Windows Virtual Security
Posted: August 9, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 9 |
| First Seen: | August 9, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
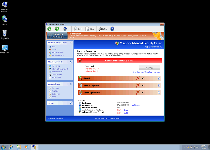
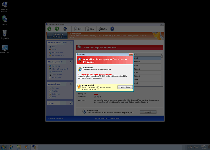
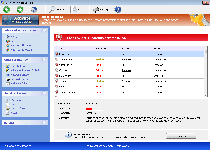 Windows Virtual Security is a fake anti-malware product that borrows the details of its interface from a combination of Windows Security Center and scamware from the same family as itself. Although Windows Virtual Security looks like a Windows-oriented security product, SpywareRemove.com malware experts have verified that Windows Virtual Security doesn't have any ability to find or remove any type of PC threat, including the Trojans, spyware and worms that Windows Virtual Security will prominently alert you to being on your computer. While there's no need to buy Windows Virtual Security or pay any heed to its fake security warnings, it is recommended that you delete Windows Virtual Security with a legitimate anti-malware program, since other attacks by Windows Virtual Security can cause issues for your operating system and web browser's security.
Windows Virtual Security is a fake anti-malware product that borrows the details of its interface from a combination of Windows Security Center and scamware from the same family as itself. Although Windows Virtual Security looks like a Windows-oriented security product, SpywareRemove.com malware experts have verified that Windows Virtual Security doesn't have any ability to find or remove any type of PC threat, including the Trojans, spyware and worms that Windows Virtual Security will prominently alert you to being on your computer. While there's no need to buy Windows Virtual Security or pay any heed to its fake security warnings, it is recommended that you delete Windows Virtual Security with a legitimate anti-malware program, since other attacks by Windows Virtual Security can cause issues for your operating system and web browser's security.
Why Windows Virtual Security's 'Virtual' More Closely Resembles 'Imaginary'
Windows Virtual Security is a direct clone of other members of the FakeVimesfamily of fake anti-malware products, with similar variants encompassing such titles as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. Most infections by Windows Virtual Security and related PC threats are acquired through fake codec downloads and other forms of fraudulent software updates, although SpywareRemove.com malware experts note that other means (such as drive-by-download exploits) can also be used.
Windows Virtual Security is neither capable of finding nor removing hostile software from your PC. However, Windows Virtual Security's attacks include a heavy variety of fake pop-up alerts to convince you otherwise, by announcing the presence of nonexistent types of spyware and attacks against your computer (including its Registry and other Windows components). To add believability to these claims, Windows Virtual Security may even generate randomly-named junk files that contain no code while looking like the byproduct of poorly-coded PC threats. In spite of this bad marketing ploy, SpywareRemove.com malware researchers can't recommend purchasing Windows Virtual Security, which is never a legitimate security product even in its registered form.
Where Windows Virtual Security's Antisecurity Stopgaps Come In
Besides being a bad security product in and of itself, Windows Virtual Security may also hamper security with respect to your web browser and Windows OS. Attacks that SpywareRemove.com malware researchers have associated with recent versions of Windows Virtual Security's family of rogue anti-malware programs include such issues as:
- Browser hijacks that block search engine sites, redirect you to unusual websites, alter your browser's error pages or prevent you from accessing PC security domains.
- Blocked security programs, including firewall utilities, Windows products like Task Manager and some brands of anti-malware scanners.
- Registry changes that reduce your web-browsing security by disabling alerts against potentially-malicious file downloads and website content.
While spending money on Windows Virtual Security is never safe for your finances or PC, SpywareRemove.com malware analysts can recommend using free codes to fake Windows Virtual Security's registration prior to deleting Windows Virtual Security with anti-malware software.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-exsh.exe
File name: Protector-exsh.exeSize: 1.96 MB (1969664 bytes)
MD5: cf08b9819944034d24297131dce44d07
Detection count: 35
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
%AppData% Protector-[rnd].exe
File name: %AppData% Protector-[rnd].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[rnd].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd]HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exeDebugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXEHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe
Additional Information
| # | Message |
|---|---|
| 1 | "Error Key-logger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan" |
| 2 | "Microsoft Security Essentials detected potential threats that might compromise your privacy or damage your computer. You need to clean your computer immediately to prevent the system crash" |
| 3 | "Trojan-PSW.Win32.launch Hack Tool:Win32/Welevate.A Adware.Win32.Fraud" |
| 4 | "Warning! Identity theft attempt Detected Hidden connection IP: 58.82.12.124 Target: Your passwords for sites" |
| 5 | "Warning! Virus Detected Threat detected: FTP Server Infected file: C:\Windows\System32\dllcache\wmploc.dll" |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.