Report: Bing Surpasses Google in Having Malware-Laced and Spam Search Results
It has been estimated in a recent Sophos Security study that nearly two-thirds of search results on Bing are found to have links that spread spam or malware. When compared with the search engine giant Google, which only accounts for 30 percent of links that spread spam or malware, Bing clearly leads the search engine pack for malware-laced search results.
What has become an epidemic over the course of the past few years, is the efforts of hackers to poison search engine results. This crafty game played well by cybercrooks, is an effort of combining sophisticated SEO (Search Engine Optimization) techniques with either hacked sites or ones created specifically for spreading malware. Popular new stories are always prime real estate on search engine results for search engine poisoning.
In Sophos' latest efforts to test their own 'web appliance' for poisoned searches used to drive traffic to sites designed to extort money from unsuspecting computer users, they are able to track down search engine redirects. Contrary to Sophos' findings of Bing being responsible for nearly two-thirds of search results having links spreading malware or spam, Microsoft exclaimed "signals that have been previously spammed now have countermeasures to prevent abuse. Bing has also developed several ranking signals to help weed out spam results and better understand the intent of the searcher. We are always looking to improve the Bing user experience for customers, and remain dedicated to providing a trusted and reliable search experience."
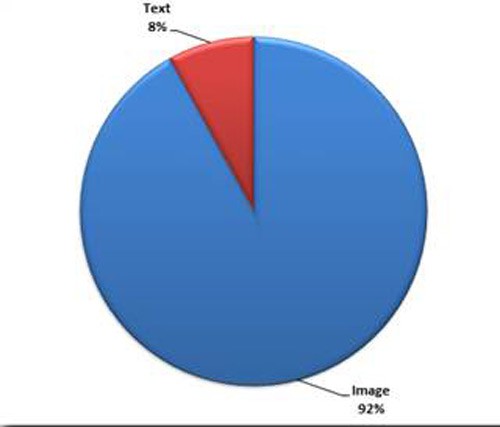
From data collected by Sophos, they were able to determine that attackers were most successful by poisoning image search results. The chart below, Figure 1, is compiled from Sophos' data clearly showing how text results are filtered more so than image results. The percentage of search results poisoning is happening more so among image searches, about 92% in total, over a small 8% of text results.
Figure 1. Sophos Security percent of image vs text poisoned search results
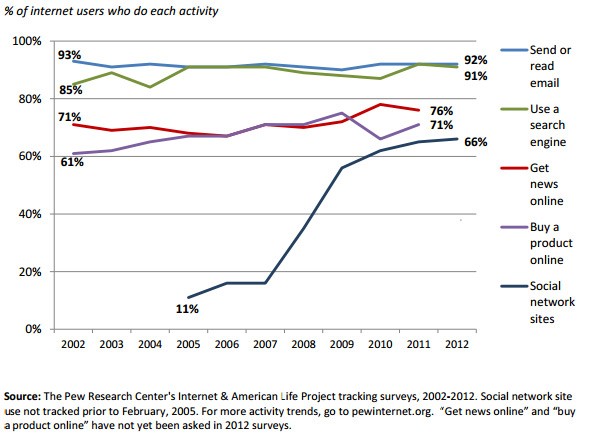
The Pew Research Center's Internet & American Life Project estimates that 91% of Internet users utilize a search engine, which is only surpassed by 92% rate of Internet users using it for sending or reading email, as demonstrated in the Internet user's activity chart below (Figure 2). It would only make sense for online attackers and cybercrooks to focus their efforts on poisoning search engine results whenever possible. Even though Bing is not as widely used as Google (second place to Google), there is enough 'virtual' business for hackers where their malicious actions are not in vein. You may be asking yourself, how can you protect yourself and limit the amount of poisoned search engine results that come your way? Below we have 5 simple tips that you may use to reduce your chances of loading a malicious or spammy site from poisoned search results.
Figure 2. Pew Research % of internet users activity report chart
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.