Behavior-Based Classification of Malware May Be the Key to Diminishing Future Attacks
It seems every year there is a virtual battle among malware threats and computer worms to win-over its predecessor with new sophisticated attack methods and a means of spreading faster than ever before. With this virtual fight, come many unfortunate victims left to wither and die until a solution is created to either stop the attack or diminish its future effectiveness.
One security firm thinks they have the answer to help abolish future malware attacks all by mapping or recording the world's malware. Josh Saxe from Invincea labs Fairfax, Virginia says, "Our vision is to have a database of the world's malware, which people can use to share insights." The scheme is based on a method to classify malware along with the programs cybercrooks utilize to send spam, steal passwords and other malicious activities.
Many security firms and experts already have their own method for classifying malware threats. We even have our own extensive database of malware. However, with the astonishing rate of which malware is produced, automated systems to pick up and classify new threats mostly analyze the malware code instead of behaviors. Behavior of malware is what will allow Saxe and others to find a key to limiting future attacks.
Breaking down malware behaviors of many strains allowed Saxe and colleagues to break the communication data into blocks. These contained certain sequences of calls throughout different samples of malware thus being able to group them into Saxe's "malware families". From there, a catalog of the newly classified malware can be created giving others additional data on analysis of emerging strains and trends.
Not only will analysts be able to group malware families, but they will be able to determine the origin malware, such as specific websites. When they visualize these new groups the determination of malware authors of new strains can be made. Of course within each instance of deciphering the data, classification could take a turn in a different direction than a firm who bases their information off of a different schematic.
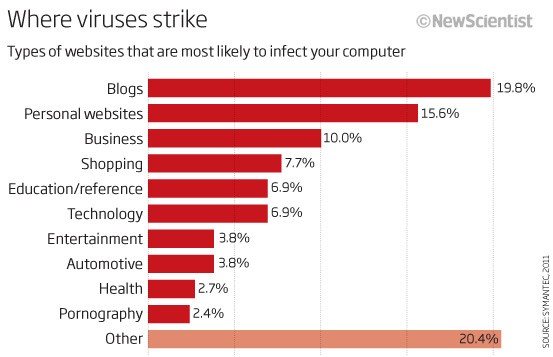
As an example of the specific websites types that infect your system, the 'Where Viruses Strike' chart below lists a percentage captured in 2011 by NewScientist.
Run by the US Defense Advanced Research Projects Agency, the Invincea project is one of several funded under the Cyber Genome Program. Many of the results of the project have not yet been made public. Just to show the massive scale of this project, they will utilize computer networks run by the Department of Defense.
The more information at our disposal in the right hands, the better off we could be when combating malware in the near future due to projects like Invincea's. Do you foresee a day when the 'good guys' ever getting ahead of the malware creators and hackers?
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.