Trojan.Shylock.B
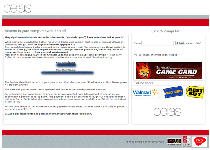
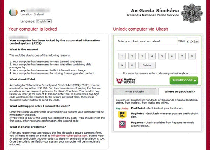
Trojan.Shylock.B is a Trojan that opens a back door on the affected computer and aims at stealing personal information. Trojan.Shylock.B spreads by exploiting the Oracle Java SE Rhino Script Engine Remote Code Execution Vulnerability (CVE-2011-3544) and Oracle Java SE Remote Java Runtime Environment Code Execution Vulnerability (CVE-2012-0507). Once executed, Trojan.Shylock.B creates the certain file. Trojan.Shylock.B then opens a back door and connects to the command-and-control (C&C)...