Researcher Stumbles Upon Method to Temporarily Slow Unprecedented WannaCryptor or WanaCrypt0r Ransomware Attacks
 Hundreds of thousands of computers have recently come under a massive attack from what is being touted as an unprecedented ransomware cyberattack that is targeting systems around the world, including various large companies. The cyberattack has literally taken the computer security world by storm and hasn't shown any signs of slowing down in the past few days. Interestingly enough, a British computer researcher accidentally stumbled upon a "kill switch" to essentially stop the attack temporarily.
Hundreds of thousands of computers have recently come under a massive attack from what is being touted as an unprecedented ransomware cyberattack that is targeting systems around the world, including various large companies. The cyberattack has literally taken the computer security world by storm and hasn't shown any signs of slowing down in the past few days. Interestingly enough, a British computer researcher accidentally stumbled upon a "kill switch" to essentially stop the attack temporarily.
Matt Suiche, the founder of a cybersecurity company in the United Arab Emirates, told ABC News over the weekend that there is a reason for the recent slow-down of the massive ransomware attack. Suiche explained, "Currently the spreading of the ransomware is slowed down dramatically because a researcher found a logic bug in the malware, not because the companies around the world are having good security practice."
While many major companies, government entities, transportation systems, and hospitals have been targeted in the ransomware attack, many of them experienced issues with their Windows-based systems. Some companies, such as FedEx, have implemented various steps to keep their systems going even if it meant isolating the use of many of their Windows-based computers, which some companies have done thus far.
The spread of what is being called an outbreak of the 'WannaCry' malware, also known as WanaCrypt0r, WannaCryptor, WCry, or WNCry, is vast and has reached what the European Cybercrime Center says is "an unprecedented level." The attack has reached as many as 99 countries around the world and over 75,000 verified attacks, according to the security firm Avast.
Avast said in a statement, "According to our data, the ransomware is mainly being targeted to Russia, Ukraine and Taiwan, but the ransomware has successfully infected major institutions, like hospitals across England and Spanish telecommunications company, Telefonica."
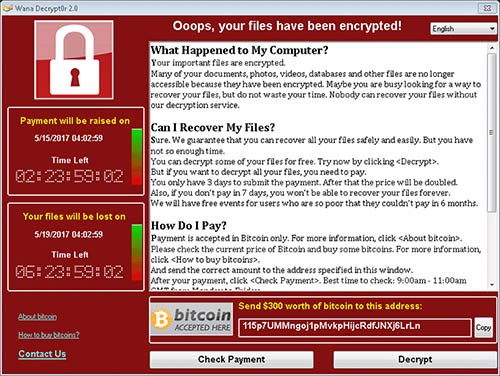
What the attack is doing on affected systems is performing a well-known tactic that ransomware has been doing for many years now. It first infects a system through an unconventional method, mostly spread by spam email attachments or hacked web sites that offer downloads. Upon infection, the malware will display a notification demanding payment, sometimes with a time limit. The ransom demanded is usually around $300 or more. Those who opt to pay the ransom may or may not receive the proper instructions or code to restore their infected PC back to normal operation, which makes the WannaCryptor ransomware so dangerous and destructive.
Example of WanaCrypt Ransomware lock screen notification of encrypted files
So far, law enforcement agencies tracking the WannaCryptor malware have not identified the perpetrators. The forensic work to identify them is said to take some time, and some have already suspected that a private or state attacker could be behind the threat. In the past, we have found that ransomware attacks on a large scale are usually carried out by cybercrook groups instead of individuals. However, authorities and experts will reserve their opinions until the facts of the attack are discovered and verified.
The efforts to find the perpetrators behind the attack and at the same time put a stop to the spread of the attack will be an ongoing effort by authorities in many countries. The method for temporarily slowing the spread of WannaCryptor is just that, temporary. There will be no premature celebrations of bringing WannaCryptor to a crawl until it is stopped dead in its tracks. Until then, companies and computer users are urged to be cautious as it is expected that this attack and future ones will continue to propagate.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.