious software distribution has become a highly-tuned machine that responds flexibly to new trends and social movements, and recent online attacks that use the Hunger Games movie as bait serve to emphasize that irksome fact. Using poisoned search results to waylay online searches and redirect traffic to sites that host harmful software isn't anything new, but criminals were so impatient to do the same for the Hunger Games that they didn't even wait for its premiere before launching over three dozen separate instances of such toxic websites. While these sites may seem to offer footage of the Hunger Games and will appear to be highly-ranked in search results, their only real content is a parcel of trojans and other PC threats, delivered via deceptively-named executable files.
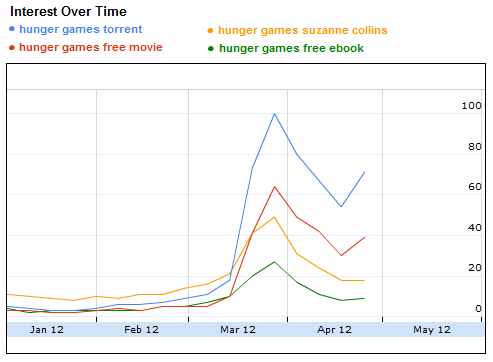
The Hunger Games is a particularly juicy target, as the Hunger Games movie has managed to keep a stranglehold grip on box office charts for a month now – surpassing all of its would-be competition since the special effects extravaganza Avatar, which also managed a four-week record, among other cinematic feats. The top factor that's common in search terms that SpywareRemove.com malware researchers have found to have a high chance of returning poisoned results is a focus on download links for illegal Hunger Games footage, especially for no-charge or 'free' movie files. Examples of some of the most-exploited search terms that may result in poisoned results for the Hunger Games include 'hunger games torrent,' 'hunger games free movie,' 'hunger games suzanne collins,' 'hunger games free ebook.' More than 50 percent of the first 100 search results of the Hunger Games popular search terms have links that can potentially lead to malware. Malware is usually the consequence of downloading copyrighted music and movies. Other sites may also use social networking attacks (SpywareRemove.com malware experts point out the popularity of malicious Facebook wall links) or mass-mailed e-mail or spam to grab an undeserved slice of fandom traffic.
Since the release of the film version of The Hunger Games, Google Insights (Figure. 1) shows there was a considerable rise of web traffic between March 25-31 for the most-exploited search terms related to Hunger Games.
Figure 1. A snapshot from Google Insights that shows the web search interest for the search terms: hunger games torrent, hunger games free movie, hunger games suzanne collins and hunger games free ebook.
What Kind of Online Scam Strategies You Should Expect
Typically, sites that exploit the Hunger Games mania for less than honest purposes limit their attacks to one of two primary strategies, although exceptions may break this general guideline:
- Fake download sites for the Hunger Games will claim to offer the movie file itself for download. This file is typically a PC threat in the form of an .exe that's been renamed to appear like another file type, such as .mpg, .flc or .mov.
- Other sites host what looks like a streaming movie player that offers the Hunger Games experience without the fuss of a download. Any attempt to use this fake player will display a fraudulent update alert for Adobe, Realplayer or another type of popular media player brand. This is a common means of distribution for trojans, such as Zlob that install scamware products (such as the recently-emerged Smart HDD, Smart Fortress 2012 or Windows Antibreaking System).
Either of these attacks may also create fake system warnings and infection alerts in the course of installing their malicious software.
Although movies are a prime focus for such sites due to high demand, similar hoaxes can involve other forms of Hunger Games media such as screensavers and desktop backgrounds. Malicious software that's installed by Hunger Games search attacks can range the gamut from keyloggers to backdoor trojans to browser hijackers, although faux security applications and spyware that specialize in theft of personal information are especially popular.
Quenching the Craving Hunger Games Frauds Have for Your Vulnerable PC
Looking at poisoned search results and other attacks that are linked to the Hunger Games searches from within the context of the overall malicious software industry, Hunger Games-based PC threats and attacks are just the latest rendition of criminals trying to ride the momentum of popular fads to infect your computer. The same behavior has also been noted by SpywareRemove.com malware researchers in events such as the 2011 cornucopia of Facebook scams that supposedly offered free tickets to a playing of Twilight – with new scams released to coincide with each movie in the series. Besides installing malicious software, these attacks often coincide with phishing attacks that attempt to harvest information like your street address or phone number.
Tips to Help Prevent Hunger Games Scams and Other Internet Fraud
Appropriate protection against malicious Hunger Games links and fake Hunger Games websites requires various precautions, all of which SpywareRemove.com malware researchers recommend, in addition to keeping a good anti-malware program installed to detect PC threats during your Hunger Games web-browsing:
- Never install software updates from third-parties or unusual websites. Movie players and similar programs often require codec updates and other patches that should always be downloaded from the original (and hopefully trustworthy) company's website. This includes updates for script packages like Flash or Java.
- Verify the safety of a link for a popular trend, such as Hunger Games, before you click on it. Inspect a link's web address and, if necessary, check it with appropriate PC security companies. SpywareRemove.com malware analysts recommend that you use enhanced caution around social network links (such as links from Twitter or Facebook) that are posted with brief, generic or poor descriptions.
- Be careful around websites that are known to distribute illegal files, such as movie downloads for Hunger Games and equally popular movies, and always check any available comments to see what other users say about the safety of the file that you're thinking of downloading.
- Never open a file unless you're sure what its file type is. Many types of PC threats, including those that are related to toxic Hunger Games searches, are renamed inaccurately, but careful inspection will help you determine the true file type. Executable files (which are identifiable by their .exe acronym when properly labeled) should be considered particularly risky.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.