Unstoppable Petya Ransomware CyberAttack Hits Networks and Computers in Over 65 Countries
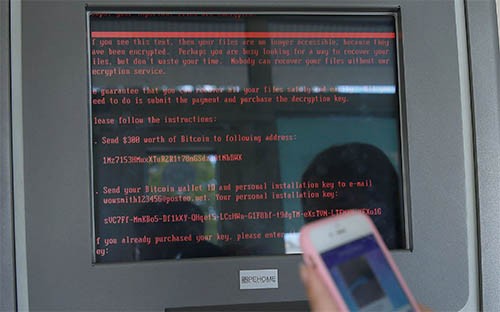
 Yesterday saw the second major ransomware outbreak in a matter of less than two months. Countless big and small organizations including financial and government institutions, media, Russia's Central Bank, Airports in Kiev, the shipping giant Maersk, and a number of other companies working in a variety of industries had their computer systems locked. Microsoft says that while Russia and Ukraine were hit the hardest, there are victims in as many as 65 countries, and pictures circulating the internet even show ATMs having a ransom note on their screens, as show in Figure 1 below.
Yesterday saw the second major ransomware outbreak in a matter of less than two months. Countless big and small organizations including financial and government institutions, media, Russia's Central Bank, Airports in Kiev, the shipping giant Maersk, and a number of other companies working in a variety of industries had their computer systems locked. Microsoft says that while Russia and Ukraine were hit the hardest, there are victims in as many as 65 countries, and pictures circulating the internet even show ATMs having a ransom note on their screens, as show in Figure 1 below.
We're pretty sure that you want to know how this attack compares to the WannaCry disaster from last month. While there are some similarities, yesterday's ransomware worm appears to be much more sophisticated than WannaCry.
It attacks the Master Boot Record and Master File Table of the infected machine which is why many people decided that it's a new version of the Petya ransomware. After a closer investigation, however, the researchers discovered that while the two families do share some code, they are many differences. In their quest to differentiate the two ransomware strains, the security companies came up with some tongue-twisting names like Nyetya and the simpler but not terribly creative NotPetya. The researchers aren't able to find a consensus on the name which is why we'll simply refer to the file-scrambling malware as the new Petya.
Figure 1. Petya Ransomware Cyberattack Infected ATM Machine Message
While they can't agree on how to call it, they are all adamant that the new ransomware was developed by someone who knew what he was doing. The investigation is still ongoing, and nobody can say definitively where the new Petya came from. Experts from Microsoft's Malware Protection Center as well as other researchers do seem to be pretty sure, however, that at least a portion of the infections came courtesy of a Trojanized update to MEDoc, a Ukrainian accounting program. MEDoc's developers initially recognized that their servers had inadvertently launched a massive cyberattack and apologized, but later, they retracted the statement and claimed that they're not responsible. Earlier today, reports emerged that the new Petya has also been spread by drive-by downloads on compromised websites. Hopefully, more information will be available on the initial infection vector in the coming days.
Petya Follows Close To The Footsteps of WannaCry Ransomware
Once it's in, the malware doesn't proceed to encrypt files immediately. It first sets about using one of its three worm components to copy itself to neighboring computers. The first method involves a Mimikatz sample which is dropped in the %temp% folder. Mimikatz is a password stealer which retrieves administrative credentials and uses them to infect other endpoints on the network with the help of Windows' Management Instrumentation Command-Line (WMIC). The second one abuses the Windows' PsExec tool, and the third one comes in the form of the now infamous EternalBlue SMBv1 exploit. EternalBlue, as you may remember, played a crucial role in spreading WannaCry to hundreds of thousands of computers worldwide last month, and it's just about the only similarity between the two campaigns.
Unlike WannaCry, the new Petya doesn't come with an Internet scanner which means that, although it's still a worm, it will only affect machines on the local network. Because it has other spreading mechanisms, however, it can infect systems that have been patched against EternalBlue.
Once it has copied itself to as many PCs as possible, it creates a scheduled task that reboots the system after a preset amount of time. Next, Emsisoft's experts say, Petya installs its own small operating system on the Master Boot Record of the infected machine. When the scheduled task reboots the PC, the new Petya launches its two encryption components.
The first one generates a machine-specific AES key and uses it to encrypt up to 1MB of every targeted file. Then, using a hardcoded RSA public key, it scrambles the AES key. The mechanism, it should be noted, is different from the one Misha, the file-encrypting component found in the old Petya, used in the past. The next stage is classic Petya, though. When it's done scrambling the files, the ransomware also encrypts the Master File Table using the Salsa20 algorithm and renders the computer completely inoperable.
While this is happening, the user sees a fake CHKDSK screen which pretends to scan the hard drive for errors, and when the encryption is complete, the ransom note appears. This time, there are no ASCII Jolly Roger drawings. Instead, victims are faced with a few paragraphs indicating what has happened (some of the text has been borrowed from WannaCry) and a ransom demand of $300 in Bitcoin.
Petya Creators Leave Out Details Leaving The Ransomware Incomplete
The new Petya is undoubtedly the work of an experienced black hat. Whether the same person is responsible for the previous versions is open for debate, but the author certainly has plenty of technical skills. This is strange because when it came to setting up the payment system, he acted like a complete amateur.
There's no individual Bitcoin address for each victim. Instead, there is just one hardcoded wallet inside the ransom note, and earlier today, Motherboard said that it's already been filled with about $10 thousand. The trouble is, the organizations that are still paying the ransom will never see their data back. That's because Petya's author instructed victims to contact him at "wowsmith123456@posteo.net," and yesterday, after seeing that their services are being abused by cybercriminals, Posteo closed the email account. Currently, organizations affected by the new Petya have no way of getting in touch with the ransomware operator and telling him that they've transferred the bitcoins. Paying the ransom is not a good decision.
Speaking of decisions, it's still unknown what the cybercrook behind yesterday's attack wanted to achieve, but from a business perspective, the whole thing might turn out to be a bit of a flop. There's too much attention from the media and the law enforcement agencies which means that whoever the person behind the Bitcoin wallet is, he'll have to be incredibly brave to take the money and go on the run. When it comes to causing damage, however, the new Petya campaign was a resounding success. And unfortunately, there's nothing to suggest that it will be the last of its sort.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.