Android.ZBot Banking Trojan Steals Credit Card Details via Android Smartphones
 Smartphones running Android have had their fair share of malicious apps cause serious issues in the past few years. The trend seems to continue as new malicious apps are emerging with aggressive actions. Among those actions, the recent Android.ZBot banking Trojan threat is stealing credit card details from Android smartphones.
Smartphones running Android have had their fair share of malicious apps cause serious issues in the past few years. The trend seems to continue as new malicious apps are emerging with aggressive actions. Among those actions, the recent Android.ZBot banking Trojan threat is stealing credit card details from Android smartphones.
The growing precedence of smartphone malware has set forth a new trend that cybercrooks are cashing in on. Use of what Dr.Web discovered to be a new mobile banking Trojan targeting Android users, dubbed Android.ZBot, is compromising infected smartphones and stealing credit card details on the device only to give them to the hackers behind the Trojan scheme.
In the discovery of Android.ZBot by Dr.Web's staff, it was found that the threat has multiple botnets and has compromised between 140 and 2,300 devices. At the time of discovering Android.ZBot, about 15 of its initial 20 botnets are still active, which is more than enough to initiate destruction where the threat collects card details stored on infected Android devices.
Distribution of malicious Android apps has always been a major issue. The Google Play Store has taken many actions to prevent the influx of malicious apps proving to lower the spread of malware among Android devices. However, 3rd party Android app sites and fake Google Play Store apps are the major culprits for the spread of malicious Android apps, such as Android.ZBot, which spread primarily through a stand-alone app that claims it is the official Google Play Store application.
Malware creators have ensured that their latest malicious Android apps are highly effective. In the case of Android.ZBot, it is able to hide on an infected device and allow the device to boot up while it collects personal user data without giving any indication to its activities. Collecting the personal data on the device later leads to the connection to its command and control server over the internet. So far, the Android.ZBot threat has only deployed financial-related apps exclusively in Russian. However, there could be instances in the near future that branch out to other locations around the world to seek financial data belonging to other institutions.
The limitations within the Android operating system have kept Android.ZBot in check when it comes to injecting external HTML code. Nevertheless, Android.ZBot proves to be a serious threat that could easily compromise a large amount of personal and financial data stored or access on an Android device.
The chart below is a representation of how many Android devices are estimated to have the Android.ZBot threat installed, reaching a peak in October 2015 and a slight decline in November 2015.
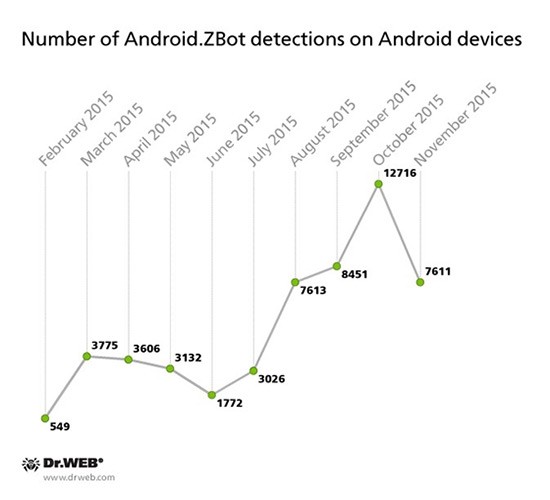
Dr.Web's Android.ZBot detection rate chart
Could you imagine, you open up your online banking account through your Android smartphone and the next day you check your account and it has a zero or negative balance? Such a situation can very well happen in the scope of what Android.ZBot and its creators are capable of doing. The creative phishing techniques of Android.ZBot are highly effective, and you could be putting yourself at risk by downloading and installing apps from unknown sources on the internet or those that claim to be a legitimate app store.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.