Windows Precautions Center
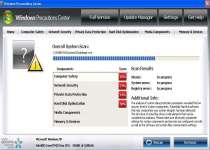 As a cheap copy of other rogue security programs, Windows Precautions Center creates fake pop-up alerts and other forms of deceitful information that make it look like your PC is heavily infected. Windows Precautions Center can infect your PC by using a Trojan that fakes Microsoft Security Essentials Alert errors and may run without your permission every time you start your computer. Windows Precautions Center may hijack your web browser or prevent you from using a range of applications and is a serious security risk to your PC.
As a cheap copy of other rogue security programs, Windows Precautions Center creates fake pop-up alerts and other forms of deceitful information that make it look like your PC is heavily infected. Windows Precautions Center can infect your PC by using a Trojan that fakes Microsoft Security Essentials Alert errors and may run without your permission every time you start your computer. Windows Precautions Center may hijack your web browser or prevent you from using a range of applications and is a serious security risk to your PC.
Readily Observable Attacks Associated with Windows Precautions Center
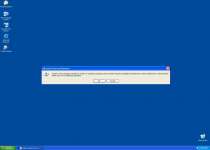
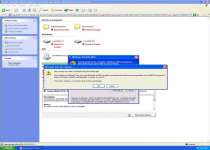
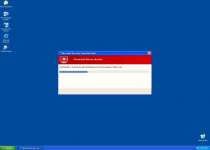
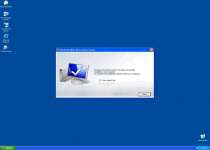
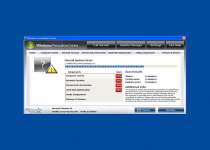
Since Windows Precautions Center is a copy of other threats like Windows Tasks Optimizer, Windows Tweaking Utility, Windows Processes Organizer and Windows Oversight Center, it should come as no surprise that Windows Precautions Center uses similar tricks to infect new PCs. Windows Precautions Center spreads with the assistance of a Fake Microsoft Security Essentials Alert Trojan that creates alerts like the ones that you see here:
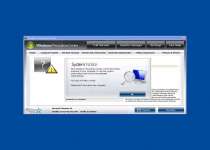
Microsoft Security Essentials Alert
Potential Threat Details
Microsoft Security Essentials detected potential threats that might compromise your private or damage your computer. Your access to these items may be suspended until you take an action. Click 'show details' to learn more.
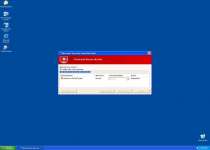
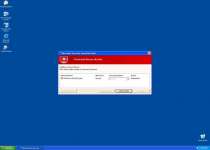
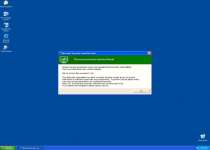
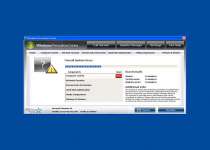
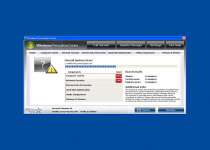
Threat prevention solution found
Security system analysis has revealed critical file system vulnerability caused by severe malware attacks.
Risk of system files infection:
The detected vulnerability may result in unauthorized access to private information and hard drive data with a seriuos [sic] possibility of irreversible data loss and unstable PC performance. To remove the malware please run a full system scan. Press 'OK' to install the software necessary to initiate system files check. To complete the installation process please reboot your computer.
This is followed up by a threat of a Trojan and then the installation of Windows Precautions Center or a related rogue security program. Your computer will reboot to finalize installation, and this will let Windows Precautions Center launch itself automatically through the use of malicious Registry exploits.
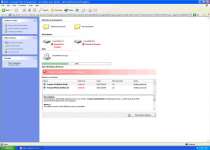
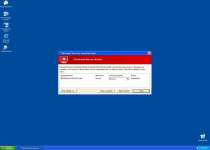
Errors you might see from Windows Precautions Center itself include:
System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
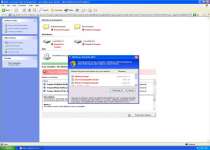
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can't [sic] guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update the database!
System component corrupted!
System reboot error has occurred due to lsass.exe system process failure.
This may be caused by severe malware infections.
Automatic restore of lsass.exe backup copy completed.
The correct system performance can not be resumed without eliminating the cause of lsass.exe corruption.
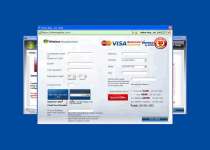
Warning! Running trial version!
The security of your computer has been compromised!
Now running trial version of the software!
Click here to purchase the full version of the software and get full protection for your PC!
Warning!
Name: [application file name]
Name: [application file path]
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning.
Warning!
Location: [application file path]
Viruses: Backdoor.Win32.Rbot
Alerts from Windows Precautions Center and Windows Precautions Center's delivering Trojan are erroneous, since neither of these invading programs try to scan your computer. Instead, Windows Precautions Center and Windows Precautions Center's cohorts are content to create fake alerts without checking to see what the real health of your system is like.
Windows Precautions Center: More Than Just an Error Generator
There are several other common attacks that Windows Precautions Center may make on your PC:
- Windows Precautions Center may hijack your web browser. Hijacks can imitate unsafe website errors to constrict your access to websites and are also used to force you to visit malicious websites.
- Windows Precautions Center may also cancel downloads to impede your ability to find suitable anti-malware applications. In some cases, renaming the file to a generically-allowed file name like 'explorer.exe' or 'iexplore.exe' will cause the download to slide under Windows Precautions Center's detection filter.
- Windows Precautions Center may also stop you from using different programs, with likely targets consisting of anti-malware scanners and Windows maintenance utilities like Task Manager. The same file-renaming trick may also work in this instance.
If you're still experiencing these attacks, don't try to remove Windows Precautions Center just yet. Instead, reboot your computer into Safe Mode or use another alternate boot option that stops Windows Precautions Center from launching itself. Only then should you use an anti-malware scanner to delete Windows Precautions Center from your PC.
File System Modifications
- The following files were created in the system:
# File Name 1 %UserProfile%\Application Data\Microsoft\[RANDOM CHARACTERS].exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell "%AppData%\Microsoft\[RANDOM CHARACTERS].exe"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_CURRENT_USER\Software\Windows Precautions CenterHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Windows Precautions CenterHKEY_LOCAL_MACHINE\Software\[APPLICATION]\Microsoft\Windows\CurrentVersion\Uninstall..{Uninstaller}Windows Precautions Center
Additional Information on Windows Precautions Center
- The following messages's were detected:
# Message 1 Safe Boot includes several tools allowing the operational system to better control application software, so that to achieve enhanced security and system stability. These elements make it possible for the operational system to perform tasks otherwise not feasible without relevant hardware support 2 Microsoft Security Essentials Alert
Potential Threat Details
Microsoft Security Essentials detected potential threats that might compromise your private or damage your computer. Your access to these items may be suspended until you take an action. Click 'show details' to learn more.3 System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Warning!
Location: c:\windows\system32\taskmgr.exe
Viruses: Backdoor.Win32.Rbot4 Threat prevention solution found
Security system analysis has revealed critical file system vulnerability caused by severe malware attacks.
Risk of system files infection:
The detected vulnerability may result in unauthorized access to private information and hard drive data with a serious possibility of irreversible data loss and unstable PC performance. To remove the malware please run a full system scan. Press ‘OK’ to install the software necessary to initiate system files check. To complete the installation process please reboot your computer.5 System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.