‘Computer Crime & Intellectual Property Section’ Ransomware
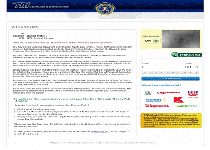
 'Computer Crime & Intellectual Property Section' ransomware is a variant of the Trojan commonly-identified as Trojan:Win32/Reveton.A . Like Police Central e-crime Unit (PCEU) ransomware , the Strathclyde Police Ukash Virus , ' Poliisi Tietoverkkorikos Tutkinnan Yksikkö' Ransomware and similar ransomware Trojans from this family, 'Computer Crime & Intellectual Property Section' ransomware displays a fraudulent pop-up that claims that your PC is guilty of being used in various...
'Computer Crime & Intellectual Property Section' ransomware is a variant of the Trojan commonly-identified as Trojan:Win32/Reveton.A . Like Police Central e-crime Unit (PCEU) ransomware , the Strathclyde Police Ukash Virus , ' Poliisi Tietoverkkorikos Tutkinnan Yksikkö' Ransomware and similar ransomware Trojans from this family, 'Computer Crime & Intellectual Property Section' ransomware displays a fraudulent pop-up that claims that your PC is guilty of being used in various...