FBI Ultimate Game Card Virus
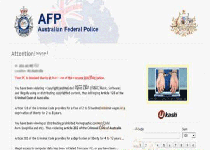
 FBI Ultimate Game Card virus is a ransomware Trojan derived from the same family as the Celas Trojan , the Gema 'Access to your computer was denied' Virus , the SIAE Virus , et al. Other than being retooled to target residents of the United States, the FBI Ultimate Game Card virus is the same as the other members of its family and will block your PC with fraudulent legal authority while FBI Ultimate Game Card claims that you've committed online crimes that call for a financial penalty....
FBI Ultimate Game Card virus is a ransomware Trojan derived from the same family as the Celas Trojan , the Gema 'Access to your computer was denied' Virus , the SIAE Virus , et al. Other than being retooled to target residents of the United States, the FBI Ultimate Game Card virus is the same as the other members of its family and will block your PC with fraudulent legal authority while FBI Ultimate Game Card claims that you've committed online crimes that call for a financial penalty....