Windows System Tasks
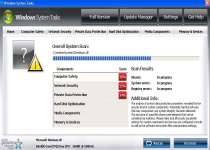 Windows System Tasks is a rogue security program that imitates the mere appearance of protecting your PC from infections and other problems. In the process of doing this, Windows System Tasks will create fake infection alerts and other false system information to lure you into purchasing a product activation key. However, Windows System Tasks lacks any true threat-detection or removal features, and will even harm your PC through browser hijacks and application-blocking while Windows System Tasks is active. Removing Windows System Tasks should be handled by appropriate anti-malware application due to the advanced nature of the Windows System Tasks threat.
Windows System Tasks is a rogue security program that imitates the mere appearance of protecting your PC from infections and other problems. In the process of doing this, Windows System Tasks will create fake infection alerts and other false system information to lure you into purchasing a product activation key. However, Windows System Tasks lacks any true threat-detection or removal features, and will even harm your PC through browser hijacks and application-blocking while Windows System Tasks is active. Removing Windows System Tasks should be handled by appropriate anti-malware application due to the advanced nature of the Windows System Tasks threat.
The Vehicle That Carries Windows System Tasks to Your Door
You might download Windows System Tasks without realizing Windows System Tasks's true malicious nature, but most Windows System Tasks infections are caused by Fake Microsoft Security Essentials Alert. This Trojan subtype is known for delivering many different types of rogue security programs, including Windows System Tasks, Windows Optimal Settings, Windows Protection Servant, Windows Repairing System and Windows Tasks Optimizer.
Some early errors created by Fake Microsoft Security Essentials Alert Trojans during the installation process include:
Microsoft Security Essentials Alert
Microsoft Security Essentials detected potential threats that might compromise your privacy or damage your computer. Your access to these items may be suspender until you take an action.
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can't [sic] guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update the database!
Warning! Running trial version!
The security of your computer has been compromised!
Now running trial version of the software!
Click here to purchase the full version of the software and get full protection for your PC!
Threat prevention solution found
Security system analysis has revealed critical file system vulnerability caused by severe malware attacks.
Risk of system files infection:
The detected vulnerability may result in unauthorized access to private information and hard drive data with a seriuos [sic] possibility of irreversible data loss and unstable PC performance. To remove the malware please run a full system scan. Press 'OK' to install the software necessary to initiate system files check. To complete the installation process please reboot your computer.
After installing Windows System Tasks or another rogue security program, the Trojan will force your PC to reboot. This lets Windows System Tasks launch itself automatically, since Windows System Tasks has Registry entries that slip Windows System Tasks neatly into your default Windows startup routine.
Windows System Tasks may also stay open as a background process even if you attempt to close Windows System Tasks. You can detect less advanced background memory process threats like Windows System Tasks by looking in the Processes tab of your Task Manager.
What Happens Between You, Your PC and Windows System Tasks
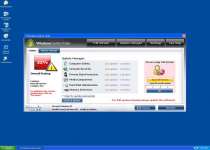
Windows System Tasks may simulate a scan of your PC, but this scan will create fake and negative results that should be ignored. Along with Windows System Tasks's scans, Windows System Tasks can also create fake pop-ups that include but aren't limited to the following:
System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Warning!
Location: [application file path]
Viruses: Backdoor.Win32.Rbot
Warning!
Name: [application file name]
Name: [application file path]
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning.
System component corrupted!
System reboot error has occurred due to lsass.exe system process failure.
This may be caused by severe malware infections.
Automatic restore of lsass.exe backup copy completed.
The correct system performance can not be resumed without eliminating the cause of lsass.exe corruption.
Other symptoms of a Windows System Tasks or Fake Microsoft Security Essentials Alert Trojan infection include browser hijacks, changed homepage settings, altered security settings and disabled applications. Trying to use a disabled program may cause an error to appear that informs you that the program is infected, but the real cause of the disablement is Windows System Tasks.
Preventing Windows System Tasks from running should stop all of these problems. Most Windows users will find Safe Mode to be the easiest option for this, although booting into a non-Windows OS or booting from a CD are also possible solutions. Once Windows System Tasks isn't running you should perform a full system scan with high-quality security application to remove Windows System Tasks and any related infections.
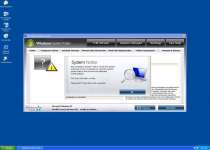
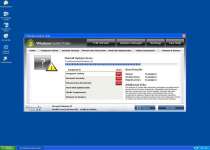
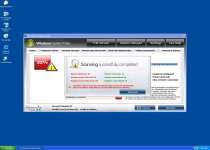
File System Modifications
- The following files were created in the system:
# File Name 1 %UserProfile%\Application Data\Microsoft\[random].exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell "%AppData%\Microsoft\[RANDOM CHARACTERS].exe"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ImageHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY..\..\..\..{RegistryKeys}File Execution Options\afwserv.exe "Debugger" = "svchost.exe'
Additional Information on Windows System Tasks
- The following messages's were detected:
# Message 1 Threat prevention solution found
Security system analysis has revealed critical file system vulnerability caused by severe malware attacks.
Risk of system files infection:
The detected vulnerability may result in unauthorized access to private information and hard drive data with a serious possibility of irreversible data loss and unstable PC performance. To remove the malware please run a full system scan. Press ‘OK’ to install the software necessary to initiate system files check. To complete the installation process please reboot your computer2 System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Warning!
Location: c:\windows\system32\taskmgr.exe
Viruses: Backdoor.Win32.Rbot3 Microsoft Security Essentials Alert
Potential Threat Details
Microsoft Security Essentials detected potential threats that might compromise your private or damage your computer. Your access to these items may be suspended until you take an action. Click ‘show details’ to learn more.4 Warning!
Location: C:\Program Files\java\jre6\bin\jqs.exe
Viruses: Virus.Win32.Sality
Deny – Forbid the execution of potentially harmful software.
Enable Protection – Click to activate antivirus and remove all infections.5 The analysis of system data protection parameters revealed the low security level of system components. Potentially harmful software that may compromise your system integrity has been detected. The structure of some files shows code elements that can be considered as malicious. 6 For full system cleanup please update the software! 7 Caution! Overall system rating is low.
Data execution prevention errors can typically be fixed by reinstalling the problematic software