Windows Safety Module
Posted: May 1, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 16 |
| First Seen: | May 1, 2012 |
|---|---|
| OS(es) Affected: | Windows |
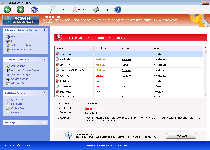 Windows Safety Module may borrow its visuals from Microsoft security software, but as a rogue anti-virus program, Windows Safety Module doesn't have any of the security-related functions to back up its looks. SpywareRemove.com malware researchers have readily identified Windows Safety Module as a new variant of FakeVimes, and as such, Windows Safety Module is capable of producing fake system alerts, inaccurate system scans and other forms of fraudulent security information as part of its scam to steal money and financial information. Because Windows Safety Module may also block Windows security applications and cause other undesirable effects, such as browser redirect attacks, deleting Windows Safety Module with a legitimate anti-malware application should always be high on your to-do list if you haven't just managed to avoid a Windows Safety Module infection in the first place.
Windows Safety Module may borrow its visuals from Microsoft security software, but as a rogue anti-virus program, Windows Safety Module doesn't have any of the security-related functions to back up its looks. SpywareRemove.com malware researchers have readily identified Windows Safety Module as a new variant of FakeVimes, and as such, Windows Safety Module is capable of producing fake system alerts, inaccurate system scans and other forms of fraudulent security information as part of its scam to steal money and financial information. Because Windows Safety Module may also block Windows security applications and cause other undesirable effects, such as browser redirect attacks, deleting Windows Safety Module with a legitimate anti-malware application should always be high on your to-do list if you haven't just managed to avoid a Windows Safety Module infection in the first place.
Windows Safety Module: A Remarkably Risky Form of 'Safety' Software
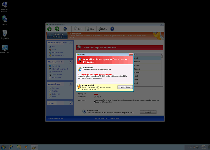
Windows Safety Module can be identified both visually and through its attacks as a clone of previous examples of scamware from Win32/FakeVimes such as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. In spite of its anti-virus software looks, Windows Safety Module's pop-up alerts, system scans and other forms of system analysis always contain inaccurate information about your PC – usually with reference to nonexistent infections or ongoing attacks (such as unauthorized network activity). SpywareRemove.com malware experts caution anything other than ignoring Windows Safety Module's warnings, which can cause you to damage innocent files or programs if you pay heed to their recommendations.
As the final note to its symphony of fraud, Windows Safety Module will repeatedly encourage you to spend money on a purchasable registration key to solve any and all problems your PC might be experiencing (which are, in reality, likely to originate from Windows Safety Module or related PC threats). SpywareRemove.com malware research team strongly discourages this for the safety of both your funds and any linked financial data, but registering Windows Safety Module with the free code '0W000-000B0-00T00-E0020' may prove useful before attempting to delete Windows Safety Module for good.
Acquiring the Real Security That Windows Safety Module Doesn't Want You to Have
Windows Safety Module's presence is also likely to coincide with various security issues, most noticeably including blocked access to security and anti-malware programs. Starting Windows without Windows Safety Module launching – for instance, by using a Safe Mode boot or booting from a removable drive – will allow you to circumvent this blockade and remove Windows Safety Module with a suitable anti-malware application. In the meantime, SpywareRemove.com malware research team also warns that victims of Windows Safety Module attacks should anticipate:
- Altered Windows settings that allow you to download unsafe files (such as files with nonvalid signature identification) without corresponding warnings from Windows.
- Browser redirects to harmful sites, particularly after you attempt to use a search engine.
- Unauthorized network activity that bypasses the Windows Firewall to report Windows Safety Module's installation on your PC.
- Disabled Windows security features such as the User Access Control.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [RANDOM CHARACTERS]HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\InspectorHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXEHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe
Additional Information
| # | Message |
|---|---|
| 1 | Error Attempt to run a potentially dangerous script detected. Full system scan is a highly recommended. |
| 2 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan |
| 3 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |


Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.