70GB Worth of Personal and Financial Data Uncovered In Torpig Botnet Hijack
A recent botnet hijack discovered that a hacker group made off with millions of data items. Ten days worth of information containing 10,000 bank accounts and credit card numbers worth hundreds of thousands of dollars, was discovered by security researchers at the University of California, Santa Barabra. The discovery came about when the security researchers at the University broke into the Torpig botnet, associated with Mebroot or Sinowal.
The Torpig or Sinowal botnet, is one of the more sophisticated networks because it uses malicious software to infect computers in an effort to harvest information such as banking accounts, credit card numbers and email passwords. The researchers from the University were able to monitor more than 180,000 infected or hacked computers by exploiting a weakness within the hackers network that controlled the group of infected computers.
What is Torpig/Sinowal and Mebroot?
Torpig/Sinowal is known to be a botnet that is capable of stealing usernames and passwords from several widely used email clients such as Outlook, Thunderbird and Eudora. In addition to collecting email credentials, Torpig is able to gather passwords from web browsers and infect PC's through malicious websites via a drive-by download attack method. Torpig/Sinowal is actually installed onto a users system after it is first infected with Mebroot, an older rootkit that first appeared in December 2007. Mebroot is a Trojan known to infect a computer's Master Boot Record (MBR). The MBR is the first code or data that a system looks for during the boot process to load the operating system. Mebroot also has the capability to download other malicious files or code onto a compromised system.
Hackers, who controlled the botnet or group of compromised computers, were able to gather data for a total of 10 days. After the 10th day they updated the command-and-control instructions. In the allotted amount of time, just 10 days, the hackers were able to gather about 70GB worth of data from the compromised computers. The information consisted of email passwords, Windows passwords, FTP credentials, financial data and credit card numbers.
In figure 1 below, the Torpig botnet was discovered to have gained millions of data items.
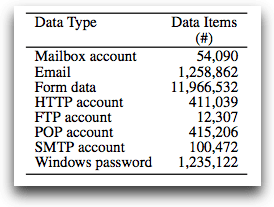
Figure. 1 [image source: blogs.zdnet.com]
How is a Botnet like Torpig/Sinowal disrupted?
Security researchers are able to figure out the different algorithms of botnets such as Torpig. They are able to predict which domains the malware will connect too and pre-register them to interrupt the botnet's impending actions. This process is similar to that used by the ad-hoc group that attempted to put an end to the Conficker worm infection. Conficker generated up to 50,000 domains names a day, similar to the Torpig/Sinowal Botnet.
After this discovery, it was estimated that Torpig's criminal network profited between $83,000 to an astonishing $8.3 million in just a ten day time frame.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.