Magic Malware
Posted: April 18, 2013
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 2,258 |
|---|---|
| Threat Level: | 2/10 |
| Infected PCs: | 46,805 |
| First Seen: | April 18, 2013 |
|---|---|
| Last Seen: | October 17, 2023 |
| OS(es) Affected: | Windows |
The Magic malware is a spyware program that's distributed in targeted attacks at business-oriented PCS, with an emphasis on infiltrating business systems in the United Kingdom. What makes Magic malware worthy of its name is the remarkable feat of its having evaded detection for roughly a year while still infecting countless PCs in the UK and other nations. With the ability to alter your browser's web page displays, steal confidential data and set up backdoor vulnerabilities, Magic malware is a high-level PC threat, and SpywareRemove.com malware research team recommends using suitably powerful anti-malware software to delete Magic malware or detect its attempted installation through common infection vectors.
The Sinister Sorcery Behind the Magic Malware
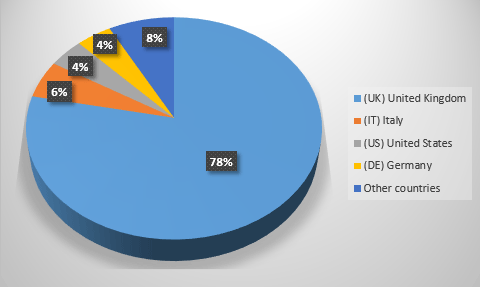
Magic malware is a rich, multifaceted Trojan that includes characteristics of both spyware and backdoor Trojans. Although Magic malware's infection methods have yet to be examined, SpywareRemove.com malware experts caution that most industrial-targeting PC threats utilize some means of distributing themselves through spam e-mail messages, local networks and removable hard drive-based devices. Based on current information, SpywareRemove.com malware research team notes that businesses in the United Kingdom are particularly at risk for Magic malware infections, and already make up nearly eighty percent of Magic malware's estimated total for compromised PCs thus far.
SpywareRemove.com malware researchers consider Magic malware's method of backdoor server communication to be the feature that's most worthy of being highlighted. Unlike most backdoor Trojans, which allow criminals to control your PC through a standard HTTP protocol-based connection, Magic malware uses a custom protocol with a so-called 'magic code' at the start of each instance of communication. This unusual feature is what allowed Magic malware to avoid being identified for so long even while infecting thousands of computers operating in the education, financial and telecommunications sectors.
Eying the Other Cards that Magic Malware has Up Its Sleeve
Besides granting criminals the ability to control your computer through its innovative backdoor connection, Magic malware also can be used to commit attacks like the following:
- Installing other types of malware that may include diverse and specialized functions distinct from Magic malware 's own attacks.
- Stealing sensitive information, potentially including passwords and other encrypted data.
- Injecting additional HTML content into your browser, which allows Magic malware to insert malicious content for multiple purposes. For example, SpywareRemove.com malware experts have noted that banking Trojans often abuse this attack for the purpose of phishing for additional personal information, with their attacks disguised as new bank security procedures.
Given its obviously difficult to detect nature, Magic malware should be identified by dedicated anti-malware products whenever this is possible. Deleting Magic malware without the assistance of such software is unlikely – particularly in light of the other PC threats that Magic malware also may install.
Figure 1 - Magic Malware infection percentages by top regions. Source: itproportal.com
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.