CryptoLocker Ransomware
Posted: September 11, 2013
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 16,983 |
|---|---|
| Threat Level: | 10/10 |
| Infected PCs: | 1,712 |
| First Seen: | September 11, 2013 |
|---|---|
| Last Seen: | October 12, 2023 |
| OS(es) Affected: | Windows |
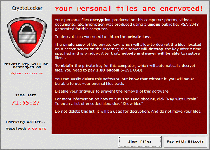
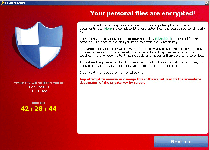 CryptoLocker, also identified as Trojan:Win32/Crilock.A, is a Windows locker Trojan that modifies a range of files on your PC to make them temporarily unusable and demands that you pay a fee before you can acquire the key to decrypt the affected files. As an added incentive to submit to CryptoLocker's ransom, CryptoLocker also warns that any attempt to remove the infection from your PC will cause the associated key to be deleted. Despite these threats, SpywareRemove.com malware experts consider it unlikely that criminals would bother to restore any affected PCs to normal after receiving their illegal payments, and continue to recommend the use of standardized anti-malware programs and decryption technology for combating CryptoLocker and all similar PC threats.
CryptoLocker, also identified as Trojan:Win32/Crilock.A, is a Windows locker Trojan that modifies a range of files on your PC to make them temporarily unusable and demands that you pay a fee before you can acquire the key to decrypt the affected files. As an added incentive to submit to CryptoLocker's ransom, CryptoLocker also warns that any attempt to remove the infection from your PC will cause the associated key to be deleted. Despite these threats, SpywareRemove.com malware experts consider it unlikely that criminals would bother to restore any affected PCs to normal after receiving their illegal payments, and continue to recommend the use of standardized anti-malware programs and decryption technology for combating CryptoLocker and all similar PC threats.
CryptoLocker: a File Lockdown on a Countdown to Data Storage Doom
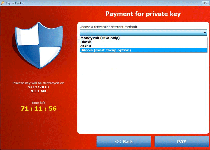
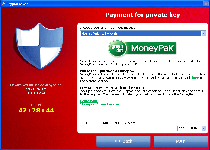
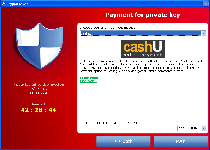
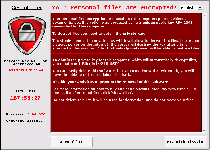
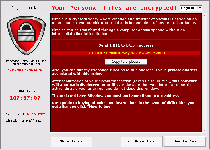
CryptoLocker is one of the relatively rare types of ransomware that follow up on their threats of encrypting the files on your PC, as opposed to threatening to do so and then using a pop-up alert to block your Windows access in general. Similar Trojans that perform approximately the same attacks include Trojan.Ransomcrypt.E, Win32:Ransom-AOQ, 'Say Hello To Little Virus Brings A Lot Of Problems' Ransomware and the ArchiveLock Trojan. Like most other PC threats of its type, CryptoLocker informs you of the attack by displaying a warning message that demands payment of a criminal's ransom fee – in this case, one approximating one hundred USD. This pop-up can block access to your desktop, which causes CryptoLocker also to be referred to as a Windows locker or Winlocker Trojan.
CryptoLocker doesn't try to portray itself as an arm of any kind of law enforcement agency, but its file encryption attack does prevent you from using the affected files and has the added urgency of a countdown timer until the offered ransom solution is withdrawn. CryptoLocker's encryption attack, a basic attack that re-arranges file data to make the files inoperable without deleting their contents, targets media and text files such TXT, JPG and AVI. Note that any applicable files on removable devices also are affected by the encryption attack.
Beating a File-Locker at Its Own Game
Although CryptoLocker takes significant time to make it seem like paying criminals is the only way to get your files returned to you safe and sound, SpywareRemove.com malware research team can suggest several alternative ways of coping with a CryptoLocker infection. Free decryption utilities are available from a variety of sources and may be used to try to undo the file encryption attack of CryptoLocker, and anti-malware applications can be used to remove CryptoLocker itself. However, if, as is recommended, you keep your files backed up to a safe source such as a writable DVD, CryptoLocker's attack can be ignored entirely – since you simply can restore all affected files from your backup without bothering to undo the encryption.
Because of the high stakes in any CryptoLocker infection, avoiding CryptoLocker is especially recommended as even preferable to removing CryptoLocker from your PC safely. Previous attacks by similar high-level PC threats have been known to use corrupted websites hosting drive-by-download attacks and/or disguised e-mail attachments, which can be blocked by the combined security of strong browser security features and anti-malware tools with Web-monitoring features.



Aliases
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Microsoft\Crypto\sysgop.exe
File name: sysgop.exeSize: 276.88 KB (276883 bytes)
MD5: 3c282af747b4f70340dca3170d55ae29
Detection count: 578
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%\Microsoft\Crypto
Group: Malware file
Last Updated: July 18, 2020
C:\Users\<username>\AppData\Local\Microsoft\Performance\Monitor\temp\tmp9927.exe
File name: tmp9927.exeSize: 404.51 KB (404513 bytes)
MD5: eb2cde846127106689d14afe7911bcec
Detection count: 354
File type: Executable File
Mime Type: unknown/exe
Path: C:\Users\<username>\AppData\Local\Microsoft\Performance\Monitor\temp\tmp9927.exe
Group: Malware file
Last Updated: November 17, 2021
eb5eb336636e3f6cacf6c8db6bf4ea00
File name: eb5eb336636e3f6cacf6c8db6bf4ea00Size: 604.41 KB (604410 bytes)
MD5: eb5eb336636e3f6cacf6c8db6bf4ea00
Detection count: 96
Group: Malware file
C:\Users\<username>\AppData\Local\Microsoft\Performance\Monitor\temp\tmp477B.exe
File name: tmp477B.exeSize: 237.4 KB (237400 bytes)
MD5: 1b21b27589ddc173ba795213e108a096
Detection count: 91
File type: Executable File
Mime Type: unknown/exe
Path: C:\Users\<username>\AppData\Local\Microsoft\Performance\Monitor\temp\tmp477B.exe
Group: Malware file
Last Updated: June 10, 2021
%APPDATA%\Microsoft\Crypto\sysras.exe
File name: sysras.exeSize: 220.72 KB (220726 bytes)
MD5: 881f86bf4bb4b9f0e993b2853a0a27cf
Detection count: 84
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%\Microsoft\Crypto
Group: Malware file
Last Updated: November 12, 2016
D:\?? ???????\Downloads\scoped_dir_5156_15540\Инструкция как скачать чит и ссылка на него.docx.exe
File name: Инструкция как скачать чит и ссылка на него.docx.exeSize: 6.56 MB (6561624 bytes)
MD5: 860bfffc08296bd13d43bef865b33f76
Detection count: 82
File type: Executable File
Mime Type: unknown/exe
Path: D:\?? ???????\Downloads\scoped_dir_5156_15540
Group: Malware file
Last Updated: July 2, 2016
K:\ADC\رزمايش.docx.exe
File name: رزمايش.docx.exeSize: 3.26 MB (3269675 bytes)
MD5: 64cc41e5aa1d5b34e6c49cbd9ffe9233
Detection count: 80
File type: Executable File
Mime Type: unknown/exe
Path: K:\ADC
Group: Malware file
Last Updated: July 2, 2016
%USERPROFILE%\??????? ????\Davlyatbegim\Testing Draft 2.docx.exe
File name: Testing Draft 2.docx.exeSize: 477.63 KB (477633 bytes)
MD5: 9406c8ea0f180383d3a8d5fedb105bb1
Detection count: 80
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\??????? ????\Davlyatbegim
Group: Malware file
Last Updated: July 2, 2016
%ALLUSERSPROFILE%\{5e5b8694-f299-3322-5e5b-b8694f291a53}\RPPTematikBerkarakterKelas1SDPengalamansms1.docx.exe
File name: RPPTematikBerkarakterKelas1SDPengalamansms1.docx.exeSize: 1.06 MB (1063936 bytes)
MD5: 14434f09c026e189161254a3230523e9
Detection count: 73
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\{5e5b8694-f299-3322-5e5b-b8694f291a53}
Group: Malware file
Last Updated: July 2, 2016
%USERPROFILE%\??? ?????????\Downloads\Министерство образования и науки Кыргызской Республики.docx.exe
File name: Министерство образования и науки Кыргызской Республики.docx.exeSize: 482.13 KB (482132 bytes)
MD5: a686e81153a11ea2817ecf58a9b0b25d
Detection count: 70
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\??? ?????????\Downloads
Group: Malware file
Last Updated: July 2, 2016
%ALLUSERSPROFILE%\{b36913b9-12df-03f6-b369-913b912d4ee4}\3.DAFTAR-LAMPIRAN--wahabkhoter.blogspot.com.docx.exe
File name: 3.DAFTAR-LAMPIRAN--wahabkhoter.blogspot.com.docx.exeSize: 465.4 KB (465408 bytes)
MD5: 85242fee40a9a0bc3ce6c20f52050643
Detection count: 61
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\{b36913b9-12df-03f6-b369-913b912d4ee4}
Group: Malware file
Last Updated: July 2, 2016
%ALLUSERSPROFILE%\{841eeb9e-7320-6fb8-841e-eeb9e732ae79}\PROGRAMPEMBELAJARANKELAS4.docx.exe
File name: PROGRAMPEMBELAJARANKELAS4.docx.exeSize: 846.84 KB (846848 bytes)
MD5: 7c87cdad5223b0ac9e1a5e2e5cc0d20f
Detection count: 41
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\{841eeb9e-7320-6fb8-841e-eeb9e732ae79}
Group: Malware file
Last Updated: July 2, 2016
7F9C454A2E016E533E181D53EBA113BC
File name: 7F9C454A2E016E533E181D53EBA113BCSize: 846.84 KB (846848 bytes)
MD5: 7f9c454a2e016e533e181d53eba113bc
Detection count: 33
Group: Malware file
Last Updated: February 15, 2020
%USERPROFILE%\??????? ????\???\ready\Министерство образования и науки Кыргызской Республики1.docx.exe
File name: Министерство образования и науки Кыргызской Республики1.docx.exeSize: 485.5 KB (485504 bytes)
MD5: 5bcb809524857f26a89ac67ffc80f6f5
Detection count: 31
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\??????? ????\???\ready
Group: Malware file
Last Updated: July 2, 2016
F:\Списывание.docx.exe
File name: Списывание.docx.exeSize: 296.05 KB (296059 bytes)
MD5: b870f4a3f292452971628fcb54d9067e
Detection count: 23
File type: Executable File
Mime Type: unknown/exe
Path: F:
Group: Malware file
Last Updated: July 2, 2016
%USERPROFILE%\??? ?????????\Downloads\Резюме.doc.exe
File name: Резюме.doc.exeSize: 493.56 KB (493568 bytes)
MD5: 12303bbfe7194fd4f0070cd4d1005209
Detection count: 19
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\??? ?????????\Downloads
Group: Malware file
Last Updated: July 2, 2016
КЫРГЫЗ РЕСПУБЛИКАСЫ сейчас КЫРГЫЗСКАЯ РЕСПУБЛИКА.docx.exe
File name: КЫРГЫЗ РЕСПУБЛИКАСЫ сейчас КЫРГЫЗСКАЯ РЕСПУБЛИКА.docx.exeSize: 545.45 KB (545454 bytes)
MD5: acf9873c86e35b9bee0db158befe8163
Detection count: 16
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: July 2, 2016
%USERPROFILE%\Desktop\Тесты по модулю Пищеварительная система для студентов 2-курса факультета лечебное дело.docx.exe
File name: Тесты по модулю Пищеварительная система для студентов 2-курса факультета лечебное дело.docx.exeSize: 3.99 MB (3998800 bytes)
MD5: 49115ff6fe4016169c24ff3783010321
Detection count: 14
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Desktop
Group: Malware file
Last Updated: July 2, 2016
%USERPROFILE%\Desktop\????? ?????\план части.docx.exe
File name: план части.docx.exeSize: 305.09 KB (305099 bytes)
MD5: bac4daf1ba563a5fdd01691441cedc9b
Detection count: 14
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Desktop\????? ?????
Group: Malware file
Last Updated: July 2, 2016
C:\$Recycle.Bin\S-1-5-21-1960731918-3399909957-3434517366-1000\$R803NKR.exe
File name: $R803NKR.exeSize: 9.97 MB (9972789 bytes)
MD5: b8ebbc2a6001ff318e49e0ec679c185f
Detection count: 9
File type: Executable File
Mime Type: unknown/exe
Path: C:\$Recycle.Bin\S-1-5-21-1960731918-3399909957-3434517366-1000\$R803NKR.exe
Group: Malware file
Last Updated: October 12, 2023
E:\?? ?????????\Выписка из Протокола.docx.exe
File name: Выписка из Протокола.docx.exeSize: 296.58 KB (296581 bytes)
MD5: 06dbb0786866ec652b12ddfcc204a735
Detection count: 4
File type: Executable File
Mime Type: unknown/exe
Path: E:\?? ?????????
Group: Malware file
Last Updated: July 2, 2016
More files
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.