Windows Security Renewal
Posted: July 19, 2012
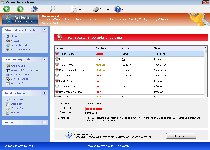
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 14 |
| First Seen: | July 19, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
 PC users who're as familiar with the FakeVimes family of rogue anti-malware programs as SpywareRemove.com malware researchers are will be able to identify Windows Security Renewal immediately as another example of said scamware. With not much to differentiate Windows Security Renewal from similar variants of fake anti-malware scanners, Windows Security Renewal is guilty of using fake security pop-ups and simulated scans to make its security services seem worth your money, along with attempts to block your authentic security programs so they can't debunk Windows Security Renewal's claims. While keeping your money from the hands of the criminals that promote Windows Security Renewal is a foremost concern, you should also strongly consider deleting Windows Security Renewal with real anti-malware software in short order since Windows Security Renewal will place your PC in a state of reduced security.
PC users who're as familiar with the FakeVimes family of rogue anti-malware programs as SpywareRemove.com malware researchers are will be able to identify Windows Security Renewal immediately as another example of said scamware. With not much to differentiate Windows Security Renewal from similar variants of fake anti-malware scanners, Windows Security Renewal is guilty of using fake security pop-ups and simulated scans to make its security services seem worth your money, along with attempts to block your authentic security programs so they can't debunk Windows Security Renewal's claims. While keeping your money from the hands of the criminals that promote Windows Security Renewal is a foremost concern, you should also strongly consider deleting Windows Security Renewal with real anti-malware software in short order since Windows Security Renewal will place your PC in a state of reduced security.
How Windows Security Renewal Withers Your Safety Under the Pretense of Boosting It
Windows Security Renewal, like any other adherent to the FakeVimes philosophy of fake PC security, completely lacks any actual functions that would allow Windows Security Renewal to detect, block or delete any form of PC threat. Instead of providing the anti-malware functions that Windows Security Renewal claims to have, Windows Security Renewal will launch automatic and fraudulent pop-ups and fake scans as soon as Windows launches. Since Windows Security Renewal will resist removal or even termination by usual means and will launch with Windows due to Registry-based system changes, SpywareRemove.com malware experts emphasize that it's necessary to disable and delete Windows Security Renewal with the same anti-malware strategies and software that you'd use against a virus or Trojan.
However, fake security features that try to fool you into buying Windows Security Renewal are only half of Windows Security Renewal's story. As seen here, the rest of Windows Security Renewal's unwarranted features are somewhat more malicious than inaccurate pop-up warnings:
- Browser redirects may alter your search results, alter your default search engine, expose you to malicious online content or take you to sites that generate advertisement-based money for the criminals behind Windows Security Renewal.
- Blocked applications will prevent you from using normal security tools to delete Windows Security Renewal and related PC threats until you disable Windows Security Renewal (via Safe Mode or by booting from a removable media-based device). In some cases, programs that are blocked by Windows Security Renewal may also have their Registry entries removed, which can necessitate that you repair your Registry or reinstall these programs. Some oft-blocked applications include:
– Windows UAC
– Windows Live OneCare
–Windows Task Manager
– Anti-malware/anti-virus scanners
–Windows Firewall
Saving Your PC from the Cycle of Windows Security Renewal's Treacherous Intel
Windows Security Renewal should always be treated as equivalent to a Trojan or similar PC threat, and SpywareRemove.com malware researchers recommend disabling Windows Security Renewal before you scan your PC to remove Windows Security Renewal and associated PC threats (such as Trojan downloaders like Zlob that often install Windows Security Renewal and other FakeVimes-based scamware). Fake anti-malware scanners like Windows Security Renewal are often inadvertently acquired from fraudulent media updates for movie players and codec packages, and it's always recommended that you acquire any updates from their original and reputable sources.
In all meaningful respects, Windows Security Renewal can be considered identical to other rogue anti-malware programs that are classified as FakeVimes members. These relatives of Windows Security Renewal include (but aren't limited to) Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-weeb.exe
File name: Protector-weeb.exeSize: 2.22 MB (2225152 bytes)
MD5: 44ee30424f0bfce281bb5d4c78695831
Detection count: 17
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
%AppData%/Protector-[rnd].exe
File name: %AppData%/Protector-[rnd].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunInspector %AppData%\Protector-[rnd].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd]HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXEHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.