Trojan.Shadowlock
Posted: July 9, 2013
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 9/10 |
|---|---|
| Infected PCs: | 14 |
| First Seen: | July 9, 2013 |
|---|---|
| Last Seen: | March 7, 2020 |
| OS(es) Affected: | Windows |
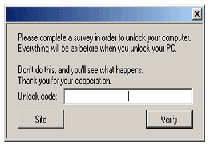 Shadowlock is a Survey ransomware Trojan, similar to the 'Your System is Locked' Ransomware, the Survey Warning Ransomware, the 'Please complete a quick survey to continue' Virus or the 'Complete an offer to continue' Virus. Like most types of ransomware, Shadowlock locks some major aspects of your PC and requests that you perform certain actions to unlock it. However, instead of asking for money, Shadowlock requests that you fill out an offer. While this may seem less dangerous than giving Shadowlock's criminals your money out of pocket, SpywareRemove.com malware experts still discourage any submission to ransomware extortion, and encourage disabling and then deleting Shadowlock with all of the standard anti-malware techniques and software.
Shadowlock is a Survey ransomware Trojan, similar to the 'Your System is Locked' Ransomware, the Survey Warning Ransomware, the 'Please complete a quick survey to continue' Virus or the 'Complete an offer to continue' Virus. Like most types of ransomware, Shadowlock locks some major aspects of your PC and requests that you perform certain actions to unlock it. However, instead of asking for money, Shadowlock requests that you fill out an offer. While this may seem less dangerous than giving Shadowlock's criminals your money out of pocket, SpywareRemove.com malware experts still discourage any submission to ransomware extortion, and encourage disabling and then deleting Shadowlock with all of the standard anti-malware techniques and software.
Shadowlock: a Lockdown Slightly More Substantial Than Some Summer Shade
Although Shadowlock has a feature set that's perfectly capable of enacting additional attacks, Shadowlock currently only is used as a simple Survey ransomware Trojan that blocks a few applications while also requesting that you fill out its offers. Instead of blocking most applications indiscriminately, SpywareRemove.com malware experts can confirm that Shadowlock only blocks a few programs that, nonetheless, are crucial for maintaining your PC's security. Task Manager, the Registry Editor and similar Windows-centric tools all are blocked by Shadowlock as long as Shadowlock is active – which Shadowlock will be by default until you take steps to disable Shadowlock. After a reboot, any programs blocked by Shadowlock can still be accessed before Shadowlock's pop-up loads – a process that usually takes around twenty seconds.
Shadowlock displays an 'offer' window automatically when Windows restarts, which supposedly allows you to unlock your computer once it's completed. Offers given by Shadowlock Trojans can be used to steal personal information, expose you to malicious web content or indulge in other attacks against your PC, and, as such, should always be avoided. Shadowlock's pop-up offer refuses to terminate like a normal pop-up and, interestingly, will reboot your computer if you enter an incorrect unlock code too many times. SpywareRemove.com malware researchers also are somewhat concerned over Shadowlock's ability to maintain itself through a traditional System Restore.
Where the Real Gloom in Shadowlock Lies
While its basic attacks are sufficient to rate Shadowlock as, at least, a mid-level security threat, SpywareRemove.com malware researchers are even more worried about the functions that Shadowlock has not been found using so far, despite their inclusion in its code. The abilities to disable the Windows Firewall, change your mouse settings, open programs automatically and terminate your web browser all are meaningful security issues that are indicative of Shadowlock being in a mere state of partial deployment, with more advanced attacks anticipated in the future.
While the shadow that Shadowlock casts on your desktop certainly can be called a dark one, all of the usual anti-malware strategies for combatting ransomware also should be effective against Shadowlock. You should disable Shadowlock by any means necessary and then delete Shadowlock with a tried-and-tested anti-malware product. This will unlock your computer without requiring you to fill out any of Shadowlock's (most likely fraudulent) offers.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\Cores.exe
File name: %AppData%\Cores.exeMime Type: unknown/exe
Group: Malware file
%AppData%\tmps.tmp
File name: %AppData%\tmps.tmpFile type: Temporary File
Mime Type: unknown/tmp
Group: Malware file
%Temp%\[5 RANDOM LETTERS].exe
File name: %Temp%\[5 RANDOM LETTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\"Cores" = "%AppData%\Cores.exe"
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.