Windows Steady Work
Posted: June 20, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 12 |
| First Seen: | June 20, 2011 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
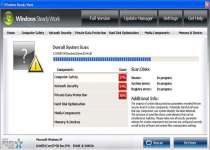 Windows Steady Work is a recent copy of similar rogue security programs that all use fake infection warnings and system alerts to convince you that they're legitimately useful software. Not only does Windows Steady Work lack any ability to detect or remove threats from your PC, Windows Steady Work will attack your computer itself by preventing you from using certain programs and hijacking your browser. Windows Steady Work infections should be removed with the help of an updated and trustworthy anti-virus program, since Windows Steady Work makes Registry alterations and is often accompanied by Trojan threats that will hinder attempts to remove Windows Steady Work by manual methods.
Windows Steady Work is a recent copy of similar rogue security programs that all use fake infection warnings and system alerts to convince you that they're legitimately useful software. Not only does Windows Steady Work lack any ability to detect or remove threats from your PC, Windows Steady Work will attack your computer itself by preventing you from using certain programs and hijacking your browser. Windows Steady Work infections should be removed with the help of an updated and trustworthy anti-virus program, since Windows Steady Work makes Registry alterations and is often accompanied by Trojan threats that will hinder attempts to remove Windows Steady Work by manual methods.
Why You Don't Want Windows Steady Work to Work for You
Even the presence of Windows Steady Work, in the first place, is indicative of another threat aboard and attacking your computer. Almost all Windows Steady Work infections are installed by Trojans like the Fake Microsoft Security Essentials Alert. Fake Microsoft Security Essentials Alert Trojans will use pop-up windows that imitate the Security Essentials Alert interface and warn you about a Trojan threat. Initially, this threat will be identified as an Unknown Win32/Trojan, and later clarified as a Trojan.Horse.Win32.PAV.64.a infection.
A Fake Microsoft Security Essentials Alert Trojan may also create warnings like the following before it installs Windows Steady Work or another rogue security program:
Microsoft Security Essentials Alert
Potential Threat Details
Microsoft Security Essentials detected potential threats that might compromise your private or damage your computer. Your access to these items may be suspended until you take an action. Click 'show details' to learn more.
After this, Windows Steady Work is installed in the form of a fake security program, and your computer is rebooted. Windows Steady Work will run automatically after the reboot, since Registry entries sneak Windows Steady Work right into your standard Windows startup routine.
Windows Steady Work has no real security or threat-combating features, but makes up for this by using large amounts of prefabricated alerts that warn you about fake threats:
System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can't [sic] guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update the database!
System component corrupted!
System reboot error has occurred due to lsass.exe system process failure.
This may be caused by severe malware infections.
Automatic restore of lsass.exe backup copy completed.
The correct system performance can not be resumed without eliminating the cause of lsass.exe corruption.
Warning! Running trial version!
The security of your computer has been compromised!
Now running trial version of the software!
Click here to purchase the full version of the software and get full protection for your PC!
Warning!
Location: [application file path]
Viruses: Backdoor.Win32.Rbot
Warning!
Name: [application file name]
Name: [application file path]
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning.
These errors may also appear when Windows Steady Work blocks a program, not because the program is infected, but because Windows Steady Work doesn't want you to access diagnostic or anti-virus software.
The Rest of Windows Steady Work's Arsenal
Besides launching itself automatically and preventing you from using certain programs, Windows Steady Work can also hijack your web browser. These hijacks can show a large variety of signs, all of which are designed to control your website-viewing habits:
- Your homepage might be changed to a harmful website that's linked to Windows Steady Work. This website can attack your PC with drive-by downloads, and may try to steal personal information like your credit card number.
- Advertisements may appear in pop-up windows or play as sound files, even if you don't have your web browser open.
- You may be redirected to strange websites or have online content altered to show malicious links.
- Fake error pages may appear that tell you that a known to be safe website is unsafe. Windows Steady Work can do this to stop you from visiting anti-virus websites that would give you the advice or a program to remove Windows Steady Work.

File System Modifications
- The following files were created in the system:
# File Name 1 %UserProfile%\Application Data\Microsoft\.exe
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = '0'
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\Microsoft\msotnu.exe
File name: msotnu.exeSize: 1.77 MB (1773056 bytes)
MD5: 01d1de50deecc76596b79a097f50215e
Detection count: 72
File type: Executable File
Mime Type: unknown/exe
Path: %AppData%\Microsoft
Group: Malware file
Last Updated: January 8, 2020
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.