Rocra/Red October Malware
Posted: January 15, 2013
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 2,448 |
|---|---|
| Threat Level: | 2/10 |
| Infected PCs: | 54,074 |
| First Seen: | January 15, 2013 |
|---|---|
| Last Seen: | October 16, 2023 |
| OS(es) Affected: | Windows |
 Red October malware, also known as Rocra, is a worldwide malware phenomenon that, like Stuxnet or Flame, appears to have been designed for the explicit purpose of corporate and government espionage. Like equally-sophisticated PC threats, Red October uses multiple modules to conduct its attacks, including 'throw away' components that are designed to attack your PC and then be deleted to avoid detection by your security software. Major infection vectors for Red October utilize e-mail-distributed text documents that double as Trojan droppers, and SpywareRemove.com malware researchers emphasize that countries in eastern Eurasia specifically are being targeted by these Red October attacks. Red October's functions are designed to steal highly confidential information from both PCs, as well as many associated devices – such as mobile phones – and should be considered a high-level PC threat. You should delete Red October infections with the most powerful anti-malware software at your disposal whenever possible.
Red October malware, also known as Rocra, is a worldwide malware phenomenon that, like Stuxnet or Flame, appears to have been designed for the explicit purpose of corporate and government espionage. Like equally-sophisticated PC threats, Red October uses multiple modules to conduct its attacks, including 'throw away' components that are designed to attack your PC and then be deleted to avoid detection by your security software. Major infection vectors for Red October utilize e-mail-distributed text documents that double as Trojan droppers, and SpywareRemove.com malware researchers emphasize that countries in eastern Eurasia specifically are being targeted by these Red October attacks. Red October's functions are designed to steal highly confidential information from both PCs, as well as many associated devices – such as mobile phones – and should be considered a high-level PC threat. You should delete Red October infections with the most powerful anti-malware software at your disposal whenever possible.
From Cinema to Reality: the Espionage Attack that Will Have Your PC Reeling
Red October was only identified and analyzed by PC security companies relatively recently, although related domain data has led some leading malware analysts to suspect that the Red October campaign has been ongoing for at least half a decade, if not longer than that. Although Red October is highly likely to include other distribution mechanisms, its main form of reproduction appears to be through carefully-targeted e-mail messages that include Word documents that install Red October. SpywareRemove.com malware researchers have noted that said documents, although they appear to be benign, actually utilize multiple exploits that are common to Microsoft Office software, and install Red October without any visible symptoms of the attack.
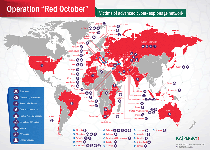
Most Red October attacks appear to target Russia-based institutions, although other eastern Eurasian countries are especially at risk. SpywareRemove.com malware experts also have seen cases of Red October infections in other countries (including Italy and the United States) that appear to be indicative of a global espionage scheme undertaken by a well-funded and organized central party.
One key to understanding the danger that Red October represents is grasping the breadth of its potential victims. In addition to attacking and stealing information from normal Windows PCs, Red October also may target e-mail databases, mobile phones, network-related devices and other types of hardware – particularly Windows and Nokia brands. Because Red October's e-mails are designed for specific government and company employees, instead of being spammed out randomly, their contents may appear to be believable and will not show any obvious signs of including malicious file attachments.
What's at Risk When Red October Comes Calling
Once the faux text document installs Red October, Red October can run a wide range of functions that are designed to compromise your PC secretively and steal personal information – even including highly-secure information that would be considered critical to corporate or government operations. SpywareRemove.com malware experts also emphasize the modular design of Red October, which allows Red October to create and discard components as they're necessary for various attacks. Some of the most significant Red October-related attacks include (but are not limited to):
- Theft of Windows user account information.
- Stealing network security and configuration-related data.
- Keylogging (recording your keyboard input or typing).
- Gathering e-mail addresses from Microsoft Outlook and other 'address book' style sources.
- Screengrabbing (taking screenshots without your consent).
- Collecting general system information that can be exploited in other attacks.
- Theft of browser-related information, including your web-browsing history and passwords for various website accounts.
Even files that are protected by encryption or (in some cases) deleted can be stolen by Red October. Red October also possesses a routine that allows Red October to fake a disinfection and then reinstall itself in its entirety.
SpywareRemove.com malware researchers strongly recommend that you use the best and most updated anti-malware equipment that's available for removing Red October, which is an advanced PC threat with well-developed defenses. On the bright side, there aren't any signs so far of Red October being able to compromise Mac or Linux-based PCs, although such brands have been targeted by similar attacks from other sources.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.