The ‘Friendly’ CoinVault Ransomware Decrypts One File for Free
Hackers are like annoying little pests that may occasionally attempt to give computer users what they want, only to later discover that the little satisfaction has lead to a dead end. In the latest actions of the CoinVault ransomware, this is exactly what is taking place with a not-so-friendly outcome.
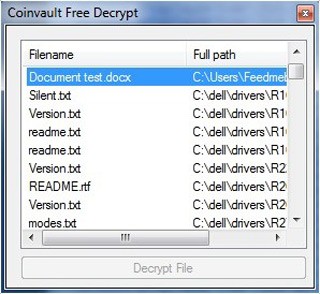
In a twisted "good faith" maneuver, the creators of CoinVault ransomware are allowing its victims to decrypt one file for free in hopes of convincing its victims to pay to unlock the other ransomed files. Similar to other file-encrypting ransomware, CoinVault encrypts documents, pictures, archives, ISO and videos files to make you pay for decryption. Yet, what makes CoinVault stand out from the rest of the ransomware is that it allows victims to view an encrypted files list and select one file they can decrypt for free (Image 1).
Unlike other famous ransomware like CryptoWall or CryptoLocker, which rely on asymmetric encryption, CoinVault uses the employment of a 256-bit AES symmetric encryption with private keys for both encrypting and decrypting located on a remote server, and it stops the Windows Volume Shadow Copy Service so victims can't use it to unlock their files.
Image 1. CoinVault allows you to make one freebie decryption to assure victims that eventually the tool will restore locked files. - Source: Webroot
A concise and to-the-point decryption ransom message is provided in CoinVault's interface:
'Your personal documents and files on this computer have just been encrypted.
The original files have been deleted and will only be recovered by following the steps described below: Click on "View encrypted files" to see a list of files that got encrypted.
The encryption was done using a unique generated encryption key (using AES-256). This means the encrypted files are of no use until they get decrypted using a key stored on a server. This server will only release this key if the amount of Bitcoins (displayed left of this windows) is sent to the Bitcoin address underneath this windows.'
Image 2. CoinVault ransomware interface - Source: Webroot
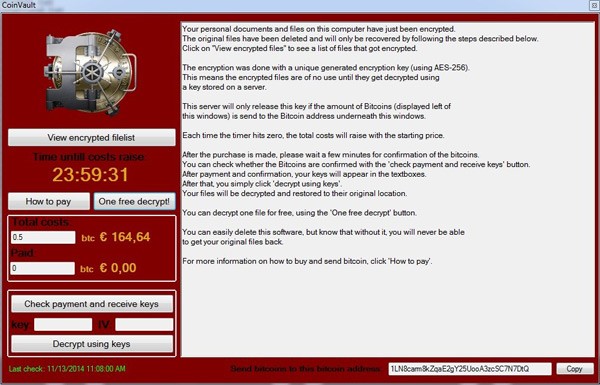
As ransomware extortion methods go, you must pay to decrypt your files, and in this case, CoinVault only supports Bitcoin as a payment method. Victims are asked to pay 0.5 Bitcoins (that is $200 at the current exchange rate) to get the key that decrypts their locked files. As time passes by, the cost increases every 24 hours. You are provided with a 24-hour countdown timer and a payment check mechanism for the victim's convenient. Also, CoinVault's handlers provided a link to the Bitcoin wallet address in order to stick with the friendly approach.
Security experts advise users not to pay the ransom because it will discourage such extortion practices. Users are advised not to open links, download or open files residing in spam emails as it is the most common way of spreading malware. To counter ransomware attacks, you should make regular backups of you important files and keep an updated anti-virus solution.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.