Report: Cyber Gangs Prefer Exploit-Style Malware Attacks Over Traditional Phishing Methods
Crimeware-based attacks are something that has been on the back burner for crybercrooks until they saw the light of day when they could utilize creative social engineering techniques to ramp up unique phishing attacks.
Crimeware attacks are mostly based on traditional phishing exploits where unique phishing sites are launched in an effort to lure susceptible PC users thus extracting personal information or spreading malware. Phishing is an aged technique that attempts to acquire data such as usernames, passwords and financial information from a site purposely created to mimic a legitimate entity. In other cases. email spoofing is a method of phishing where email messages are used to lure unsuspecting computer users where they think the email came from their bank or something attempting to confirm login credentials.
Professional phishers have moved to the open water where they can conduct exploit-style malware attacks instead of the traditional mass phishing campaigns. These non-traditional exploits, outlined in the APWG (Anti-Phishing Working Group) report of the most targeted industry sectors in the 3rd quarter of 2012, received 30,955 unique phishing site reports in July 2012. This number is just 24% lower than the all-time high of 40,621 reports recorded in August of 2009.
The most targeted industry sectors, as demonstrated in the pie chart in Figure 1 below, shows how financial and payment services made up the majority of crimeware-based attacks comprised of 34.4% and 32.1% respectfully.
Figure 1. Most Targeted Industry Sectors 3rd Quarter '12 Chart - APWG Report
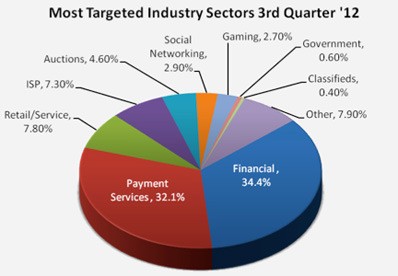
With cybergangs making their move to exploit-style malware attacks, it makes it more difficult to detect if we only look for traditional phishing indicators. The new type of exploit-style attacks utilize drive-by downloads that infect users directly with malware. This method basically bypasses the traditional sense of collecting data through a common phishing site. These old social engineering methods of phishing have gone the way of the dinosaurs as cybergangs dance to a new exploit-style tune.
Phishing on a grand scale have also taken a turn to continue to targeting '.com' top-level-domains over all other types, as demonstrated in the Phishing by TLD Q3 2012 pie chart in Figure 2 below. Not only are cyber gangs becoming bold with new phishing techniques, but they have gone in for the ultimate kill by targeting the most popularized top-level-domain type, the .com.
Figure 2. Phishing by TLD Q3 2012 Chart - APWG Report
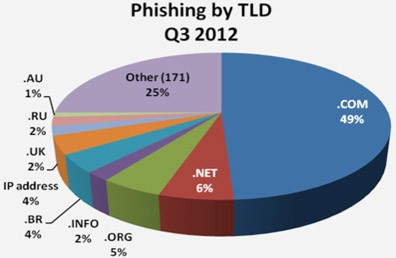
Other items to note within the Q3 2012 APWG report are the facts of China being the top ranking country for malware infections and financial services continuing to be the most-targeted industry. It looks as if the new exploit-style attacks will put the same targets of old-outgoing Phishing methods in the cross-hairs of cyber gangs who have adapted to works on a larger scale.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.