Windows Inviolability System
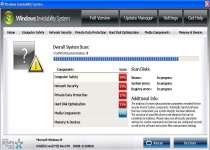 Windows Inviolability System is a rogue security application that creates an appearance of poor security on your PC to bully you into purchasing the 'full' version of Windows Inviolability System. Sadly, Windows Inviolability System lacks both threat removal or even real threat detection features and can only cause harm to your computer. Other symptoms associated with a Windows Inviolability System infection include browser hijacks and difficulty using various programs, both of which are caused by Windows Inviolability System and then blamed on nonexistent external threats. You should delete Windows Inviolability System from your PC by using an anti-virus program that actually has the security features Windows Inviolability System claims to possess.
Windows Inviolability System is a rogue security application that creates an appearance of poor security on your PC to bully you into purchasing the 'full' version of Windows Inviolability System. Sadly, Windows Inviolability System lacks both threat removal or even real threat detection features and can only cause harm to your computer. Other symptoms associated with a Windows Inviolability System infection include browser hijacks and difficulty using various programs, both of which are caused by Windows Inviolability System and then blamed on nonexistent external threats. You should delete Windows Inviolability System from your PC by using an anti-virus program that actually has the security features Windows Inviolability System claims to possess.
Windows Inviolability System: A Major Violation of Your PC Security
Windows Inviolability System may pretend to be a broad security product that monitors your network security, hard disk optimization and other aspects of your PC, but Windows Inviolability System's only real goal is to steal money and credit card information. Towards this end, even Windows Inviolability System's delivery method onto your computer is malicious, typically caused by the Fake Microsoft Security Essentials Alert Trojan.
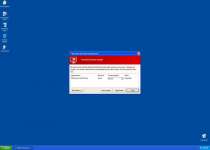
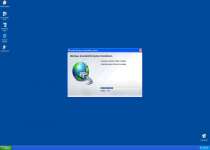
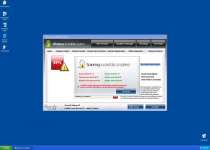
Fake Microsoft Security Essentials Alert Trojans usually will install themselves by exploiting script-based security holes in your browser. Turning off Java and Flash when they're not needed, keeping your browser updated and using updated security software can all help against attacks by this Trojan and others. The first thing Fake Microsoft Security Essentials Alert will do is create various fake error messages similar to the one below:
Microsoft Security Essentials Alert
Potential Threat Details
Microsoft Security Essentials detected potential threats that might compromise your private or damage your computer. Your access to these items may be suspended until you take an action. Click 'show details' to learn more.
After this and other fake warnings, Fake Microsoft Security Essentials Alert will install Windows Inviolability System or a similar threat. Your PC will likely be rebooted to allow Windows Inviolability System to launch itself automatically.
Windows Inviolability System's Targets Your PC After Fake Microsoft Security Essentials Alert Plays Its Part
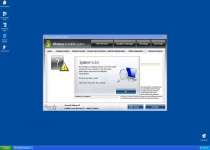
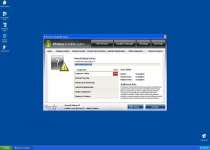
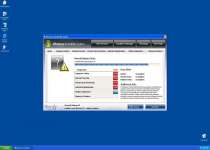
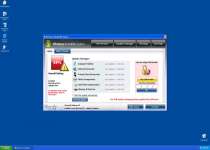
After being installed, Windows Inviolability System can launch itself without your permission and may even stay active if you attempt to close Windows Inviolability System. Windows Inviolability System will create numerous error messages regarding fake infections, but these errors serve no purpose other than to make you want to buy Windows Inviolability System's fake security software.
Examples of Windows Inviolability System errors include:
Warning!
Location: [application file path]
Viruses: Backdoor.Win32.Rbot
Warning!
Name: [application file name]
Name: [application file path]
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning.
System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can't [sic] guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update the database!
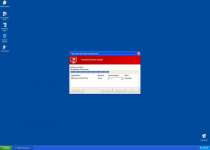
System component corrupted!
System reboot error has occurred due to lsass.exe system process failure.
This may be caused by severe malware infections.
Automatic restore of lsass.exe backup copy completed.
The correct system performance can not be resumed without eliminating the cause of lsass.exe corruption.
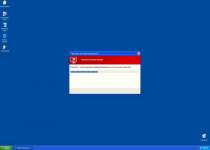
Warning! Running trial version!
The security of your computer has been compromised!
Now running trial version of the software!
Click here to purchase the full version of the software and get full protection for your PC!
Windows Inviolability System may use these warnings while blocking programs; this simple attack casts blame on a nonexistent threat while Windows Inviolability System is doing the actual harm. Security-related programs, including anti-virus scanners and basic Windows utilities, are at risk.
Windows Inviolability System use Trojans to hijack your web browser. Signs of this particular Windows Inviolability System attack include a strange homepage, pop-ups, search results that have been tampered with and unusual errors when you attempt to access websites.
Many Windows Inviolability System hijacks may attempt to redirect you to Windows Inviolability System's homepage, or to the homepage of one of Windows Inviolability System's relatives. Related threats include Windows AV Component, Windows Microsoft Guardian, Windows Necessary Firewall and Windows Verifying Center.
Removing Windows Inviolability System without expert assistance can be a challenge due to the Registry changes that Windows Inviolability System makes, as well as the possible presence of Trojans and other threats. In most cases, using anti-virus software to delete Windows Inviolability System is the best solution.

File System Modifications
- The following files were created in the system:
# File Name 1 %UserProfile%\Application Data\Microsoft\[RANDOM CHARACTERS].exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
Additional Information on Windows Inviolability System
- The following messages's were detected:
# Message 1 Microsoft Security Essentials Alert
Potential Threat Details
Microsoft Security Essentials detected potential threats that might compromise your private or damage your computer. Your access to these items may be suspended until you take an action. Click ‘show details’ to learn more.2 System reboot error has occurred due to lsass.exe system process failure.
This may be caused by severe malware infections.
Automatic restore of lsass.exe backup copy completed.
The correct system performance can not be resumed without eliminating the cause of lsass.exe corruption.3 Threat prevention solution found
Security system analysis has revealed critical file system vulnerability caused by severe malware attacks.
Risk of system files infection:
The detected vulnerability may result in unauthorized access to private information and hard drive data with a serious possibility of irreversible data loss and unstable PC performance. To remove the malware please run a full system scan. Press ‘OK’ to install the software necessary to initiate system files check. To complete the installation process please reboot your computer
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.