Droidclub's Malicious Chrome Extensions Affected Hundreds of Thousands of Users
 Chrome extensions could be useful. They could be good fun, and they could boost your productivity. In some cases, however, Chrome extensions could be dangerous. Researchers from TrendMicro wrote about a botnet called Droidclub and explained how it infects users via Google Chrome extensions.
Chrome extensions could be useful. They could be good fun, and they could boost your productivity. In some cases, however, Chrome extensions could be dangerous. Researchers from TrendMicro wrote about a botnet called Droidclub and explained how it infects users via Google Chrome extensions.
The attack starts with malicious advertisements, but they alone are not enough. Some social engineering is needed as well. The users are redirected to a website which displays a popup saying that in order to view it, they need to install a Chrome extension. Clicking Ok downloads the extension automatically, and all that's left is for the user to install it. At this point, the extension will display the permissions it needs in order to operate, but as we all know, users tend to ignore them and simply click Ok.
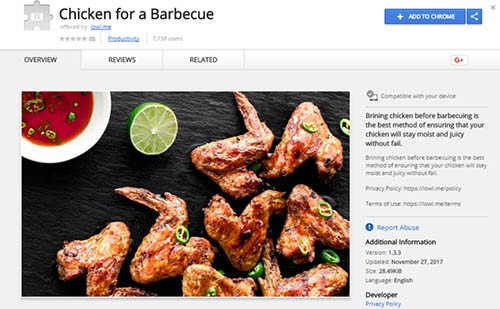
The extensions' names and descriptions are also ignored, apparently. TrendMicro posted a Chrome Web Store screenshot of one of them, and it seems to be a guide to brining chicken before a barbeque. Quite why this should exist as a browser extension is slightly baffling, but more than 420 thousand users installed it and the other 88 Droidclub add-ons which appear to be just as nonsensical.
Screenshot of Chrome Web Store Questionable Add-on - Source: TrendMicro
Once installed, Droidclub's extension contacts the Command & Control (C&C) server and downloads some configuration code. Most of the malicious behavior revolves around ads. The researchers noted that random popups start showing up, and some JavaScript could also link specific keywords on a web page to low-quality advertisements. The ads on the website victims are visiting could also be changed. Unfortunately, this is not all.
The Droidclub botnet has been around since at least April 2017, and the experts noted that some of its previous versions also included the infamous Coinhive script, which turned the victims' computers into cryptocurrency miners. With the more recent updates, the botnet's operators de-activated the script, but TrendMicro warned that re-deploying it shouldn't be too much of a challenge.
Worryingly, there's even more to it than that. The extensions also inject a library from a legitimate web analytics tool called Yandex Metrica. It's designed to help website operators monitor the way users behave on a certain page by recording things like mouse clicks and scrolling. The library can also record keystrokes, and although passwords aren't logged, things like usernames, email addresses, and even credit card details could be stolen.
Droidclub's operators also made their extensions difficult to remove. If users try to uninstall them from the Chrome Web Store, they will simply be redirected to the introduction pages. If they try to remove them through chrome://extensions, they will be redirected to a fake page that mimics Chrome's interface and fools the victims into thinking that the add-on is gone while it's still installed and operational.
Thankfully, TrendMicro got in touch with Google, and the 89 extensions associated with Droidclub were removed from the store and deactivated on victims' PCs. Cloudflare, meanwhile, took down the C&C servers, which means that for now, the Droidclub botnet is down. Nevertheless, Google Chrome's users should be careful with the extensions they install. Ad-blocking tools could also prove helpful.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.