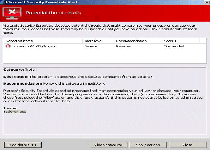
‘Windows Genuine Advantage’ Trojan Ransomware
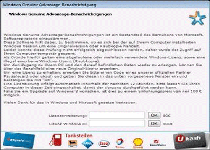 'Windows Genuine Advantage' Trojan Ransomware is a clone of the West Yorkshire Ransomware , ' Votre ordinateur est bloqué' Belgium Ransomware and related ransomware Trojans, and uses an updated hoax for German Windows users but, otherwise, the same basic attacks against your PC – including displaying a fake pop-up alert that blocks your ability to use other programs. 'Windows Genuine Advantage' ransomware may also take additional measures to encrypt media files and make them unusable. While...
'Windows Genuine Advantage' Trojan Ransomware is a clone of the West Yorkshire Ransomware , ' Votre ordinateur est bloqué' Belgium Ransomware and related ransomware Trojans, and uses an updated hoax for German Windows users but, otherwise, the same basic attacks against your PC – including displaying a fake pop-up alert that blocks your ability to use other programs. 'Windows Genuine Advantage' ransomware may also take additional measures to encrypt media files and make them unusable. While...