Windows Antivirus Booster
Posted: March 1, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 18 |
| First Seen: | March 3, 2014 |
|---|---|
| Last Seen: | March 28, 2019 |
| OS(es) Affected: | Windows |
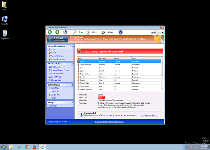 Windows Antivirus Booster is a variant of NameChanger, a fake anti-malware scanner that changes its names between versions while also providing fake security alerts, anti-virus scans and other fraudulent security 'features'. The primary lure in Windows Antivirus Booster's tactic is its attempt to trick you into registering its premium software for no benefits to your PC, but malware researchers also categorize Windows Antivirus Booster as a major security risk due to the potential for blocked security programs and related issues. Removing Windows Antivirus Booster should be done without purchasing Windows Antivirus Booster, and with the assistance of dependable, legitimate anti-malware utilities whenever available.
Windows Antivirus Booster is a variant of NameChanger, a fake anti-malware scanner that changes its names between versions while also providing fake security alerts, anti-virus scans and other fraudulent security 'features'. The primary lure in Windows Antivirus Booster's tactic is its attempt to trick you into registering its premium software for no benefits to your PC, but malware researchers also categorize Windows Antivirus Booster as a major security risk due to the potential for blocked security programs and related issues. Removing Windows Antivirus Booster should be done without purchasing Windows Antivirus Booster, and with the assistance of dependable, legitimate anti-malware utilities whenever available.
The Booster Shot for Your PC that's Full of Threats
Windows Antivirus Booster is part of the ongoing continuation of the name-swapping hoaxes of the FakeVimes, Tritax and FakePAV families of rogue anti-malware products. While Windows Antivirus Booster derives its appearance from previous iterations of these families and shows minimal new functions, Windows Antivirus Booster's name has been altered to make it difficult to identify as scamware, essentially identical to Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security. These rogue anti-malware programs may be installed through fake 'system scanners' implemented via corrupted JavaScript exploits, which are hosted on criminal websites.
After being installed by such an exploit, Windows Antivirus Booster continues its part in this hoax through the use of fake pop-up warnings that identify PC threats. While Windows Antivirus Booster uses warnings that reference real kinds of threatening software, Windows Antivirus Booster doesn't try to detect these threats, and, instead, will claim that any affected PC is suffering from these issues. Malware researchers also warn of a related problem: Windows Antivirus Booster may block other applications by terminating their processes automatically or making harmful Registry changes. A successful program block may cause Windows Antivirus Booster to load one of its fake warnings, to make it look as though the software was infected.
Turning Down the Offer of Antivirus Health that Hurts Your Computer
Windows Antivirus Booster may camouflage itself perfectly as an anti-virus product, but can neither find nor remove legitimate viruses of any kind. Currently, malware experts find it safe to use free codes to register Windows Antivirus Booster (an optional step that can streamline its removal), but strongly advise against purchasing Windows Antivirus Booster or giving the criminals affiliated with Windows Antivirus Booster any kind of confidential information. Whether you installed Windows Antivirus Booster intentionally or Windows Antivirus Booster was installed by force, Windows Antivirus Booster always should be considered threatening software, due for deletion as soon as you can access appropriate anti-malware products.
Deleting Windows Antivirus Booster also may be slowed down by its predilection for blocking other applications, including instant messengers, some types of Web browsers and even basic security programs like Task Manager. If you need to access a program blocked by Windows Antivirus Booster before Windows Antivirus Booster can be removed, boot your PC through Safe Mode (accessible by tapping F8 during a system restart until the relevant menu appears). Alternately, you can load a backup OS from a peripheral device or DVD.
However, malware researchers always finds it safest to act in a preventive fashion versus threats, and good browser protection hopefully will keep Windows Antivirus Booster from eyeing you as its next mark, in the first place.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:svc-wqfm.exe
File name: svc-wqfm.exeSize: 1.44 MB (1445376 bytes)
MD5: 23ac0fec3f5348022cf51ac029cc8085
Detection count: 49
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: March 3, 2014
%AppData%\data.sec
File name: %AppData%\data.secMime Type: unknown/sec
Group: Malware file
%AppData%\svc-[RANDOM CHARACTERS].exe
File name: %AppData%\svc-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AllUsersProfile%\Start Menu\Programs\Windows AntiVirus Booster.lnk
File name: %AllUsersProfile%\Start Menu\Programs\Windows AntiVirus Booster.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%UserProfile%\Desktop\Windows AntiVirus Booster.lnk
File name: %UserProfile%\Desktop\Windows AntiVirus Booster.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
File name without pathWindows AntiVirus Booster.lnkHKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "S_SC" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "ZSFT" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "MS-SEC" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = ".zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = 1HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = "%AppData%\svc-[RANDOM CHARACTERS].exe"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\bckd "ImagePath" = 22.sys HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableVirtualization" = 0HKEY..\..\..\..{Subkeys}HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exeHKEY_LOCAL_MACHINE\Software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exe
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.