Windows Problems Protector
Posted: February 2, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 14 |
| First Seen: | February 3, 2011 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
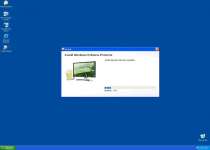
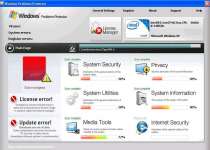 Despite the benign name, Windows Problems Protector is anything but a solution to your computer's woes. Coming to the Internet through the very same people who've designed many other malware infections, Windows Problems Protector is pure malware that should be eliminated with extreme prejudice. While its error messages and behavior may terrify those unready for it, the prepared will find Windows Problems Protector relatively easy to spot and eradicate.
Despite the benign name, Windows Problems Protector is anything but a solution to your computer's woes. Coming to the Internet through the very same people who've designed many other malware infections, Windows Problems Protector is pure malware that should be eliminated with extreme prejudice. While its error messages and behavior may terrify those unready for it, the prepared will find Windows Problems Protector relatively easy to spot and eradicate.
Peeking Behind the Veil of This So-Called 'Protector'
Like quite a few other rogue software 'products', Windows Problems Protector originates from the Russian Federation. In fact, it was made by the same people who made malware like WindowsShieldCenter and Windows System Optimizator. As a partner in crime with similar malware, it's a recent 2011 innovation and tends to be distributed by one particular kind of Trojan, fake Microsoft Security Essentials Alert Malware. This host Trojan chooses from a whole menu of different rogues. Should Windows Problems Protector be the one it slops onto your hard drive, you will know about it pretty quickly, because it will bring your computer activities to a dead halt.
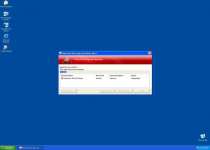
The initial installation occurs when the Trojan ironically informs you that it has detected a Trojan infection! A fake scan prompt will further indicate that the Trojan.Horse.Win32.PAV.64.a infection was found and that Windows Problems Protector or another rogue security program should be installed to take care of the threat. Here, it's important to remember that this Trojan isn't able to detect true infections and is simply using fear-mongering to earn your trust.
If you disregard these false warnings, you still have the initial Trojan to deal with, but you do not have Windows Problems Protector mucking up your system. Only by agreeing to install it will Windows Problems Protector typically be installed. After that, your computer will be rebooted.
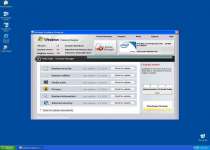
After Windows Problems Protector Makes Itself Cozy
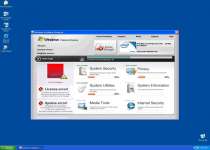
Getting back to your operating system will show that Windows Problems Protector has grabbed most of your screen real estate. Take a deep breath and keep your head; the rogue program will let you get back to your usual desktop after you close it. Ignore Windows Problems Protector's encouragement for you to waste time on the scan, since the scanning process is just as fake this time as it was with the hosting Trojan.
Once on your system and running, Windows Problems Protector has two primary ways of scaring you into throwing your money away on it:
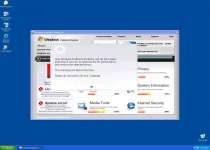
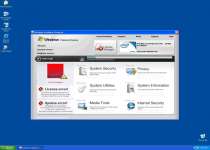
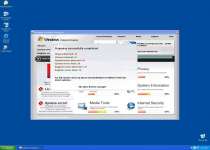
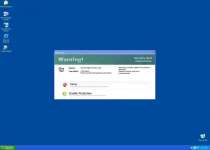
The first scheme Windows Problems Protector has in store for you is a second helping of fake error messages. These take a word variety of ominous but entirely deceitful forms, such as suggesting that your registry has been altered, that your web browser has a keylogger, or that a critical system file has failed and been backed up. These messages are all quite worthless, since Windows Problems Protector is no more capable of detecting these problems than your mouse is capable of flying to the moon.
Windows Problems Protector's fall-back plan is more brutal than its simple lies. Like many other rogue programs, especially those distributed in a similar manner, it will also disable certain programs to protect itself from being deleted, or simply to alarm the user. As a rule of thumb, if something bad happens, it's safe to assume Windows Problems Protector's at fault.
No matter how bad things get, the last thing you do not want is to give your money to a rogue security program. Windows Problems Protector has no services or help to give you, so save your dollars! By keeping a level head and following through with removal instructions for both Windows Problems Protector and Fake Microsoft Security Essentials, you can restore your system to tip-top shape.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\cahhlo.exe
File name: cahhlo.exeSize: 2.41 MB (2413568 bytes)
MD5: ee216a9e48874b1f899488ba6a726e5b
Detection count: 21
File type: Executable File
Mime Type: unknown/exe
Path: %AppData%
Group: Malware file
Last Updated: January 8, 2020

Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.