BitCrypt Ransomware
Posted: April 11, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 48 |
| First Seen: | April 11, 2014 |
|---|---|
| OS(es) Affected: | Windows |
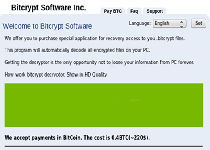 The BitCrypt Ransomware is a file encryptor Trojan that modifies files to prevent you from using them, with a focus on prominent file types like Microsoft documents and images. After blocking your access to different files, the BitCrypt Ransomware will use your desktop to communicate a ransom demand, requiring payment of roughly two hundred USD in BitCoins. Since the BitCrypt Ransomware's controlling creators have no reason to unlock any files encrypted by the BitCrypt Ransomware even after they've received payment, malware experts recommend the tandem use of remote file backups and anti-malware tools for hindering and removing the BitCrypt Ransomware inexpensively.
The BitCrypt Ransomware is a file encryptor Trojan that modifies files to prevent you from using them, with a focus on prominent file types like Microsoft documents and images. After blocking your access to different files, the BitCrypt Ransomware will use your desktop to communicate a ransom demand, requiring payment of roughly two hundred USD in BitCoins. Since the BitCrypt Ransomware's controlling creators have no reason to unlock any files encrypted by the BitCrypt Ransomware even after they've received payment, malware experts recommend the tandem use of remote file backups and anti-malware tools for hindering and removing the BitCrypt Ransomware inexpensively.
The Trojan that Kicks You While You're Down
Ransomware campaigns are nothing new to malware researchers, who have seen them target most nations throughout the globe, but peculiarly the United States and Europe. Currently being installed by a variant of the Fareit Trojan, the BitCrypt Ransomware has been identified in two, separate variants, with its second one including updates to make its attacks more difficult to remedy than previously. As a file encryptor, the BitCrypt Ransomware uses RS4-1024 encryption standards to scramble the data of diverse file types, making the affected files unusable without decryption. Other PC security companies have released free decryption tools for the oldest known version of the BitCrypt Ransomware, although these tools are not able to decrypt files affected by the latest version of the BitCrypt Ransomware.
Besides finding your files unable to be opened and appended with a 'bitcrypt2' file type suffix, a BitCrypt Ransomware attack also is recognizable by its changes to your wallpaper, which the BitCrypt Ransomware uses to display its ransom message. The BitCrypt Ransomware insists that you use the Tor anonymity browser – a legitimate utility whose features often are exploited by threat authors – to visit their website and make payment of 0.4 BitCoins to receive their own decryption tool.
However, the BitCrypt Ransomware may be plundering from the already-plundered, since the Trojan that installs the BitCrypt Ransomware, Fareit, also has been known to include functions for gathering the contents of BitCoin wallets automatically. The twice-attempted BitCoin theft could be a sign of third parties trying to wring money from the same victim several times. However, malware experts find it more likely that they used Fareit as a generic delivery vehicle for the BitCrypt Ransomware without bothering to modify the first Trojan's default behavior. Fareit is a more multiple-purpose Trojan than the BitCrypt Ransomware, and also may install other threats or collect protected information from your computer.
Crawling out of the File Crypt of the BitCrypt Ransomware's Attack
As a rule, malware researchers recommend finding alternatives to paying cybercrooks in ransomware-based situations. With respect to the BitCrypt Ransomware, the simplest defense is to keep all important files on a remote backup, which can be used to restore any encrypted files after you've removed the BitCrypt Ransomware. Old versions of the BitCrypt Ransomware also may have their file-modifying attacks resolved by free utilities, as previously noted.
Since a secondary PC threat installs the BitCrypt Ransomware, removing the BitCrypt Ransomware also requires removing Fareit. Any suspected BitCrypt Ransomware infection should be followed up by an overall anti-malware scan of your computer. Malware analysts also would counsel using Safe Mode or other means of blocking the BitCrypt Ransomware, to prevent any unintended problems with accessing all of your security software.
Unfortunately, legitimate services like BitCoin and Tor continue to be exploited by unscrupulous persons for personal gain, and problems like the BitCrypt Ransomware show no signs of slacking off in the future.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:f2dfa6a0bc275a78d76f7f6c123e4d34
File name: f2dfa6a0bc275a78d76f7f6c123e4d34Size: 32.25 KB (32256 bytes)
MD5: f2dfa6a0bc275a78d76f7f6c123e4d34
Detection count: 35
Group: Malware file
Bitcrypt.txt
File name: Bitcrypt.txtMime Type: unknown/txt
Group: Malware file
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.