Fake System Restore
Posted: April 13, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 14 |
| First Seen: | October 6, 2011 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
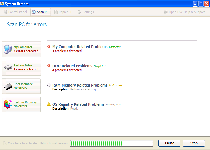 The non-Microsoft rogue defragmenter System Restore is a fake security application used to lure the user into unintentionally becoming the victim of fraud and should not be confused with the Microsoft-based System Restore feature available on all Windows platforms. System Restore and similar threats are known to use Trojans to infect new PCs, a process which may use fake alerts that lead you into thinking that you're installing legitimate software. Browser hijacks and other problems with application usage have been noted on computers infected by Fake System Restore, so you delete System Restore through proper use of anti-malware software as soon as you get the chance.
The non-Microsoft rogue defragmenter System Restore is a fake security application used to lure the user into unintentionally becoming the victim of fraud and should not be confused with the Microsoft-based System Restore feature available on all Windows platforms. System Restore and similar threats are known to use Trojans to infect new PCs, a process which may use fake alerts that lead you into thinking that you're installing legitimate software. Browser hijacks and other problems with application usage have been noted on computers infected by Fake System Restore, so you delete System Restore through proper use of anti-malware software as soon as you get the chance.
System Restore is Another Rogue Infection Cowering Under a Known Brand
Fake System Restore hopes that you'll mistake it for a real System Restore application, since the Microsoft feature of that name is available in any machine that has Windows. The real Windows System Restore, however, only serves as a utility for rolling your operating system state back to a previous and more stable one. The rogue security program System Restore is quite different and will behave in a similar fashion to other rogue defragmenters such as Windows Restore, System Diagnostic, Windows Diagnostic, Windows Tool and WinScan.
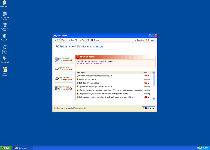
Rogue programs in the System Restore family tend to be distributed by Trojans that first get into your computer through a fake system scan or a browser exploit. Afterward, you may see a message similar to this one:
Windows Diagnostic
Windows detected a hard disk error.
A problem with the hard drive sectors has been detected. It is recommended to download the following sertified [sic] software to fix the detected hard drive problems. Do you want to download recommended software?
If you fall for this trick, you'll end up installing System Restore or a similar PC threat.
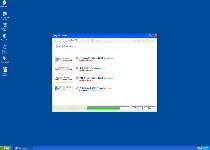
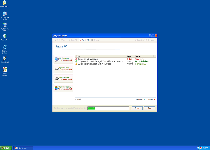
System Restore will immediately show you a large number of system errors whether you want System Restore to do so or not. Some brief examples include:
Windows detected a hard drive problem.
A hard drive error occurred while starting the application.
Requested registry access is not allowed. Registry defragmentation required
32% of HDD space is unreadable
Ram Temperature is 83 C. Optimization is required for normal operation.
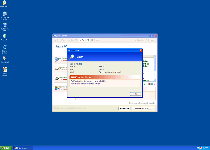
These errors and more like them may initially scare you into thinking about purchasing Fake System Restore to fix the problems. However, all warnings are faked, and in fact, many of them would render the PC completely inoperable if they were true!
Restoring Your System from System Restore
Since System Restore has no real functions that benefit your computer, you should have no problems wanting to delete System Restore, but that's easier said than done. System Restore is known for shutting down anti-malware software and other applications along with displaying the above warnings, and can also hijack your web browser to control which websites you visit or how they're displayed.
Using Safe Mode or a similar alternative startup method will prevent System Restore from launching automatically, in which case the next step is to remove System Restore while System Restore can't interfere. Since System Restore registers .dll files, adds Windows Registry entries, and otherwise is a complicated threat, you shouldn't try to delete System Restore by removing the files one at a time.
It's strongly suggested that you use a reliable anti-malware program and scan your entire PC, since many related Trojans may also need to be removed along with the removal of System Restore. If your anti-malware software is high-quality and completely updated, permanently removing System Restore shouldn't prove to be a challenge.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%ALLUSERSPROFILE%\Application Data\uk64VDsZ0gb.exe
File name: uk64VDsZ0gb.exeSize: 352.25 KB (352256 bytes)
MD5: a7a2361890a50b111748603a2873e431
Detection count: 79
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: October 10, 2011
%ALLUSERSPROFILE%\Application Data\ii664VDsZ0gb.exe
File name: ii664VDsZ0gb.exeSize: 348.16 KB (348160 bytes)
MD5: 36329c82a876e81da915dc9e10020eea
Detection count: 78
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: October 10, 2011
%ALLUSERSPROFILE%\Application Data\eeV664VDsZ0gb.exe
File name: eeV664VDsZ0gb.exeSize: 349.69 KB (349696 bytes)
MD5: fa6524d135d2ae7394d0420b2a0c1b6d
Detection count: 77
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: October 10, 2011
%ALLUSERSPROFILE%\Application Data\3ZV664VDsZ0gb.exe
File name: 3ZV664VDsZ0gb.exeSize: 358.4 KB (358400 bytes)
MD5: 6dbf905c1c5d87c0198e574df1584603
Detection count: 74
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: January 8, 2020
%ALLUSERSPROFILE%\Application Data\6DSS92c31Apgjk.exe
File name: 6DSS92c31Apgjk.exeSize: 358.4 KB (358400 bytes)
MD5: 86de51a43727f5ff214d5ce7b1aa1ae5
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: October 10, 2011
%Desktop%\System Restore.lnk
File name: %Desktop%\System Restore.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Programs%\System Restore
File name: %Programs%\System RestoreGroup: Malware file
%Programs%\System Restore\System Restore.lnk
File name: %Programs%\System Restore\System Restore.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%TempDir%\[RANDOM CHARACTERS]
File name: %TempDir%\[RANDOM CHARACTERS]Group: Malware file
%TempDir%\[RANDOM CHARACTERS].exe
File name: %TempDir%\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%TempDir%\dfrg
File name: %TempDir%\dfrgGroup: Malware file
%TempDir%\dfrgr
File name: %TempDir%\dfrgrGroup: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS]"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS].exe"HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'Yes'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "CertificateRevocation" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnonBadCertRecving" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop "NoChangingWallPaper" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '.zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;.scr;'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer "NoDesktop" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "DisableTaskMgr" = '1'HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "Hidden" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "ShowSuperHidden" = '0'
Additional Information
| # | Message |
|---|---|
| 1 | 1633 MB to be removed for computer performance optimization – Performance Issue |
| 2 | Bad sectors on hard drive or damaged file allocation table – Critical Error |
| 3 | Boot sector of the hard drive is damaged |
| 4 | C:\System32\drivers is damaged. This problem may cause a system failure. |
| 5 | Damaged hard drive clusters detected. Private data is at risk. Restore is required |
| 6 | Data Safety Problem. System integrity is at risk. |
| 7 | Disk drive C:\ is unreadable |
| 8 | Drive C initializing error |
| 9 | Files placement on hard drive is not optimized. Defragmentation is required – Performance Issue |
| 10 | GPU RAM temperature is critically high. Urgent RAM memory optimization is required to prevent system failure |
| 11 | Hard drive and memory errors are detected on your PC. |
| 12 | Hard drive does not correspond to system requests |
| 13 | Hard drive doesn't respond to system commands – Critical Error |
| 14 | Hard drive rotational speed exceeds system limits and may cause a system failure |
| 15 | Hard drive space less than technical limits |
| 16 | Local Disc C:\ is not accessible. Make sure the hard drive is installed and connected correctly. |
| 17 | RAM Memory defragmentation is required. Only 30% of RAM Memory is free to use |
| 18 | RAM Memory temperature 83 C. Optimization is required for normal RAM functioning |
| 19 | RAM memory speed decreased significantly and may cause a system failure |
| 20 | Read time of hard drive clusters less than 500 ms – Critical Error |
| 21 | System files are damaged. System is unstable. |
The system restore program just showed up on my computer
My daughter's laptop has the fake system restore, I tried safe mode but it has disallowed her login password in safe mode ,,, any ideas
just showed up on mine this morning
I use XP Pro SP3 with automatic updates turned on, all my third party programs are also up to date. I use a firewall and have an anti-virus program installed. This malware program got onto my computer via IE8, which is of course a program allowed by the firewall.
I was surfing Google on the morning of the 7th of November 2011 and this nasty little program infected my computer. It had completely crippled it. I WAS NOT downloading anything or looking at porn, just using Google for its intended purpose.
After this rogue program infected and crippled my computer it asked for money to repair it.
It prevented Malwarebytes from running (I already had it on my PC). It also prevented me from re-installing Malwarebytes. Every type of anti-malware program recommended by websites were prevented from being installed.
The only program that did install was SPYBOT SEARCH and DESTROY 1.6.2
I was lucky enough to have access to another PC which I used to download SPYBOT and put it on a USB STICK. SPYBOT then removed some of the infection. Malwarebytes was then able to run and it removed then rest of the infection. I then ran my anti-virus program and it finished off the job.
TIPS.
I disabled the infected PCs internet connection and then opened any folder I could, (this malware seriously affects computer functionality and makes you believe that all of your work has gone, it has not, it is just hidden). Once I managed to open a folder I went to TOOLS then FOLDER OPTIONS and then the VIEW tab. I ticked SHOW HIDDEN FILES AND FOLDERS.
This showed me all my work and computer system folders and programs. This made it much easier to fight this nasty, malicious criminal program.
If you are in the UK please report this to the police. This is fraud and is a crime. I am sure the USA and other countries have similar crime reporting systems.
I hope the above helps someone and remember, when your pulling your hair out and shouting at your PC other victims of this crime are experiencing the same. Together, as members of the HONEST online community, we will beat these criminals and hopefully get them prosecuted – but this can only happen if we help each other and report our experiences to the police.
All the best everyone and remember, don't let the buggers get you down.
Tim
This trojan also hides many of the files on your computer. To show them again. right click on a folder and choose properties. Remove the hidden file checkmark if it is there. If it is absent, mark it hidden, apply to a subfolders also and then reverse the process to show files again.
1.) Use a backup browser such as google chrome Opera, or safari for windows which is unlikely to be broken by the virus OR an alternate computer to obtain Rkill(iexplore version), and Malware Bytes on a flash drive
2.) install and Run rkill (may have to use the iexplore.exe version)
3.) install and Run Malware Bytes
4.) If “start menu” items are missing, a.) right click taskbar, b.) select properties, c.) Click the start menu tab in the pop up, d.)check on the “select the store and display a list of recently opened programs” box, e.) click cutomize and change items you desire displayed from “Don’t display this item” to “Display as link” (for example: control panel, pictures, personal folder, documents)
5.) If your files are missing a.)navigate to the control panel, b.) select “Appearance and personalization” (Control Panel home view) ["Folder options" from "Classic View"], c.) click show hidden files or folders, or click folder options and go to the view tab. d.) under “Hidden files and folders” click “Show hidden files and folders” e.) highlight files and folders you want unhidden (for example: Computer/C:/Users/”yourusernamehere”), rightclick and select properties f.) under the general tab uncheck “Hidden” and “Read-Only” g.) when prompted apply to subfolders and files, h.) go back to folder options and check “Do not show hidden files and folders”
That should pretty much get your computer back to normal. This virus really sucks so good luck.
my pc was infected, november 2,2011 at 16:50 UTC
Evry files disapeared.
But I can save my most important file (in my mail box), using a live cd of Ubuntu 9.10. Ubuntu can see and open all my files.
My system got infected today 🙁
Friends PC got infected yesterday. Mike S instructions worked great except when done, Desktop and tool bar icons were still missing. Most of the programs under All Programs were missing, and the desktop picture was missing. Most program shortcuts were gone or broken. Fortunately there was a very recent system backup point so I ran the real Windows Restore and everything came back. Go to go now.
I put the computer in safe mode with networking and ran "rkill"( free)
You need to run rkill first and do not reboot then scan
Got me on 11/11/11 around 11pm(sounds ominous!). Like a fool I clicked Fix Errors, but damage was already done, so now to try some of the above solutions.
With all the warnings on radio here in Australia, I should have known better, it's so bloody criminal!
How am i suppose to download the rkill if none of my internet browsers will show up?
First looking at System Restore I thought it was honestly a restoring program built into windows. Until it started scanning, I had no idea of it being a fake. I believe you all are missing some registry entries for the fake system restore program. I tried removing but it still loads when starting Windows. Somehow something is still loading into memory. What gives?