Windows Armour Master
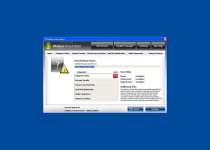
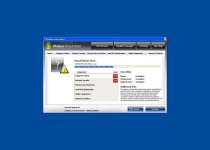
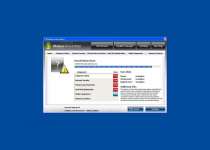
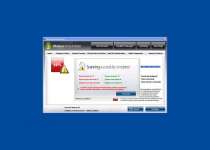
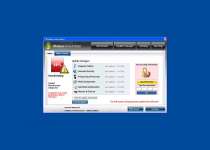
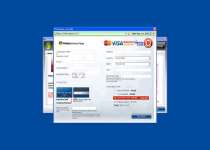
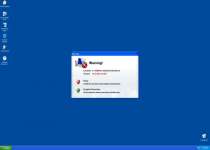
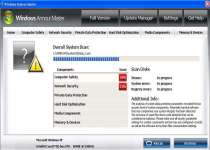 Windows Armour Master is a rogue anti-spyware program which pretends to be a trustworthy security tool, and thus, tries to fool computer users. Like its predecessor Windows Armature Master, Windows Armour Master was created by cyber-criminals to cheat users and steal their money. Windows Armour Master usually is delivered via Trojan infection, and it can infiltrate into your PC system without your knowledge and permission. Windows Armour Master can stay dormant for a while before it sends you a Fake Microsoft Security Essentials Alert warning message, pretending to be a part of the legitimate Microsoft Security Essentials product. Windows Armour Master forces you into downloading and installing its scam security tool. When installed on a computer system, Windows Armour Master starts a bogus system scan and returns numerous malware threats, memory and devices problems, critical system malfunctions and other security issues allegedly detected on the infected computer. However, all listed parasites and issues are fake, and you should ignore them; otherwise, Windows Armour Master scareware will extort your money. After that, Windows Armour Master offers the affected user to purchase its supposed registered version to remove those allegedly reported malware infections and computer problems. Do not trust anything what Windows Armour Master would promise you to do on your machine. Never purchase Windows Armour Master and remove it from your computer immediately after its detection by using a legitimate anti-virus software.
Windows Armour Master is a rogue anti-spyware program which pretends to be a trustworthy security tool, and thus, tries to fool computer users. Like its predecessor Windows Armature Master, Windows Armour Master was created by cyber-criminals to cheat users and steal their money. Windows Armour Master usually is delivered via Trojan infection, and it can infiltrate into your PC system without your knowledge and permission. Windows Armour Master can stay dormant for a while before it sends you a Fake Microsoft Security Essentials Alert warning message, pretending to be a part of the legitimate Microsoft Security Essentials product. Windows Armour Master forces you into downloading and installing its scam security tool. When installed on a computer system, Windows Armour Master starts a bogus system scan and returns numerous malware threats, memory and devices problems, critical system malfunctions and other security issues allegedly detected on the infected computer. However, all listed parasites and issues are fake, and you should ignore them; otherwise, Windows Armour Master scareware will extort your money. After that, Windows Armour Master offers the affected user to purchase its supposed registered version to remove those allegedly reported malware infections and computer problems. Do not trust anything what Windows Armour Master would promise you to do on your machine. Never purchase Windows Armour Master and remove it from your computer immediately after its detection by using a legitimate anti-virus software.
File System Modifications
- The following files were created in the system:
# File Name 1 %UserProfile%\Application Data\Microsoft\[RANDOM CHARACTERS].exe 2 deqnhti.exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR" = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.