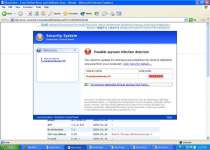
Maocal
Maocal is a trojan designed to steal sensitive user information and log keystrokes. It starts automatically on each computer startup and works in background. Maocal collects passwords and other valuable data and sends it to its home servers. It can update itself via the Internet. Maocal doesn't damage the computer, but severely violates user privacy. Consider removing it immediately.
The following files were created in the system: