CryptoWall Ransomware
Posted: May 12, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 11,326 |
| First Seen: | May 12, 2014 |
|---|---|
| Last Seen: | November 26, 2024 |
| OS(es) Affected: | Windows |
 The CryptoWall Ransomware is a file encryptor Trojan that encodes the data of different file types and holds them hostage. The persons responsible for distributing the CryptoWall Ransomware through hacked websites and other methods demand that any victims make a high payment to return the affected files to readability, but malware researchers recommend against this course of action. As opposed to rewarding ill-minded persons for attacking your PC, file backups can let you restore any encrypted files for free, and anti-malware tools, as usual, can remove the CryptoWall Ransomware, albeit not all of the aftereffects of its attacks.
The CryptoWall Ransomware is a file encryptor Trojan that encodes the data of different file types and holds them hostage. The persons responsible for distributing the CryptoWall Ransomware through hacked websites and other methods demand that any victims make a high payment to return the affected files to readability, but malware researchers recommend against this course of action. As opposed to rewarding ill-minded persons for attacking your PC, file backups can let you restore any encrypted files for free, and anti-malware tools, as usual, can remove the CryptoWall Ransomware, albeit not all of the aftereffects of its attacks.
The CryptoWall Ransomware: the Word that's Hot on Blog Sites
The CryptoWall Ransomware has joined the ranks of other, equally prominent Trojans being distributed through hacked WordPress websites, despite the CryptoWall Ransomware also being seen distributed via spam e-mail and other means. The most recent distribution methods redirect the victim's Web browser through a string of other, hacked sites through iFrame vulnerabilities, eventually leading to the Goon Exploit Kit. Because malware experts have seen that attacks for the CryptoWall Ransomware also rotate alternate payloads into use, the installation of the CryptoWall Ransomware is just one of several, potential consequences of these attacks. WordPress site administrators are, once again, reminded that outdated versions of that Web design platform are especially vulnerable to security breaches, inevitably leading to threat distribution.
With its installation proceeding automatically, the CryptoWall Ransomware can then proceed with encrypting various file types on your hard drives, including image files and text documents. The RSA-2048 encryption will prevent these files from being read properly by your computer, making restoring them from a remote backup the simplest solution. However, the CryptoWall Ransomware will display a ransom-themed pop-up demanding hundreds of dollars' worth in BitCoins, ostensibly before the CryptoWall Ransomware will decrypt the files for you. Naturally, malware experts do not encourage this questionable solution, which relies on unreliable persons making good on their word – after already having taken your money.
Taking Back Your Fair Share of a File Ransom
Due to the inevitable and highly disruptive symptoms associated with a successful CryptoWall Ransomware attack, the CryptoWall Ransomware infections usually should be noticed almost immediately. Regardless of the files encrypted by the CryptoWall Ransomware, the CryptoWall Ransomware also will place additional files into the targeted directories that include its ransom instructions, labeled as 'DECRYPT_INSTRUCTION.' However, the CryptoWall Ransomware's delivery and installation methods are presumed to occur without any visible signs.
Besides the ever-important facets of website administrative security that are relevant to stopping the CryptoWall Ransomware's ongoing campaign (which has targeted charitable organizations, along with blogs), PC users also can disable JavaScript in their Web browsers. Doing so will block many of the exploits used to redirect victims to the attack. In cases of confirmed exposure to such a hacked website, malware researchers recommend disinfecting the PC, whether or not any indicators of the CryptoWall Ransomware's attacks are in evidence.
Like other, similar Trojan distribution campaigns, the CryptoWall Ransomware displays clearly that threat attacks have no need to be creative to be successful or threatening in their larceny.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%ALLUSERSPROFILE%\HELP_DECRYPT.URL
File name: HELP_DECRYPT.URLSize: 292B (292 bytes)
MD5: 68bab4a48588991342ca900e7b3db1d8
Detection count: 126
Mime Type: unknown/URL
Path: %ALLUSERSPROFILE%
Group: Malware file
Last Updated: August 11, 2017
onewindow1s.jpg
File name: onewindow1s.jpgSize: 278.01 KB (278016 bytes)
MD5: 845f94f481f32c883692f6c8bb4946cb
Detection count: 90
Mime Type: unknown/jpg
Group: Malware file
Last Updated: July 3, 2015
11a2c84.exe
File name: 11a2c84.exeSize: 220.16 KB (220160 bytes)
MD5: f97d91f8aebbce4628664231184af5a1
Detection count: 84
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: June 12, 2014
%SystemDrive%\22bb2aa7\22bb2aa7.exe
File name: 22bb2aa7.exeSize: 221.18 KB (221184 bytes)
MD5: fc70fcc84636f1ac405e85ab375e6323
Detection count: 82
File type: Executable File
Mime Type: unknown/exe
Path: %SystemDrive%\22bb2aa7
Group: Malware file
Last Updated: June 25, 2015
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\a5b2077d.exe
File name: a5b2077d.exeSize: 262.14 KB (262144 bytes)
MD5: 687d2936249b2ab7387e9336bddf23ef
Detection count: 40
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
Group: Malware file
Last Updated: February 26, 2016
C:\Users\<username>\AppData\Roaming\a5d89829.exe
File name: a5d89829.exeSize: 195.58 KB (195584 bytes)
MD5: edfeb771395e1807109712a2bf158599
Detection count: 12
File type: Executable File
Mime Type: unknown/exe
Path: C:\Users\<username>\AppData\Roaming
Group: Malware file
Last Updated: April 8, 2024
%SystemDrive%\43894dc\43894dc.exe
File name: 43894dc.exeSize: 165.37 KB (165376 bytes)
MD5: 517d709b1b99fa87ddfe61950a93cf5c
Detection count: 9
File type: Executable File
Mime Type: unknown/exe
Path: %SystemDrive%\43894dc
Group: Malware file
Last Updated: June 20, 2014
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\a2f10867.exe
File name: a2f10867.exeSize: 221.18 KB (221184 bytes)
MD5: 7f919abf4c32b34d576c81564045f98b
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
Group: Malware file
Last Updated: July 8, 2015
%APPDATA%\deyct-a.exe
File name: deyct-a.exeSize: 348.16 KB (348160 bytes)
MD5: ce57a4f528ebb078f9bba3e72dc953f1
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: December 8, 2015
%APPDATA%\ivsposkhf2.exe
File name: ivsposkhf2.exeSize: 342.52 KB (342528 bytes)
MD5: 3d238f4934dad0b8724acce5800a5e63
Detection count: 2
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: December 27, 2015
%USERPROFILE%\Documents\qnemvp.exe
File name: qnemvp.exeSize: 393.58 KB (393583 bytes)
MD5: 467dd942e4f3386bb7e8dd309c21d558
Detection count: 2
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Documents
Group: Malware file
Last Updated: March 15, 2016
DECRYPT_INSTRUCTION.html
File name: DECRYPT_INSTRUCTION.htmlMime Type: unknown/html
Group: Malware file
DECRYPT_INSTRUCTION.url
File name: DECRYPT_INSTRUCTION.urlMime Type: unknown/url
Group: Malware file
DECRYPT_INSTRUCTION.txt
File name: DECRYPT_INSTRUCTION.txtMime Type: unknown/txt
Group: Malware file
More files
Registry Modifications
File name without pathDECRYPT_INSTRUCTION.URLINSTALL_TOR.URLRegexp file mask%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\DECRYPT_INSTRUCTION.HTML%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\DECRYPT_INSTRUCTION.TXT%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\HELP_DECRYPT.PNG%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\HELP_DECRYPT.url%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\HELP_YOUR_FILES.PNG%HOMEDRIVE%\out.png
Additional Information
| # | Message |
|---|---|
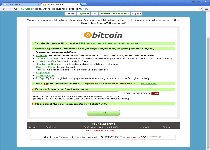
| 1 | Decrypt service Your files are encrypted. To get the key to decrypt files you have to pay 500 USD/EUR. If payments is not made before [date] the cost of decrypting files will increase 2 times and will be 1000 USD/EUR Prior to increasing the amount left: [count down timer] We are present a special software - CryptoWall Decrypter - which is allow to decrypt and return control to all your encrypted files. How to buy CryptoWall decrypter? 1.You should register Bitcoin waller 2. Purchasing Bitcoins - Although it's not yet easy to buy bit coins, it's getting simpler every day. 3. Send 1.22 BTC to Bitcoin address: 1BhLzCZGY6dwQYgX4B6NR5sjDebBPNapvv 4. Enter the Transaction ID and select amount. 5. Please check the payment information and click "PAY". |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.