Malware Attacking Java CVE-2012-1723 Flaw Increases to Unprecedented Volumes
Hackers have taken to their roots to do what they do best in a recent attack on a Java CVE-2012-1723 flaw. A vulnerability within the Java CVE-2012-1723 was patched by Oracle almost two months ago to put an end to a remote pre-authentication flaw in the Java Runtime environment. Not giving the patch enough time to reach vulnerable computers, hackers have made it their business to get a jump on exploiting this very flaw potentially allowing them to execute arbitrary code on the target system.
Java exploits are only one of many ways attackers could slip malicious code onto a vulnerable computer in an effort to execute malicious actions. Usually the choice to attack discovered flaws in Java is because they are able to obfuscate, or virtually hide their methods to loading malicious code.
The particular attacks on the Java CVE-2012-1723 flaw are recognized by security researchers as a way of loading a particular static field with a ClassLoader or Object type with custom data, to ultimately hide from detection. In other words, methods used to attack the Java CVE-2012-1723 vulnerability are growing at alarming rates because the initial attack shows no indication of exploitation.
July 10th of this year marked a date that analysts noticed a sharp rise in the number of Java CVE-20-12-1723 flaw attacks. Such an indicator could mean either the patch is not effective, or hackers have found a way to meticulously attack the vulnerability under the radar. By the reports coming out from the Microsoft Malware Protection Center, the latter is more likely relevant in this specific case.
The current Java CVE-2012-1723 flaw exploration volume increase goes along with analysis on Java exploits in general. The chart below shows a similar spike in Java exploitation attempts back in 2010 around the same time of year (July). Such an increase can be compared to what is happening currently with the Java CVE-2012-1723 flaw.
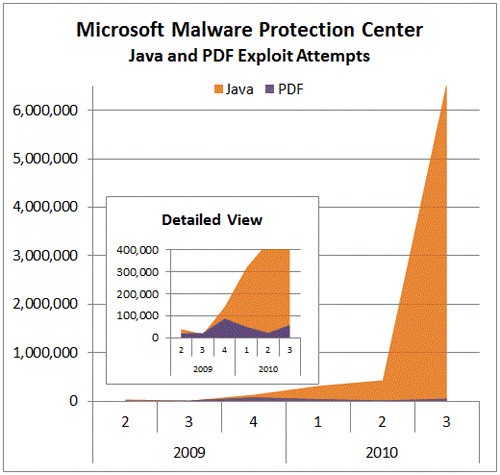
Java and PDF exploitation attempts in 2010 - source: Microsoft Malware Protection Center
One could say this emerging attack has reached unprecedented volumes because of hackers' ability to perform the attacks under the radar. A specific oddity with the vulnerability, discovered by Jeong Wook Oh of the Microsoft Malware Protection Center, is the attackers really do not have the ability to hide what they are doing with their exploits. The attackers would essentially be required to take an extra step in building a Java class with specific attributes. In such a case, analysts would be able to tell what is going on if they know what to look for.
What it all comes down to attacking the Java CVE-2012-1723 in abundant numbers, the attackers taking extra steps to obfuscate the core exploit has been successful. The attackers would be required to create a class with specific features, such as a static field member with ClassLoader type or Object type methods. Normally, Java would not allow attacks without having the code stand out to experts. Instead, hackers need to take the long route for their attack, which they have done in the case of the Java CVE-2012-1723 for the number of attacks to have sparked since July 10, 2012.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.