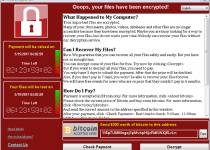
DNS Unlocker
The DNS Unlocker is a utility for modifying how your PC interacts with the Domain Name System hierarchy, which may affect which websites your browser loads. While neither illegal nor threatening, the DNS Unlocker's features are easily exploitable for undesirable side effects, such as injected advertisements, redirecting your browser or blocking various websites. Since these risks may outweigh the DNS Unlocker's benefits, malware experts recommend removing the DNS Unlocker for any PC users who...