Windows Antivirus Suite
Posted: February 21, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 35 |
| First Seen: | February 21, 2014 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
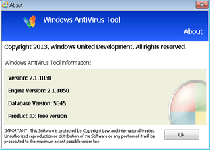
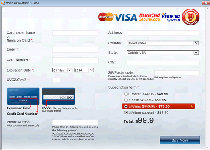
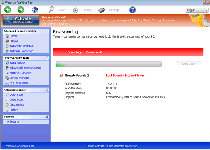 Windows AntiVirus Suite is a rogue anti-malware program that creates system alerts imitating the content of legitimate anti-malware suites but without the real protection or threat-detection accuracy provided by these products. Buying Windows AntiVirus Suite may not provide you with any actual defense from threats, but Windows AntiVirus Suite will transfer your financial information to criminals while Windows AntiVirus Suite continues impeding your PC's real security features. Proper removal of Windows AntiVirus Suite doesn't require its purchase or registration, but you should attempt to disable Windows AntiVirus Suite before using a real anti-malware program to uninstall Windows AntiVirus Suite safely.
Windows AntiVirus Suite is a rogue anti-malware program that creates system alerts imitating the content of legitimate anti-malware suites but without the real protection or threat-detection accuracy provided by these products. Buying Windows AntiVirus Suite may not provide you with any actual defense from threats, but Windows AntiVirus Suite will transfer your financial information to criminals while Windows AntiVirus Suite continues impeding your PC's real security features. Proper removal of Windows AntiVirus Suite doesn't require its purchase or registration, but you should attempt to disable Windows AntiVirus Suite before using a real anti-malware program to uninstall Windows AntiVirus Suite safely.
The Suite that Provides You with Problems When You're Lacking Them
Although its design template shows many traits familiar to the FakePAV and Tritax families, malware researchers currently classify Windows AntiVirus Suite as a member of the FakeVimes family. Like any crime family, these families require plausible deniability in the form of obfuscated identities, and Windows AntiVirus Suite is one of the latest variants to be wheeled out with a new name to confuse victims into thinking Windows AntiVirus Suite is a legitimate product. Some of the other PC threats most likely related to Windows AntiVirus Suite include Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.
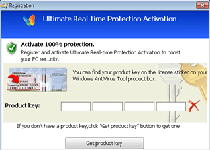
While Windows AntiVirus Suite claims to offer 'ultimate protection' in the form of a process manager, anti-malware scans, phishing defenses and other PC security features, Windows AntiVirus Suite's real functions are meant to inhibit real PC maintenance. Windows AntiVirus Suite persistently detects fake threats, including high-level ones that resemble the alerts of real anti-malware products, and may take additional steps to block other programs. Although Windows AntiVirus Suite will claim that its invasive functions are intended to protect your computer, malware researchers have confirmed that Windows AntiVirus Suite is simple scamware and has no benefits, either before or after purchase.
Signing out of the Windows AntiVirus Suite
As long as Windows AntiVirus Suite is installed, and even if you're determined to ignore any false flags or pop-ups from Windows AntiVirus Suite, Windows AntiVirus Suite poses a danger to your computer. Victims of attacks from the same families often experienced blocked access to social networking programs and security software, with the latter being a critical concern to malware experts. Since Windows AntiVirus Suite's deletion will require removing harmful Registry changes that affect other applications, you should avoid deleting Windows AntiVirus Suite manually, in normal circumstances. Anti-malware products that are kept updated should be able to remove Windows AntiVirus Suite after Windows AntiVirus Suite is been disabled by common security practices, such as rebooting with the Safe Mode option.
Windows AntiVirus Suite, and other, new versions of FakeVimes 'products' often are seen being distributed through hacked and unsafe sites. Exposure to these attacks may compromise your computer and, in many cases, may be identified by the display of a fake security or anti-malware alert. Anti-malware products with Web protection and browser security features often are helpful for disabling these attacks, which are responsible for the proliferation of a wide range of threats besides Windows AntiVirus Suite.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:svc-ocpe.exe
File name: svc-ocpe.exeSize: 1.27 MB (1276928 bytes)
MD5: a05efa46453d60f5c51bcb55b4544905
Detection count: 51
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: January 8, 2020
%AppData%\data.sec
File name: %AppData%\data.secMime Type: unknown/sec
Group: Malware file
%AppData%\svc-[RANDOM CHARACTERS].exe
File name: %AppData%\svc-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AllUsersProfile%\Start Menu\Programs\Windows Antivirus Suite.lnk
File name: %AllUsersProfile%\Start Menu\Programs\Windows Antivirus Suite.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%UserProfile%\Desktop\Windows Antivirus Suite.lnk
File name: %UserProfile%\Desktop\Windows Antivirus Suite.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
File name without pathWindows Antivirus Suite.lnkHKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "S_SC" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = ".zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = 1HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = "%AppData%\svc-[RANDOM CHARACTERS].exe"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\bckd "ImagePath" = 22.sys HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableVirtualization" = 0HKEY..\..\..\..{Subkeys}HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exeHKEY_LOCAL_MACHINE\Software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exe
Additional Information
| # | Message |
|---|---|
| 1 | Error Attempt to run a potentially dangerous script detected. Full system scan is highly recommended. |
| 2 | Error There's a suspicious software running on your PC. For more details, run a system file check. |
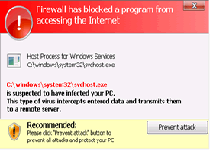
| 3 | Firewall has blocked a program from accessing the Internet Internet Explorer C:\Windows\system32\iexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits themto a remote server. |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.