Exploit Kits, Mobile Malware and Botnets Becoming Cybercriminals’ Weapons of Mass Computer Destruction
 Exploit kits combined with mobile malware and aggressive botnets on the side, is turning out to be the best dish served up by cybercrooks this year as a new threat report from F-Secure Labs confirms a booming business in such types of malware threats.
Exploit kits combined with mobile malware and aggressive botnets on the side, is turning out to be the best dish served up by cybercrooks this year as a new threat report from F-Secure Labs confirms a booming business in such types of malware threats.
Exploitation kids might as well be happy meals for cybercrooks as they are readily available entities that allow a new form of automation to exploit vulnerabilities within computers. The old notion of working smarter not harder is more relevant than it has even been when it comes to new advanced exploit kits now days, and it is turning out to be good business for cybercrooks and hackers.
"The world of malware today is commoditized and professionalized," says Mikko Hypponen, Chief Research Officer at F-Secure. "We saw this especially in the second half of last year in the form of more standardization of vulnerability exploitation, and the increased use of automated exploit kits."
F-Secure has outlined in their latest threat report for 2012, how in 2012 exploit kits finding vulnerabilities within software were the most popular way to gain access to a user's system. During the second year of 2012, 28 percent of all detections were exploit-related while 68 percent of those were related to vulnerabilities in Java.
You may have already skimmed across an article or story talking about how Java is under attack again and somehow you must disable it on your PC to avoid the latest and greatest exploitation. Well, there is a reason you are seeing these reports in abundant numbers lately. It is simple, today's exploit kits are popular and widely used by hackers because they are extremely effective. The BlackHole and Cool Exploit are among the popular ones, which include exploits for Windows and Java vulnerabilities.
"Criminals in the malware system each handle their own little niches, their own little links in the chain," says Sean Sullivan, Security Advisor at F-Secure. "And exploits are the first link. They're how the criminals get in the door."
Knowing that criminals can virtually create a 'key' to your computer's 'doors', it becomes an extremely scary thought in the minds of the computer illiterate. Just think of that key being created on an automated assembly line without taking any breaks. Things get really serious now.
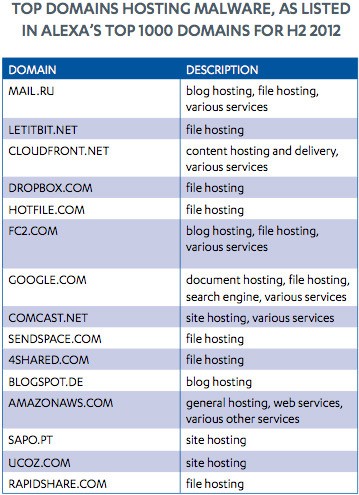
There is an abundance of domains hosting malware, many of which are piggybacked off of well-known URLs belonging to gigantic legitimate companies. These malicious domains, some of the top ones listed in Figure 1 below, were found to host malware in some fashion at the hands of a cybercriminal. Through these avenues malware may be spread reaching mobile devices and even compromising large groups of computers to form botnets.
Figure 1. Top Domains Hosting Malware as listed in Alexa's Top 1000 Domains for H2 2012
Botnets and mobile malware are also issues growing at a pace only second to exploit kits. In the spectrum of mobile malware, Android malware accounted for 79% of all new, unique mobile malware variants in 2012. Also, according to F-Secure, Botnets resurfaced in 2012 formulating entities such as the ZeroAccess botnet comprised of 140,000 unique IPs in the US and Europe. The infamous bank-password-stealing Zeus botnet is still on the radar screen in many countries, including the US, Germany and Italy.
Not only has F-Secure's analysis outlined new threats to be on the lookout for, but it has empowered others to take proactive precautions by utilizing stronger passwords, keeping all of their software updated and installing trusted anti-spyware solutions on their computer. What steps have you taken to ensure your computer is protected from cybercriminals' weapons of mass computer destruction?
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.