Windows Inspection Utility
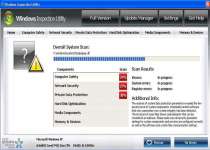 Windows Inspection Utility is the latest re-skin of a rogue security program that's being passed around by many different names with the help of a Trojan that imitates Windows alerts. Despite a slightly different appearance and a fresh name, Windows Inspection Utility acts just like its predecessors by using inaccurate infection warnings and deceptive system scans to bully you into purchasing a fake product registration key. In addition to these false positives, Windows Inspection Utility may also block you from using various applications and redirect your web browser to dangerous websites. Because of the latter symptoms, any infection by Windows Inspection Utility should be considered to be a serious threat; remove Windows Inspection Utility by using suitable anti-malware programs and techniques.
Windows Inspection Utility is the latest re-skin of a rogue security program that's being passed around by many different names with the help of a Trojan that imitates Windows alerts. Despite a slightly different appearance and a fresh name, Windows Inspection Utility acts just like its predecessors by using inaccurate infection warnings and deceptive system scans to bully you into purchasing a fake product registration key. In addition to these false positives, Windows Inspection Utility may also block you from using various applications and redirect your web browser to dangerous websites. Because of the latter symptoms, any infection by Windows Inspection Utility should be considered to be a serious threat; remove Windows Inspection Utility by using suitable anti-malware programs and techniques.
Inspecting the Fraudulent Inspector Software
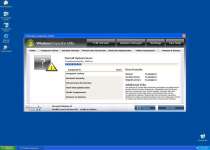
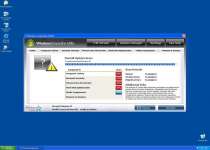
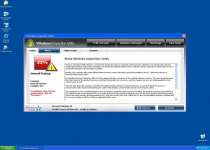
Windows Inspection Utility is part of a very large family of rogue programs that include such members as Windows Oversight Center, Windows Power Expansion, Windows Utility Tool, Windows Processes Organizer, Windows Lowlevel Solution and Windows Process Regulator. These programs all use the official Windows logo along with a generally professional-looking interface that pretends to monitor updates, licenses, possible infections and other aspects of system security.
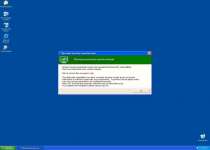
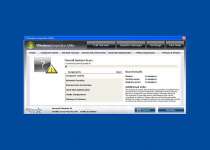
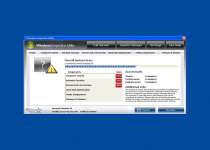
Sadly, these features are just empty shells with all the shine and none of the function to back up Windows Inspection Utility's claims of utility. Infections from the Windows Inspection Utility family of rogue programs are usually caused by the fake Microsoft Security Essentials Alert Trojan. One of the first errors you'll see from this Trojan will look similar to this one:
Microsoft Security Essentials Alert
Potential Threat Details
Microsoft Security Essentials detected potential threats that might compromise your private or damage your computer. Your access to these items may be suspended until you take an action. Click 'show details' to learn more.
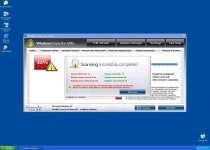
Afterwards, the Trojan will tell you that a Trojan.Horse.Win32.PAV.64.a infection is on your system, and present a software download to 'remove' it. Not only is this Trojan not real, but Windows Inspection Utility can't even detect or remove Trojans in the first place.
Making the Most of Genuine Utility to Kick Out Windows Inspection Utility
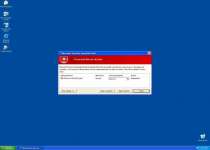
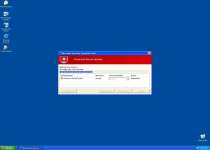
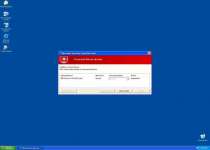
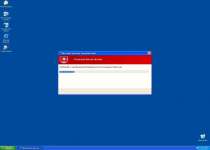
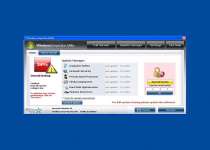
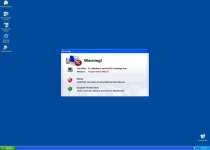
While Windows Inspection Utility is on your computer, you'll see many different types of fake errors, including this one:
Warning!
Name: [program executable]
Name: [program executable file path]
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning.
This particular error message is notable because it's often used as part of a misdirecting attack that simultaneously blocks an application and then blames a nonexistent keylogger for the problem. In reality, Windows Inspection Utility is causing the problem. You may be able to avoid this attack by renaming the executable file into a generic file, such as 'explorer.exe.'
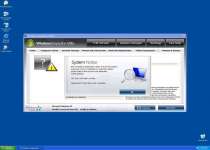
Your Registry will be corrupted to let Windows Inspection Utility remain active at all times, and even your web browser can't be trusted, as Windows Inspection Utility can hijack it and force it to display dangerous websites or fake errors. The first thing you can do to neuter Windows Inspection Utility is switch to Safe Mode, which prevents the corrupt Registry entries from launching Windows Inspection Utility.
If you use a good anti-malware scanner after deactivating Windows Inspection Utility, removing Windows Inspection Utility should be simple. However, since Windows Inspection Utility is a fresh threat, you should be ready to download any necessary threat database updates before you run the scan that detects and hopefully removes Windows Inspection Utility.

File System Modifications
- The following files were created in the system:
# File Name 1 %AppData%\Microsoft\[RANDOM CHARACTERS].exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell "%AppData%\Microsoft\[RANDOM CHARACTERS].exe"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.