Windows Protection Alarm
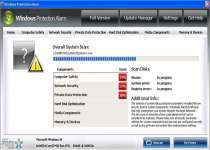 Windows Protection Alarm is a rogue anti-virus and security program that creates fake infection warnings and fake grades for your PC security. Windows Protection Alarm requests money for a registration process in exchange for fixing problems on your computer, but Windows Protection Alarm will actually cause problems like browser hijacks and program crashes instead of fixing them. You should remove Windows Protection Alarm by preventing Windows Protection Alarm from running and then using a suitably advanced anti-malware scanner.
Windows Protection Alarm is a rogue anti-virus and security program that creates fake infection warnings and fake grades for your PC security. Windows Protection Alarm requests money for a registration process in exchange for fixing problems on your computer, but Windows Protection Alarm will actually cause problems like browser hijacks and program crashes instead of fixing them. You should remove Windows Protection Alarm by preventing Windows Protection Alarm from running and then using a suitably advanced anti-malware scanner.
How Windows Protection Alarm Gets from the Internet to Your PC
Windows Protection Alarm is one of many possible payloads that are installed (or 'dropped') by the Fake Microsoft Security Essentials Alert. Other possible rogue security programs that can be installed by this Trojan include Windows Risks Preventions, Windows Necessary Firewall, Windows Salvage System and Windows Custom Settings.
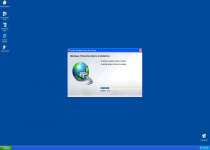
The initial Windows Protection Alarm installation process is heralded by fake Security Essentials Trojans that are similar to this sample:
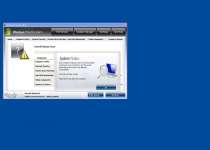
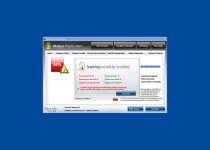
Threat prevention solution found
Security system analysis has revealed critical file system vulnerability caused by severe malware attacks.
Risk of system files infection:
The detected vulnerability may result in unauthorized access to private information and hard drive data with a seriuos [sic] possibility of irreversible data loss and unstable PC performance. To remove the malware please run a full system scan. Press 'OK' to install the software necessary to initiate system files check. To complete the installation process please reboot your computer.
Other messages related to Fake Microsoft Security Essentials Alert Trojans include warnings about inadequate security software or warnings about the presence of a fake Trojan threat. The Fake Microsoft Security Essentials Alert Trojan will proceed to install Windows Protection Alarm or another threat and reboot your PC. After that, Fake Microsoft Security Essentials Alert hands the reigns over to Windows Protection Alarm.
Why Windows Protection Alarm Should Set Off Your Internal Alarm?
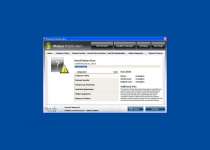
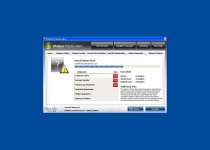
Startup Registry entries let Windows Protection Alarm run automatically with Windows. One of the first things you'll see is a window that pretends to grade your PC security, including aspects like 'network safety' and 'private data protection.' Most or all grades will be negative, but since Windows Protection Alarm doesn't try to analyze your computer, in the first place you can ignore these inaccurate scores.
Windows Protection Alarm may also attack your PC by:
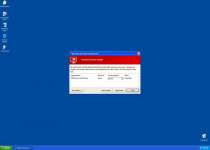
- Blocking programs, with or without error messages such as the ones shown here:
Warning!
Location: [application file path]
Viruses: Backdoor.Win32.RbotWarning!
Name: [application file name]
Name: [application file path]
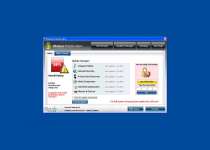
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning. - Create fake errors at random, purely to make you think that your computer will self-destructs without Windows Protection Alarm's help. Here are just two of the other errors that you might see:
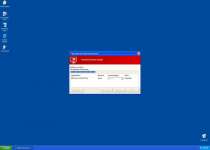
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can't [sic] guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update the database!System component corrupted!
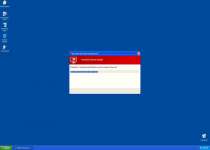
System reboot error has occurred due to lsass.exe system process failure.
This may be caused by severe malware infections.
Automatic restore of lsass.exe backup copy completed.
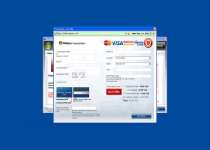
The correct system performance can not be resumed without eliminating the cause of lsass.exe corruption. - Hijack your web browser to redirect you to the Windows Protection Alarm home site and steal your credit card information. Hijacks can also block website access by creating fake error pages or redirecting you away from destinations that Windows Protection Alarm doesn't want you to visit.
Removing Windows Protection Alarm's will solve all of these problems, but you should only attempt to remove Windows Protection Alarm's by using anti-malware programs that can safely delete all components with few to no side effects. In most cases, Safe Mode or booting your OS from a CD is also recommended.
File System Modifications
- The following files were created in the system:
# File Name 1 %UserProfile%\Application Data\Microsoft\[random].exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.