Windows Premium Guard
Posted: April 26, 2012
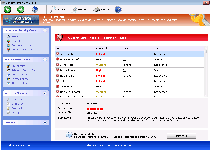
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 5 |
| First Seen: | April 26, 2012 |
|---|---|
| OS(es) Affected: | Windows |
 Windows Premium Guard is promoted and sold as an anti-virus product, but SpywareRemove.com malware research team has confirmed that Windows Premium Guard's true functions are those of a rogue anti-virus program, including inaccurate pop-up warnings, system scans with fraudulent results and various types of security-hindering behavior. While Windows Premium Guard will repeatedly encourage you to spend money on its registration key, purchasing Windows Premium Guard will only place your money and financial information in criminal possession, and you should always ignore Windows Premium Guard's prompts in favor of removing Windows Premium Guard with a legitimate anti-malware application. Because Windows Premium Guard may block your real security programs while Windows Premium Guard is open, you may also be required to boot your operating system in a way that bypasses Windows Premium Guard's startup routine before you can delete Windows Premium Guard – for example, by using Safe Mode or other baseline security features to assist your anti-malware software.
Windows Premium Guard is promoted and sold as an anti-virus product, but SpywareRemove.com malware research team has confirmed that Windows Premium Guard's true functions are those of a rogue anti-virus program, including inaccurate pop-up warnings, system scans with fraudulent results and various types of security-hindering behavior. While Windows Premium Guard will repeatedly encourage you to spend money on its registration key, purchasing Windows Premium Guard will only place your money and financial information in criminal possession, and you should always ignore Windows Premium Guard's prompts in favor of removing Windows Premium Guard with a legitimate anti-malware application. Because Windows Premium Guard may block your real security programs while Windows Premium Guard is open, you may also be required to boot your operating system in a way that bypasses Windows Premium Guard's startup routine before you can delete Windows Premium Guard – for example, by using Safe Mode or other baseline security features to assist your anti-malware software.
Windows Premium Guard: Closer to a Virtual Thief Than a Protector
Windows Premium Guard belongs to the same group of scamware (identified as FakeVimes by Microsoft) as dozens of other rogue anti-virus scanners, including both recently-emerged PC threats and older ones like Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. SpywareRemove.com malware researchers stress that, despite their different brand names, each of these fake AV products uses similar attacks against your PC, particularly including fake pop-up alerts and system scans, and all of them should be considered just as hostile as Windows Premium Guard itself.
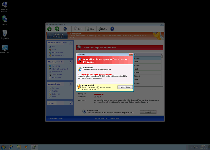
Pop-ups and other forms of security information from Windows Premium Guard should always be discarded as fraudulent and even potentially destructive to your PC if their advice is followed. SpywareRemove.com malware experts note that these fake alerts can include warnings about non-existent viruses, fake program activity warnings, threats about attacks that aren't occurring or various forms of 'software at risk' messages that encourage you to purchase Windows Premium Guard. Ultimately, despite the strong recommendations of these pop-ups, there's no reason to buy Windows Premium Guard, although you may wish to activate its registration process for free with the code '0W000-000B0-00T00-E0020' (which can reduce some of Windows Premium Guard's attacks against your PC).
Why Taking Out Windows Premium Guard's Fake Guardsmanship Should Be a High Priority
Unlike real anti-virus software, Windows Premium Guard will also launch itself with Windows and eschews giving you any way to disable this startup routine by normal methods. This can be problematic when attempting to remove Windows Premium Guard, since SpywareRemove.com malware researchers have found that scamware from Windows Premium Guard's family can also create security issues such as:
- Blocking security and anti-malware programs, including Windows tools like Task Manager.
- Redirecting your web browser to hostile websites when you attempt to use an online search engine.
- Disabling warning messages for file downloads with invalid signature identification (a method of distinguishing between legitimate programs and malicious ones).
- Disabling the Windows UAC, which prevents unauthorized changes to your PC.
Because these conditions work to make your computer much more vulnerable to other PC threats than it would be under ordinary circumstances, SpywareRemove.com malware research team suggests Windows Premium Guard's immediate deletion with anti-malware software once you notice any symptoms of a Windows Premium Guard infection. To disable Windows Premium Guard and access the appropriate software to expedite its removal, Safe Mode, a remote hard drive-based boot or booting into a second OS (especially a non-Windows OS, as Windows Premium Guard is, like all FakeVimes-based scamware, Windows-specific) are all useful.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-xfac.exe
File name: Protector-xfac.exeSize: 1.86 MB (1865728 bytes)
MD5: d37032237c1ab112dd11583fe2a8dc0a
Detection count: 68
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: April 26, 2012
%APPDATA%\Protector-mnlu.exe
File name: Protector-mnlu.exeSize: 1.85 MB (1858048 bytes)
MD5: ff3cb8c27cb3c89247fa0ef55f661dec
Detection count: 39
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: April 26, 2012
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\Protector-<RANDOM 4 CHARACTERS>.exe
File name: %AppData%\Protector-<RANDOM 4 CHARACTERS>.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Protector-<RANDOM 3 CHARACTERS>.exe
File name: %AppData%\Protector-<RANDOM 3 CHARACTERS>.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%Desktop%\Windows Premium Guard.lnk
File name: %Desktop%\Windows Premium Guard.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%CommonStartMenu%\Programs\Windows Premium Guard.lnk
File name: %CommonStartMenu%\Programs\Windows Premium Guard.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-4-25_4"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "uqcphfxlsq"HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\oaui.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wininetd.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashSimp2.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rcsync.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fp-win_trial.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\monitor.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\system32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bargains.exeHKEY_CURRENT_USER\Software\ASProtect
Additional Information
| # | Message |
|---|---|
| 1 | Error
Attempt to modify Registry key entries detected. Registry entry analysis recommended. |
| 2 | Error Attempt to modify Registry key entries detected. Registry entry analysis recommended. |
| 3 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 4 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
| 5 | Warning
Firewall has blocked a program from accessing the Internet C:\program files\internet explorer\iexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
| 6 | Warning Firewall has blocked a program from accessing the Internet C:program filesinternet exploreriexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
| 7 | Warning! Identity theft attempt Detected |
| 8 | Warning! Spambot detected!
Attention! A spambot sending viruses from your e-mail has been detected on your PC. |
| 9 | Warning! Spambot detected! Attention! A spambot sending viruses from your e-mail has been detected on your PC. |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.