Updated Tinba Banking Botnet Aggressively Attacks Russian Banking Institutions
 An ongoing campaign has been detected to target several Russian banking institutions in the recent days from what appears to be an aggressive botnet attack. The cybercriminals behind the efforts of attacking Russian banks and various payment service providers were found by Dell SecureWorks to be using a sophisticated botnet called Tinba, which is a banking Trojan similar to the famous Zeus threat we have covered to no end.
An ongoing campaign has been detected to target several Russian banking institutions in the recent days from what appears to be an aggressive botnet attack. The cybercriminals behind the efforts of attacking Russian banks and various payment service providers were found by Dell SecureWorks to be using a sophisticated botnet called Tinba, which is a banking Trojan similar to the famous Zeus threat we have covered to no end.
The Tinba 2.0 banking Trojan horse, technically a botnet, masquerades in its second iteration as a threat that has previously focused its efforts to attack entities located in European areas, Japan and North America. Since its first discovery in 2014, Tinba has evolved into an updated threat that is sold on the black market as a botnet kit.
Dell SecureWorks map of Tinba infections from October 2015
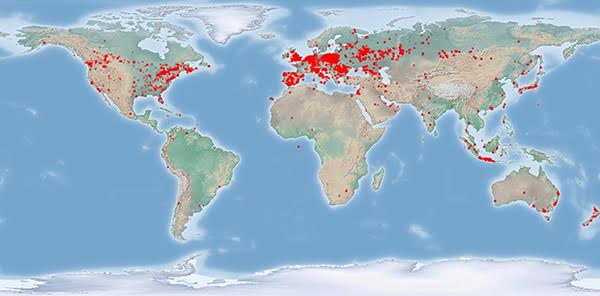
Fundamentally, Tinba can be purchased by anyone who is inclined to set up their own command and control (C&C) servers and configure various security and authentication methods to evade detection while it performs the action of seeking out banking login information.
The hackers behind Tinba have recently gone after Russian banks and payment service providers. While such a target is rather uncommon for banking Trojans and botnets, the reasoning behind this strategy makes sense in the light of cybercrooks wanting to avoid attention and alerting law enforcement.
As it turns out, Russian targets are not mostly areas that law enforcement does not monitor as heavily as institutions located in North America or other European countries. In a large percentage of cases, it is Russia that is waging the attacks instead of receiving them.
The Dell SecureWorks researchers found where most of the victims of Tinba's wraith were initially infected through spam email messages and exploits like the Angler, Neutrino and Nuclear kits. Such exploit kits have been used in the past with great success to aid in the efforts of other malware to collect financial operation data and send it to a C&C server so cybercriminals may use it for fraudulent transactions.
As the unethical practices of hackers grow to unprecedented heights, new and sophisticated malware like the Tinba threat will be at the forefront of attacks. It just so happens that hackers are still perpetuating attacks on banking institutions through the use of info-stealing botnets and Trojan horses like Tinba, which you could technically claim to be a successor to the nearly decade-old Zeus botnet threat.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.