Windows Utility Tool
Posted: January 21, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 5 |
| First Seen: | January 21, 2011 |
|---|---|
| Last Seen: | April 18, 2018 |
| OS(es) Affected: | Windows |
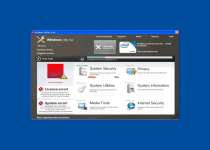
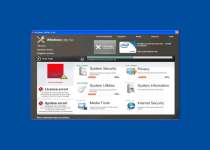
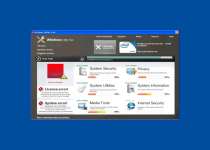
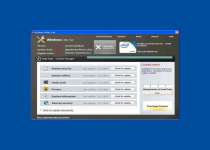
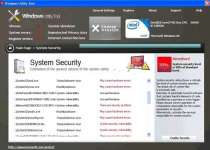 Windows Utility Tool is a close relative of many other preexisting rogue anti-spyware products and has no use other than enabling criminals access to your money and information on your system. Windows Utility Tool shares a Trojan-based delivery mechanism with many other rogue anti-spyware products, and may be installed through misleading error messages. Windows Utility Tool has no positive traits that make it worth keeping around on your computer, and will constantly interfere with your computer use through false positive infection messages, so go ahead and delete Windows Utility Tool when you get the chance.
Windows Utility Tool is a close relative of many other preexisting rogue anti-spyware products and has no use other than enabling criminals access to your money and information on your system. Windows Utility Tool shares a Trojan-based delivery mechanism with many other rogue anti-spyware products, and may be installed through misleading error messages. Windows Utility Tool has no positive traits that make it worth keeping around on your computer, and will constantly interfere with your computer use through false positive infection messages, so go ahead and delete Windows Utility Tool when you get the chance.
The Rogue Product Payload Arrives
The infection method for Windows Utility Tool can vary somewhat, but the currently prevalent method is through the Microsoft Security Essentials Alert Malware. This prolific Trojan serves as the enabler for rogue anti-spyware products like Windows Utility Tool. At first, Windows Utility Tool will get onto your system undetected. Then the Trojan creates a series of fake error message that detect another supposed Trojan infection? Trojan.Horse.Win32.PAV.64.a. This infection does not exist and is just used to encourage users to install Windows Utility Tool or another rogue anti-spyware product.
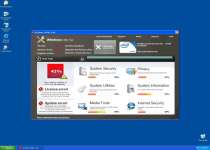
The installation of Windows Utility Tool heralds quite a bit of unpleasantness for your poor machine, since the rogue anti-spyware product has no adherence for the boundaries of legitimate anti-malware products. Windows Utility Tool will alter your registry so that Windows Utility Tool displays itself, along with a scan prompt, before you can even get to your desktop. This insistence puts Windows Utility Tool at the forefront of your computer usage during startup, but that's only the beginning.
The Total (and Totally Unpleasant) Windows Utility Tool Experience
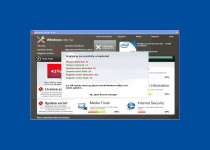
Trojan.Horse.Win32.PAV.64.a's abuse of your trust may begin with meddling in your registry file, but it hardly stops there. Its persistent scanning requests only result in groundless displays of predetermined results that Trojan.Horse.Win32.PAV.64.a shows without actually attempting to scan your computer. Besides using fake scans, Trojan.Horse.Win32.PAV.64.a will also support its deception with error messages, and may even crash programs to make these errors seem real. The contents of these messages will often be reused from other rogue anti-spyware products, and include such poisonous treats as:
System component corrupted!
System reboot error has occurred due to lsass.exe system process failure.
This may be caused by severe malware infections.
Automatic restore of lsass.exe backup copy completed.
The correct system performance can not be resumed without eliminating the cause of lsass.exe corruption.
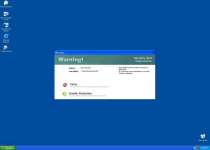
System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Warning!
Name: firefox.exe
Name: c:\program files\firefox\firefox.exe
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning.
System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
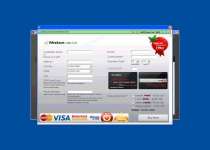
In all cases, these errors are fabricated by Windows Utility Tool so that you'll buy it, giving the criminals behind the rogue anti-spyware product both money and access to private information. Distrust any alarming errors you see on your computer until you've deleted Windows Utility Tool and the Trojan that opened the door for this rogue scanner. Other problems that can result from harboring Windows Utility Tool include but are not restricted to:
- Excessive memory usage.
- The automated installation of other malware.
- Keylogging and other information-stealing spyware activities.
- Browser hijacking, especially to redirect you towards the Windows Utility Tool website.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\dovibt.exe
File name: dovibt.exeSize: 2.33 MB (2333184 bytes)
MD5: a0424f1b2e6c5ed0d51d415bcaa6e7b2
Detection count: 21
File type: Executable File
Mime Type: unknown/exe
Path: %AppData%
Group: Malware file
Last Updated: January 21, 2011
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.